
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

The Menlo Labs research team recently analyzed a phishing case where the threat actor was using the data to commit identity fraud. Menlo Labs was able to track a threat actor using the XBALTI phishing kit as he stole victim information and used it to file for fraudulent unemployment claims and COVID relief aid.
In this case, we’ll look at the XBALTI phishing kit. The XBALTI phishing kit is a commonly used phishing kit with a few target themes (Amazon and Chase Banking). Our threat actor used the Chase Banking theme.
The phishing kit is made up of a couple of files that work together to steal victim data. After the collection, the kit exfiltrates the data to the threat actor. The actor will have access to an admin panel to access the stolen data and/or can also have the information emailed to themselves. Below, we've provided an analysis of this phishing kit.
Example 1:
Analyst comment: this information is likely to change (source: https://scammer.info/t/xbalti-phishing-kit-amazon-and-chase/78691)

Example 2:
(source: https://blog.medarkus.net/2020/10/11/XBALTI-Kit.html)

Admin panels:
The XBALTI admin panel provides the threat actor with pages to see viewers, Social Security numbers, dates of birth, as well as multiple email and credit card pages.


Landing pages:
Landing pages are custom websites that mimic the target company in order to trick victims into sharing their information with the site.

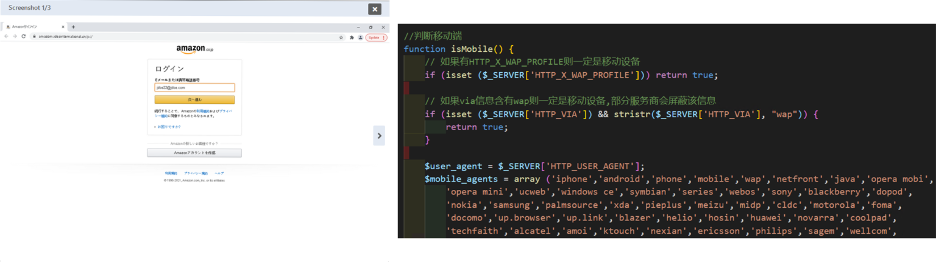
Information stealing pages:
These pages are designed to look like legitimate secure login pages; however, these companies normally won’t ask for customers to provide personal information to log in, such as what these pages are asking for.


Amazon will not ask for updated payment information in order to access your account. Users should be very careful of these types of details.




Credentials:
The phishing kit compromises victim credentials, but it’s also hard-coded with the threat actor’s own email and password. This opsec fail exposes the threat actor’s own personal information. It’s set up this way so the stolen information can be directly sent to the threat actor’s email address.

Now that we’ve had a look at the phishing kit, we’ll talk about the threat actor.
The threat actor used the phishing kit, and possibly other tactics, to collect personal information from victims. Menlo Labs was given access to insider information from the threat actor email, in which we could see emails from XBALTI that appeared to be test logs. The actor used the following phishing link: https[://]topwaterproofcamera[.]com/chase./secure/XBALTI/send.php.


With the information the actor collected from victims, we know he attempted to create loan applications. He also opened bank accounts under the assumed name.

At first, not everything worked right. The bank sent the card to the wrong address, sending it to the victim and not to the actor. This is just one of the fake addresses the actor uses. It’s possible that he has mules who will pass the money forward or he knows the people at the address.

He also set up a Cash App account using his real first name and the assumed last name. We assess, based on the transactions, that there may be other scams the actor is involved in. We also noticed that he seems to send little sums of money and receive bigger sums of money from some possible victims who may not know they are mules.


The threat actor also sets up a crypto currency wallet.


The fraudster went on to attempt to take out COVID relief loans and FEMA disaster relief, as well as apply for unemployment benefits.



Menlo Labs worked with the appropriate law enforcement agency and turned this threat actor in. We assess this was a low-level actor who does not pose a greater risk.
https[://]topwaterproofcamera[.]com/chase./secure/XBALTI/send.php
The following rules were sourced on GitHub and were tested in VirusTotal.
rule PK_Amazon_xbalti : Amazon
{
meta:
description = "Phishing Kit impersonating Amazon"
licence = "GPL-3.0"
author = "Thomas 'tAd' Damonneville"
reference = ""
date = "2021-08-11"
comment = "Phishing Kit - Amazon - 'BY XBALTI'"
strings:
$zip_file = { 50 4b 03 04 }
$spec_dir = "XBALTI"
$spec_dir1 = "amazon"
$spec_file1 = "rezulta.php"
$spec_file2 = "check_bin.php"
$spec_file3 = "send_billing.php"
$spec_file4 = "antibots.php"
condition:
uint32(0) == 0x04034b50 and
$zip_file and
all of ($spec_dir*) and
// check for file
all of ($spec_file*)
}
rule PK_Apple_xbalti : Apple
{
meta:
description = "Phishing Kit impersonating Apple"
licence = "GPL-3.0"
author = "Thomas 'tAd' Damonneville"
reference = ""
date = "2020-12-16"
comment = "Phishing Kit - Apple - 'BY XBALTI'"
strings:
$zip_file = { 50 4b 03 04 }
$spec_dir = "XBALTI"
$spec_file1 = "yassin.css"
$spec_file2 = "Congratulation.php"
$spec_file3 = "Secure.php"
$spec_image1 = "img/Apple_logo_grey.svg"
condition:
uint32(0) == 0x04034b50 and
$zip_file and
$spec_dir and
// check for file
all of ($spec_file*) and
any of ($spec_image*)
}
rule PK_Chase_Xbalti : Chase1
{
meta:
description = "Phishing Kit impersonating Chase bank"
licence = "GPL-3.0"
author = "Thomas 'tAd' Damonneville"
reference = ""
date = "2019-12-29"
comment = "Phishing Kit - Chase Bank - XBalti"
strings:
// the zipfile working on
$local_file = { 50 4b 03 04 }
// specific directory found in PhishingKit
$spec_dir = "XBALTI"
// specific files found in PhishingKit
$spec_file = "chasefavicon.ico"
$spec_file2 = "Email.php"
condition:
// look for the ZIP header
uint32(0) == 0x04034b50 and
$local_file and
$spec_dir and
$spec_file and
$spec_file2
}
rule PK_Chase_Xbaltiv3 : Chase
{
meta:
description = "Phishing Kit impersonating Chase bank"
licence = "GPL-3.0"
author = "Thomas 'tAd' Damonneville"
reference = "https://stalkphish.com/2021/04/22/scammer_vs_scammer_backdoored_phishing_kit/"
date = "2021-04-21"
comment = "Phishing Kit - Chase Bank - XBalti V3"
strings:
// the zipfile working on
$local_file = { 50 4b 03 04 }
// specific directory found in PhishingKit
$spec_dir = "XBALTI"
// specific files found in PhishingKit
$spec_file = "desktopnight.jpeg"
$spec_file2 = "lostyle.css"
$spec_file3 = "Email.php"
condition:
// look for the ZIP header
uint32(0) == 0x04034b50 and
$local_file and
$spec_dir and
all of ($spec_file*)
}
Menlo Security
