
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

Ransomware is becoming more pervasive due to its increasing profitability for cybercriminals. This growth is facilitated by the widespread use of cryptocurrency for anonymous payments, a growing attack surface, and the continuous evolution of sophisticated ransomware techniques including double extortion tactics.
Ransomware is a type of malware that encrypts a targeted victim's data, files, devices, or systems, rendering them inaccessible. This type of attack effectively holds the victim's data hostage until a ransom is paid in exchange for decryption keys that restore access to compromised systems. In the first half of 2023, ransomware attackers extorted $176 million more than the same period in 2022, putting 2023 on track to be the second-costliest year for ransomware in history according to the Chainalysis Mid-year Update.
Ransomware attacks can hamstring business processes, leaving organizations and users without the data they need to operate and deliver mission-critical services. Double extortion ransomware has become increasingly popular with ransomware groups such as Play Ransomware who use double-extortion tactics to target wide ranges of businesses and critical infrastructure organizations across North America, South America, Europe, and Australia. With double extortion ransomware, victim’s sensitive data is first stolen, then encrypted, giving cyber criminals the option of demanding two separate ransom payments. Any enterprise that directly holds significant amounts of client, supplier or even partner data is vulnerable to double extortion tactics. As hybrid work and increased browser usage become the new normal, security teams have realized the importance of establishing proper safeguards and implementing best practices to protect the most critical business tool in the enterprise arsenal from ransomware attacks.
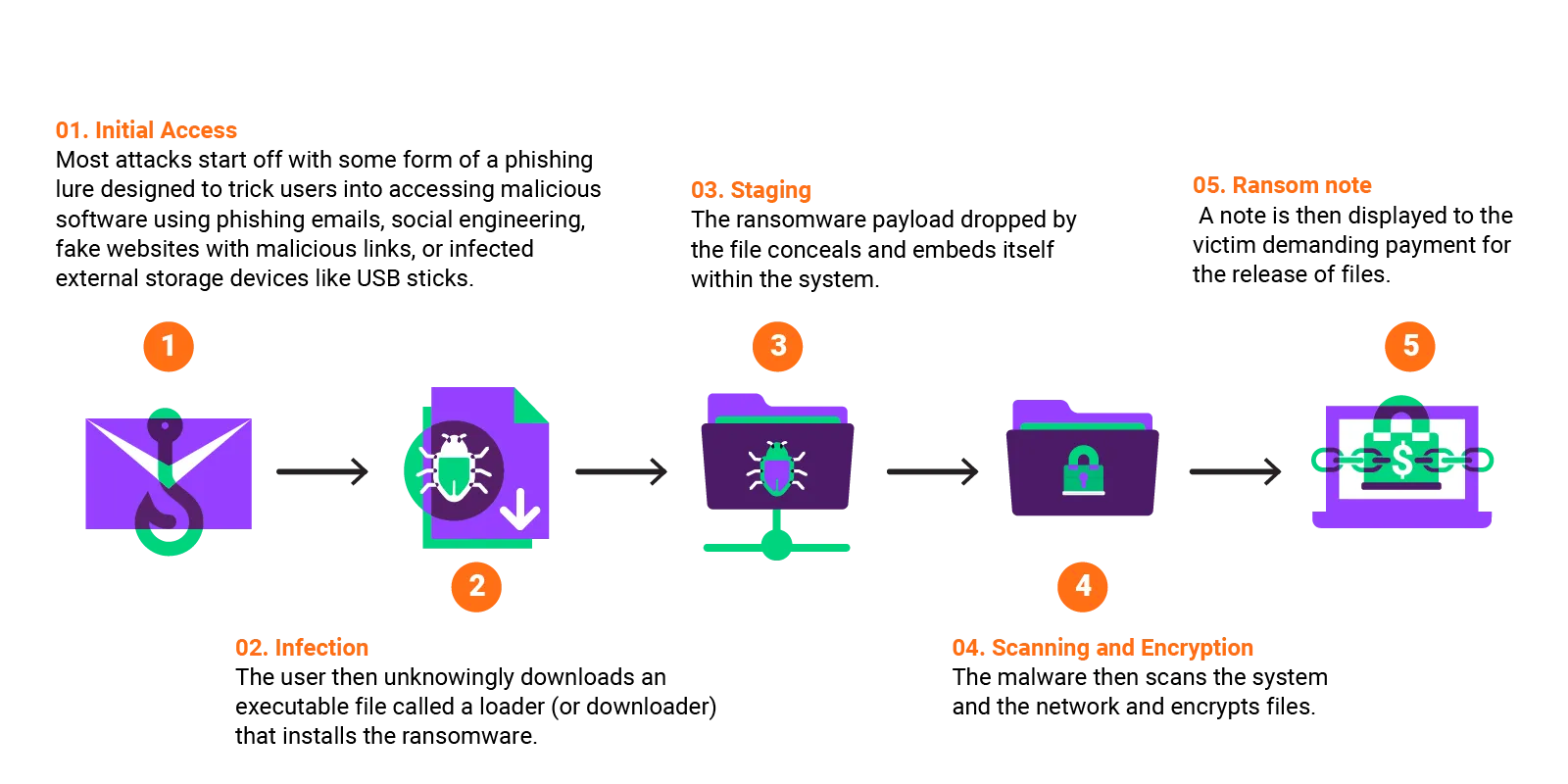
Over time, ransomware has evolved from single ransom demands to more pervasive and destructive attacks, resulting in double-extortion tactics and pressuring victims to pay substantially more by threatening the release of stolen data. The economic and reputational impacts of these ransomware attacks can be devastating. Each stage of a ransomware attack can be interpreted differently, but if we look at a simplified version of a ransomware attack, it can be broken down into five stages: initial access, infection, staging, scanning/encryption, and ransom note.
