
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

Phishing is a type of cyber attack. Attackers use deceptive techniques to trick users into revealing sensitive information, downloading malware, and exposing themselves or their organizations to cybercrime risks.
Phishing attacks are the most common type of social engineering and can happen through web, email, text, or phone calls. They involve tricking people into giving information or assets to the wrong people. Social engineering attacks rely on human error and pressure tactics in an effort to divulge sensitive information such as passwords, credit card numbers and other personal information.
The attacker typically masquerades as a person or organization the victim trusts—e.g., a coworker, a boss, a company the victim or victim’s employer does business with—and creates a sense of urgency that drives the victim to act rashly. Threat actors and fraudsters use these tactics because it’s easier and less expensive to trick people than it is to hack into a computer or enterprise network.
In fact, the most common initial attack vector for data breaches worldwide is phishing, responsible for 16% of global data breaches, according to the IBM Cost of a Data Breach Report 2023.
Phishing attacks can pose a significant threat to enterprises, and it's crucial to be cautious reading unsolicited emails, messages, or requests for personal information. These attacks work by exploiting human trust and tricking individuals into revealing sensitive information. Here's a typical overview of how a phishing attack works:
Attackers identify an intended target based on their level of access to sensitive information or systems and create a fake identity to initiate communication.
Attackers are compromising known trusted sites or designing fake URLs that closely resemble legitimate ones in order to capture login credentials or other sensitive information. Phishing attempts can also be delivered through emails, SMS, or even phone calls usually containing urgent or enticing language to take immediate action.
Attackers will try to create a sense of urgency or fear to pressure the target into taking quick action and exploit trust by impersonating entities the target is likely to trust with familiar logos and messaging.
Many people click on links in phishing messages. They then provide personal information such as passwords, credit card information, or social security numbers. This information is given to potentially harmful websites.
Attackers will use stolen information to access user's systems, corporate accounts, and enterprise networks without permission. They will then commit identity theft, financial fraud, or other malicious actions.
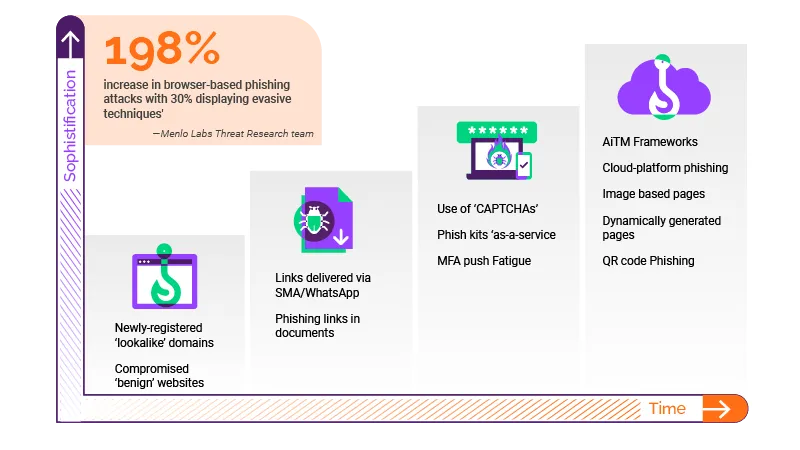
Attackers have created a variety of evasive techniques used in today’s phishing attacks to evade commonly deployed security tools such as Secure Web Gateways, Firewalls and Endpoint Security. Some of these evasive phishing techniques include man-in-the-middle attacks, multi-factor authentication bypass, legacy URL reputation evasion, SEO poisoning and using legitimate cloud-sharing services.
A Man-in-the-middle attack is an attack where unauthorized 3rd parties intercept and alter the communication between two parties without their knowledge in an attempt to capture sensitive information like login credentials or session tokens, allowing attackers to impersonate the user or gain unauthorized access.
An MFA bypass attack is specifically used by cybercriminals to avoid or circumvent MFA tools in order to gain access to user accounts. These techniques bypass security measures such as unique passwords, digital tokens, and biometric authentication. They enable unauthorized access to important information and systems. They exploit trust in SSO platforms, like Okta, LastPass, and OneLogin, to gain unauthorized access to multiple services.
Threat actors capitalize on this technique by hijacking trusted sites, or by creating a new site and leaving it dormant until its URL/domain is trusted. They then use these URLs and destination sites to launch phishing attacks. The user opens the web URL believing it to be authentic, and because the URL is in a safe category, it is not blocked by web filters. Either malware subverts the user or the user willingly enters credentials for a credential theft attack.
This commonly known URL evasion technique is used to manipulate search engine results in order to drive traffic to malicious websites. The attackers exploit the algorithms of search engines to promote their own content, often containing malware or phishing schemes.
Attackers will use cloud-sharing platforms such as Gdrive or Box with trusted domains in order to avoid detection. These have become lucrative phishing avenues for threat actors for hosting malicious content or password protected files in credential phishing campaigns.
The browser has become the most widely used enterprise application as business users spend more than 75% of their working day inside web browsers according to Forrester. As a result, attackers have become hands on crafting their attacks. They have evolved their social engineering techniques to specifically target the browser and employ evasive techniques designed to bypass commonly deployed security tools.
Enterprise security faces a challenge because security tools still depend on traditional network signals like Firewalls and Secure Web Gateways. These tools do not offer insight into specific browser behaviors, which means they cannot detect evasive phishing threats. Network and endpoint security tools such as firewalls, SWG, and URL reputation checks are unable to detect previously unseen phishing attacks because there is no signature or indicator of compromise (IOC) available to indicate that an endpoint or network may have been breached at that specific moment in time.
