
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

Security beyond the network. Zero Trust Access delivers comprehensive zero trust for your entire digital ecosystem.
It’s important to note that zero trust is not a solution. It’s not a tool. It’s not something you can buy in a box or download and deploy on your network. Zero trust is a state of mind. A zero trust security strategy assumes that all traffic–regardless of whether it originates from a trusted source – is untrustworthy. This forces web sites, web apps, Software-as-a-Service (SaaS) platforms and even email content to be treated as if it is malicious. It then needs to be authenticated continuously, before each interaction with a user, device or application on the network.
Zero trust turns the traditional detect-and-remediate approach to cybersecurity on its head. Instead of trusting everything except for known threats, zero trust assumes that all traffic – regardless of whether it originates from a trusted source – is untrustworthy. This forces web sites, web apps, Software-as-a-Service (SaaS) platforms and even email content to be treated as if it is malicious. It then needs to be authenticated continuously, before each interaction with a user, device or application on the network.
Traditional security strategies are built to authenticate entities (a user, device or application) once at the edge of the network and then give them access to everything inside the network. This worked well when enterprise networks were set up in a hub and spoke model where there was little mobility. Users tended to log in from corporate headquarters behind a robust firewall that could control traffic flowing in and out of the data center.
Today’s networks, however, are highly-distributed and mobile. Users, devices, apps and data are spread out across private and public cloud infrastructures where they are spun up and down on demand. This decentralized architecture hasn’t so much eliminated the perimeter as it has expanded it to anywhere users do business – whether it is a remote office, a home office, a customer site or on the road. The perimeter is everywhere – making it impossible to stop breaches. Zero trust, on the other hand, continuously authenticates entities at the perimeter and inside the network, ensuring that nothing gets through the cracks.
A zero trust security strategy begins with no access as the default. No user, device or application – regardless of location or status – can access anything without being granted access and authenticated first. From there, access has to be earned through continuous authentication. This prevents a malicious actor from getting access to an end device and then spreading through the network in search of a more valuable target.
Accelerated digital transformation has pushed everything out the edge of the network. Modern applications are no longer monolithic stacks in a single data center. They’re now split up into thousands of microservices spread out across multiple cloud infrastructures. This improves application experience and enables business agility, but it has essentially broken traditional security strategies that were built for the hub and spoke model where security is attached to static infrastructure. The new, modern way of working needs a modern security approach–and zero trust is ideal for securing users, devices, applications and data in the multi-cloud world.
Secondly, the threat landscape has evolved and grown tremendously over the past several years. Enterprises are sending usernames, passwords and multifactor authentication tokens all around the Internet, providing more opportunity for an attacker to intercept and steal those credentials. Enterprises are also sharing resources with the general public, and, therefore, malicious actors. The CEO of a Fortune 50 company likely has a Microsoft 365, Google Productivity Suite or Box account. So, too, does every hacker. It’s fairly easy to spin up a legitimate-looking email communication to trick a user into giving way credentials. Zero Trust stops lateral movement and safeguards other applications inside the network.
It’s important to note that zero trust is not a solution. It’s not a product. It’s not something you can turn on and off. Zero trust is a mindset that needs to be implemented throughout the organization from the management team to the IT team to individual users. It requires a complete re architect of your network.
The first step for implementing zero trust is to know what resources you have and who needs to connect to them. This catalog serves as a trusty road map for granting authentications. What applications do you have? Who needs access? How do you request and get access? What kind of access does each user need? Read only? Read/write? What behaviors are allowed and what should be blocked? Knowing the answers to these questions allows you to build rules around zero trust security that can be implemented effectively.
A clientless approach that goes through the browser allows you to extend control to devices that you don’t manage – including personal devices, partners, customers and other third parties. Some applications will continue to require an agent–and that’s fine. But starting with a clientless by default approach to zero trust eliminates these gaps and allows you to offload a lot of bandwidth off your VPN onto the public Internet – which improves performance and lowers networking costs.
Zero Trust isn’t just about the user and their device. It’s about application to application connectivity. It’s about data. It’s about IoT devices. It’s about external collaborators, All these entities need to be who they say they are and have a legitimate reason for connecting to each other and the network.
Today’s applications – whether they are Microsoft 365 or Salesforce – require continuous connectivity to enable real-time collaboration. Someone makes an update to a customer record or edits a shared document, every users’ view is reflected in real time. As you make the shift to zero trust, you need to put in place a system of continuous analysis of everything that’s happening.