Before an attacker can demand a ransom, attackers must first infiltrate their victim’s system and infect them with malware. Attackers will start by performing reconnaissance on their intended targets, look for vulnerabilities to exploit, such as phishing attempts, credential abuse, or unpatched software, and then employ evasive techniques to gain initial access onto the endpoint.
Once initial access has been made, attackers will deploy various malware and download tools to search for data, steal credentials, and monitor communication channels across the network with the goal of compromising as many machines as possible.
A command-and-control (C2) server is set up by the attackers to send encryption keys to the target system, while installing additional malware to help facilitate other stages of the ransomware lifecycle.
This step involves the attacker scanning for information about the victim’s network and spreading the infection laterally across additional machines to elevate their access privileges in search of more valuable data. In this stage, attackers also exfiltrate data to the C2 server for double-extortion tactics down the line. Attackers then encrypt the data and systems using the keys sent from their C2 server.
The attackers demand a ransom payment, and the enterprise is left with a tough decision to pay in the hope of recovering the files immediately or reject paying the ransom and begin the process of rebuilding systems and gathering data from the ground up.
Ransomware attacks are growing more successful in breaching enterprise networks due to more targeted surveillance methods used to identify the intended victim and by using evasive techniques to successful gain initial access. Once an attacker has gained access, malicious actors can move laterally across the network and start to extract data — whether it’s logging keystrokes or exfiltrating files or data. Then, once all the value is extracted, systems are locked down and held for ransom.
Depending on the type of ransomware attack and the attacker’s motive, the consequences of ransomware can range from minor inconveniences to critical business shutdowns. And while certain industries may seem less prone to attacks, no one is immune to a ransomware attack. The increase in remote work has also significantly increased the attack surface for cybercriminals, making it easier to identify victims and target enterprises with poor browser security controls. Successful ransomware attacks can lead to loss of confidential information, identity theft, data breaches, and large-scale financial loss for individuals and corporations.