Even AI models trained on network-based telemetry fall short. While they derive their strength from robust datasets, their effectiveness lacks insight into specific browser behaviors. This forces IT and security teams to rely on network-based signature detection approaches, which can only identify known threats, and fail to block evasive phishing threats targeting the browser.
As a consequence, these novel phishing attacks have become the tool of choice for attackers attempting to penetrate enterprise networks. Even platforms like VirusTotal, which inspect items from over 70 of the world’s largest antivirus scanners and URL/domain blocklisting services, fail to flag evasive URLs and domains in sophisticated phishing. This indicates that there is a clear need for improved visibility, enhanced security controls, and better protection from threats directly within the browser.
Browser Security white paper
To make matters worse, easily accessible phish kits (PhaaS) and ransomware-as-a-service kits (RaaS) today have simplified the process of launching sophisticated phishing attacks. These tools serve as comprehensive toolkits to empower attackers to accelerate their phishing campaigns. Generative AI tools like ChatGPT, have significantly reduced the barriers for attackers to launch more sophisticated and successful phishing campaigns. Attackers can produce thousands of phishing attacks with new threat signatures and fewer errors of common tell tale signs, all in a matter of minutes, posing an even greater threat to enterprises.
They contain pre-packaged resources and provide attackers with the necessary tools such as pre-made templates and scripts to craft and effectively execute their malicious campaigns. These toolkits also make it easier for rudimentary attackers to create convincing and fraudulent websites or emails for the purpose of stealing sensitive information from its intended victims.
The increase in remote work has significantly increased the attack surface for cybercriminals. Successful phishing attacks can lead to loss of confidential information, identity theft, data breaches and large scale financial loss for individuals and corporations.
Due to the seriousness of these attacks and public disclosure requirements for data breaches, phishing attacks can cause significant reputational damage, loss of trust among supply chain partners and even regulatory issues for many businesses. For these reasons, phishing attacks pose a significant risk to individuals and businesses and therefore it is crucial to stopping these attacks before they gain access to user systems and enterprise networks.
Furthermore, cybercriminals have the ability to also disclose or sell stolen information across the dark web, requiring certain government intervention which can sometimes bring heavy fines or other sanctions.
The browser is the business application enterprises can’t live without, but it has fallen behind from a security perspective.
While web, email, and endpoint security do screen out some phishing attempts, the browser remains critically exposed to evasive phishing attacks. Existing enterprise security solutions, which rely heavily on known threat signatures or AI trained on network telemetry, continue to fall short in preventing the latest phishing threats and evasive techniques being used. This proves that existing defenses aren’t getting the job done, and that the browser remains the single greatest entry point for attackers and that we have to make a change.
Browser security offers the most effective phishing countermeasures against today’s sophisticated phishing attacks by delivering comprehensive visibility into every browser session. This provides IT and security teams with actionable threat intelligence inside the browser enabling dynamic policy enforcement for zero-hour phishing, malware, and ransomware attacks targeting the browser. This allows IT and security teams to gain context-rich, actionable insights into browser-based threats that often remain hidden from other security solutions.
Other common steps that can help mitigate phishing threats include:
Menlo Security eliminates phishing attacks and reduces the browser attack surface with our Secure Cloud Browser by allowing enterprise security teams to properly manage their existing browsers, protect their users, and secure application access. Menlo Security’s Browser Security solution is the only solution able to identify and dynamically stop evasive malware, zero-day web exploits and phishing attacks.
In fact, Menlo Security is able to identify and block phishing attacks 6 days ahead of any other security vendor by using our AI powered browser security solution. This ‘protection buffer’ significantly decreases the time between a user’s first access to a malicious site and the point at which one or more vendors on VT flag it as malicious.
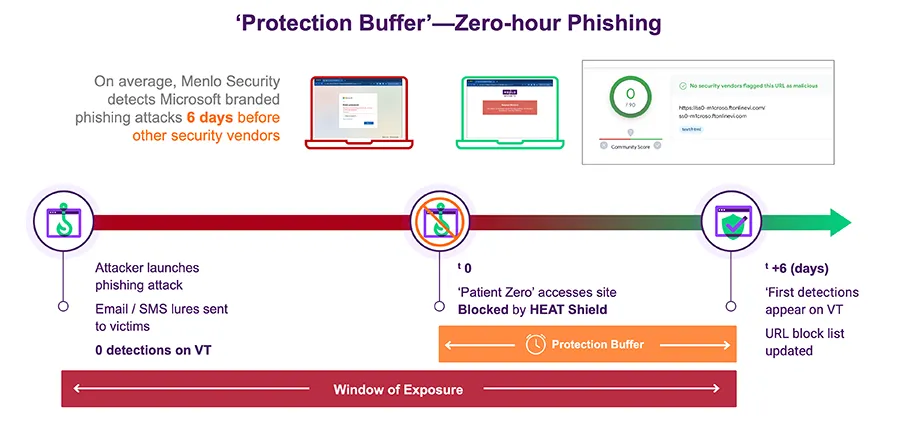
Menlo Security’s Browser Security solution works across any device, providing end-to-end visibility into every browser session. It delivers real-time dynamic policy control to effectively stop evasive malware and zero-hour phishing attacks from infecting user systems and enterprise networks.
Browser Security solutions