You might see that an end user connects in and they start behaving strangely. They start downloading a whole lot more than they did. Normally that might be a red flag, and you might want to do something about that.
You might see that the application at the other end is actually connected to something different than it was before. Maybe there’s one other entity or maybe another app connected into that app that didn’t exist there before. That might be a sign that there’s something suspicious or potentially malicious going on with the application.
And then finally, you would want to be able to look at data coming through. Because again, if we’re not going to trust the user and their device, we’re not going to trust the application. We’re not going to trust the data. We need to make sure that the data coming down from those applications to the end user is also not malicious.
Without a doubt, an approach that places browser security at the core of the security stack is the most effective and efficient zero trust strategy. Browser security and Secure Cloud Browsing is the secret sauce that pulls everything together, acting as a central technology framework through which all security services can be delivered safely and securely in the cloud.
Secure Cloud Browsing works by creating a protective layer around users as they navigate the web and applications, blocking not only known and existing threats but unknown and future threats as well. Secure Cloud Browsing needs to be applied consistently across the organization, not disrupt user productivity, give the security team complete visibility and control over web-based traffic and scale instantly to any user in any location around the globe.
When done right, Secure Cloud Browsing makes security invisible, happening behind the scenes where it can’t inhibit productivity for today’s remote workforce. Email clients and web browsers should continue to work as intended. There should be no clients to install or hardware to ship, and common browsing functionality such as shortcuts, cutting, pasting and printing work needs to be preserved. The right browser security solution makes sure employees access the Internet with all of the features and functionality they’ve come to expect. No pixelated screens or read-only web pages. Everything should work for your users as intended no matter where business takes them.
Menlo Security secures enterprise browsers. Menlo Security manages browsers, protects your users, and secures application access and enterprise data, providing a complete enterprise browser solution from any browser. Menlo Security secures browsers while preserving user choice and providing a familiar, easy-to-use experience. You can deploy browser security policies in a single click, secure SaaS and private application access, and protect enterprise data down to the last mile. At the core is the Menlo Secure Cloud Browser which runs within an elastic and orchestrated cloud-native platform, fetching content and delivering safe, decomposed and reconstructed, content to a local browser. Cloud content inspection keeps threats off the endpoint and protects against internet-born phishing and evasive malware. The AI-powered cloud content inspection works with the safe cloud document and archive viewer, browser isolation, and other protections. The Secure Cloud Browser scales globally and can deliver a risk-free local-browsing experience for every user, every tab, and every web session within and across your enterprise.
We live in a connected world where enterprises no longer operate in a silo. Running a business today requires close collaboration with external organizations – such as technology partners, suppliers, logistics companies and freelancers among others. Unfortunately, giving these collaborators access to your business systems and data massively extends the threat surface to entities that you have no control over – giving threat actors more avenues for accessing your critical systems.
Extending zero trust to unmanaged devices forces these entities to confirm their identity before and during connecting to your systems – preventing threat actors from gaining access to your network through these security gaps.
Think of an insurance agency working with a customer to file a claim. In addition to internal users, customers, the claimant, adjusters, auditors and a myriad of other stakeholders have to either provide information or access information in order for that claim to be processed accurately and in a timely manner.
Doing this manually over email, FTP or the phone is labor intensive, introduces the possibility of human errors and, frankly, takes a lot of time. Digital transformation over the past several years has streamlined the process by giving these stakeholders access to internal systems through a web-based portal. But, each of these connections provides an opportunity for an enterprising malicious actor that has already breached a partner’s system to spread throughout the insurance company’s network.
Zero trust ensures that all entities – whether they belong to the insurance agency or not – continuously prove trustworthiness to access any system on the network. Extending zero trust to unmanaged devices enables this new collaborative way of working without adding security risk or IT overhead.
Traditional security tools were designed for the hub and spoke model where a few entities outside a hardened firewall connected to the network through a central control point. All traffic would flow back to the data center where it could be monitored and policies would be applied. Organizations just had to authenticate the entity at the first touch and then not have to worry about monitoring or securing east-west traffic.
However, as we have already established, we don’t live in that world anymore. Not only are internal users, applications, devices and data spread out, external entities spread around the world need access as well. The inability to continually authenticate and restrict access on a granular level is a major security gap that threat actors are using with a high degree of success.