Due to the seriousness of these attacks and public disclosure requirements for data breaches, ransomware attacks can cause significant reputational damage, loss of trust among supply chain partners, and even regulatory issues for many businesses. Ransomware actors today have become more aggressive by using complex delivery systems, and they have become more discerning in their attacks, targeting critical business functions using common ransomware techniques such as:
An attacker will lock users out of all their data or systems until a ransom has been paid.
An attacker attempts to steal data and then threatens to make it public across the internet or sell it on the dark web as a way to up the ante, making the victim more inclined to pay.
Poses as malware, but actually erases data from a victim’s systems even if a ransom is paid.
Involves an attacker encrypting data and exfiltrating it to potentially extort victims into paying a ransom twice.
In addition to financial losses, successful ransomware attempts can lead to damaged business reputations, decreased employee morale, loss of customer trust and loyalty. A successful attack can even cause organizations to become targets for future attacks. In fact, the total cost of a ransomware attack can far exceed the ransom price tag itself, according to IBM's Cost of a Data Breach Report 2023, with the average dollar amount attached to a ransomware attack at $5.13 million, an increase of 13% over the previous year — and that doesn't even include the cost of the ransom payment. Cyber insurance can lessen the financial burden of a ransomware attack, but only to an extent and often does not cover intangible costs.
Initial access brokers (IABs) and ransomware-as-a-service (RaaS) kits have simplified the process of launching sophisticated phishing attacks. IABs are threat actors that specialize in infiltrating computer systems and networks, then selling that unauthorized access to other malicious actors. IABs are skilled at identifying and exploiting security vulnerabilities, providing services to ransomware groups and other bad actors.
RaaS kits have also become widely accessible, significantly lowering the bar for rudimentary threat actors and IABs to create convincing and fraudulent websites or emails for the purpose of stealing sensitive information from their intended victims. These toolkits contain pre-packaged resources and provide attackers with necessary tools, such as pre-made templates and scripts, to craft and effectively execute their malicious campaigns. The price of RaaS kits ranges from $40 per month to several thousand dollars – trivial amounts, considering that the average ransom demand in 2021 was $6 million. A threat actor doesn’t need every attack to be successful to become rich.
Browser Security white paper
The only way to effectively stop ransomware is to prevent the malware incursion altogether, before the attackers gain initial access to a victim’s system or network. If enterprise defenses detect these evasive threats in their earlier stages, they can prevent these attacks from ever reaching the endpoint.
While web, email, and endpoint security do provide some protection against initial access attempts, the browser remains critically exposed to evasive ransomware attacks. Existing enterprise security solutions, which rely heavily on known threat signatures or AI trained on network telemetry, continue to fall short in preventing modern ransomware attacks and the latest evasive threats being used. They leave the browser unprotected, making it the single greatest entry point for modern attacks. We have to make a change.
Browser security offers the most effective ransomware protection strategy against today’s sophisticated ransomware attacks by delivering comprehensive visibility and dynamic policy control into every browser session. Browser security provides IT and security teams with actionable threat intelligence inside the browser, enabling dynamic policy enforcement for zero-hour phishing, malware, and ransomware attacks targeting the browser. This intelligence allows IT and security teams to gain context-rich, actionable insights into browser-based threats that often remain hidden from other security solutions.
Other common hygiene habits that can help mitigate the risk of ransomware include:
The Menlo Security Secure Cloud Browser eliminates ransomware and reduces the browser attack surface, allowing enterprise security teams to properly manage their existing browsers, protect their users, and secure application access. Secure Cloud Browser is the only solution able to identify and dynamically stop evasive malware, zero-day web exploits, and ransomware attacks. The solution works across any device and any browser, providing end-to-end browsing visibility and delivering real-time dynamic policy control to stop evasive malware and zero-hour phishing attacks from infecting user systems and enterprise networks.
To learn more about evasive ransomware and how enterprises can use browser security to eliminate the browser attack surface, visit the Evasive Ransomware solution page.