A clientless approach managed from a central control point allows you to extend zero trust to unmanaged devices in a non-disruptive way. There’s no need to ask partners to install a software client or give up control over their own device. Yet, you gain complete visibility into who the entity asking for access really is and what they are doing. From there, you can provide granular access based on your existing zero trust policies.
Yes, but only if you routed traffic through a static control point such as a VPN or on-premises firewall. Zero Trust Network Access (ZTNA) uses the public internet to gain this visibility and control – allowing you to continually monitor identity and behavior in order to assess trustworthiness throughout the entire engagement. And, because the cloud is ubiquitous, you can implement zero trust on a global scale wherever you do business without having to worry about latency or bandwidth constraints.
Yes, that is the beauty of a clientless, cloud native approach. You only need one security system to cover any type of device – whether they are corporate devices, your employees’ personal devices or a third-party entity. You don’t need to set up separate systems. A clientless approach through the cloud covers them all and provides a single management plane through which you can create, update and apply granular zero trust policies.
Rather than access the original application, the Menlo Secure Cloud Browser creates a rendered display of the application on the endpoint device directly in the user’s browser. There is no inherent trust of web traffic and interactions. As a result, this shields the application from parameter tampering, web scraping, API abuse, and a host of other problems. Even if the endpoint somehow gets compromised, the threat actor cannot get direct access to HTTP headers, content, and the application. Instead, all malicious activity is executed in the Menlo Secure Cloud Browser instead of the endpoint browser.. In addition, to easily support remote access and/or BYOD users, Menlo Secure Application Access has zero touch and agentless deployment for browser-based applications. This agent-free, easy deployment helps organizations:
Zero trust policies enforce the rules that govern zero trust strategies. For example, an organization may want to force read-only access for suspicious websites to protect users from credential theft. Or, it may want to tighten restrictions around payroll applications because of the sensitivity of data on those systems. Zero trust policies take into account the user, the device and what they are requesting access to–and their trustworthiness are continuously monitored and evaluated.
Traditional security policies authenticate entities (a user, device or application) once at the edge of the network and then give them access to everything inside the network. This worked well when enterprise networks were set up in a hub and spoke model where there was little mobility. Users tended to log in from corporate headquarters behind a robust firewall that could control traffic flowing in and out of the data center.
Today’s networks, however, are highly-distributed and mobile. Users, devices, apps and data are spread out across private and public cloud infrastructures where they are spun up and down on demand. This decentralized architecture hasn’t so much eliminated the perimeter as it has expanded it to anywhere users do business–whether it is a remote office, a home office, a customer site or on the road. The perimeter is everywhere – making it impossible to stop breaches.
Zero trust policies continuously authenticate entities at the perimeter and inside the network, ensuring that nothing gets through the cracks. This granular control allows you to identify and monitor changes of trustworthiness. Rather than assume authenticated entities are trustworthy, zero trust policies assume everything is malicious by default and require them to continuously prove their trustworthiness.
It’s a strategy that requires enterprises to completely rethink how they protect the organization. Zero trust policies must be ubiquitous throughout the network security stack–including the Secure Web Gateway (SWG), firewall, and Cloud Access Security Broker (CASB). Whether someone is connected to a cable coming out of the wall at the corporate headquarters or logging on from public WiFi in a coffee shop, zero trust policies govern exactly what they can access and at what level.
You can’t secure what you don’t know. Any zero trust policy starts with cataloging your applications so you know where they sit in the network and what users need access. You can then define levels of accessibility to determine who gets full access, who gets read-only and whether users can get upload or download permissions.
Once you know what you have, you can bake levels of control into your zero trust policies. It’s almost like calculating a risk score. For example, let’s say that a known user is trying to access an application on the network. Multi-factor authentication proves that the user is who they say they are and they are logged into a known device. However, the user is located in a country such as Albania.
Not only is that a strange location for this particular user to be located in, it’s a known hotbed of hacker activity. A zero trust policy can be set to provide the authenticated user access to the application but limits him to read-only. This granular level of control protects the application from potentially malicious activity without disrupting the user’s productivity–just in case the user really does have a legitimate reason for being in Albania. Zero trust policies allow you to set these various levels of security based on pre-set rules and apply them globally.
Zero trust policies also need to go beyond just user to app accessibility. They need to go the other way as well by dictating data flow from the application to the user or even between applications. This allows you to apply zero trust policies to applications, users, devices and data–providing complete coverage across the enterprise. You should even be able to extend policies to third parties such as customers and partners using unmanaged devices to be truly secure. It shouldn’t matter if it’s an application, a person, an IoT device – every entity needs to continually prove its trustworthiness throughout every interaction.
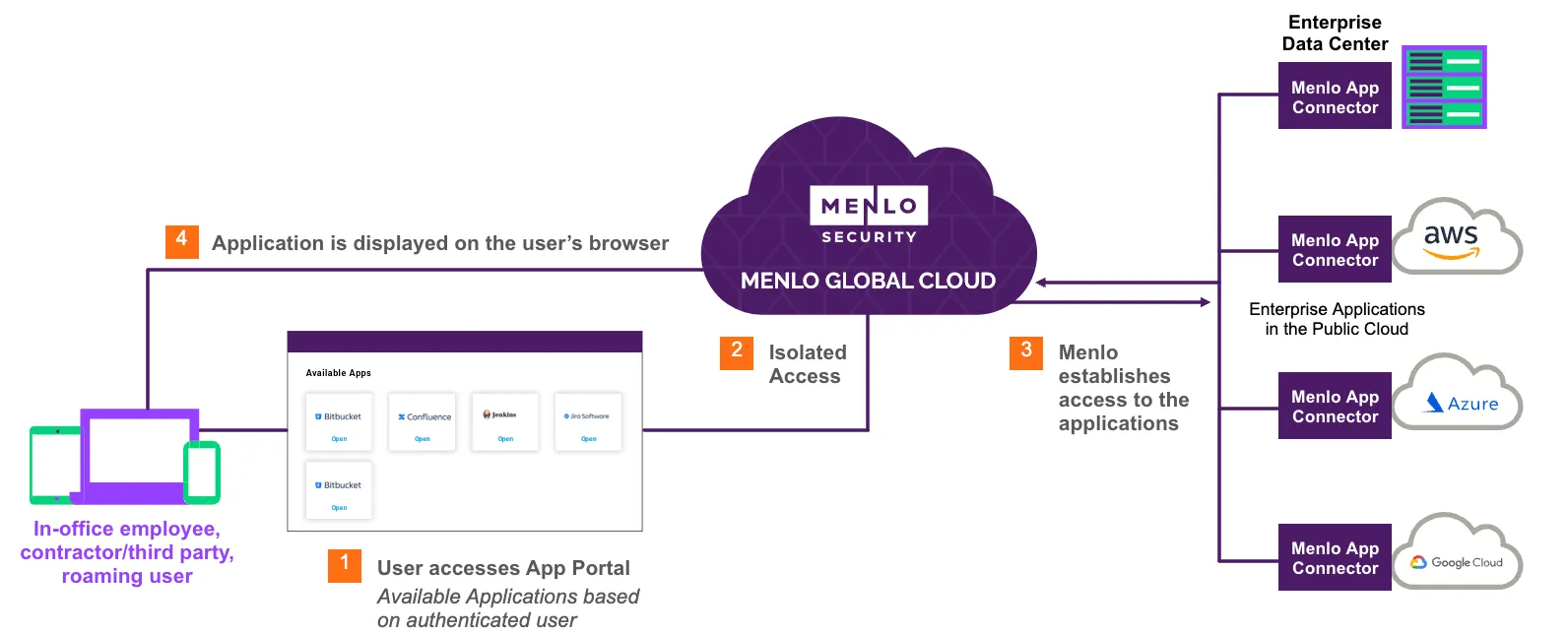
Access is granted only to specific applications that are necessary for a user's job function, not the whole network. The zero-trust principles are built into the foundation of Menlo Secure Application Access, enabling both granular and conditional access policies to even highly distributed employees or third parties. Organizations can define access by users, groups, source IPs, and geographies.
In terms of deployment, Menlo supports zero-touch and agentless deployment for browser-based applications and an agent for non browser-based applications. For browser-based applications, no DNS records are needed, there’s no need to import certificates, and no agent is required. Menlo then provides a single place to create and manage those zero trust policies – allowing you to set once and apply globally across applications, users, devices and data.
Menlo Security is powered by the Menlo Secure Cloud Browser. Everything goes through this abstracted layer in the cloud, giving administrators unparalleled visibility and control into security without impacting the native user experience.
Learn more about Zero Trust Access
Zero trust identity is a way to grant access across the network in a granular fashion based on trustworthiness. Zero trust starts with no access by default and then intelligently provides different levels of access to specific entities – whether it’s a user, an application, data, or a device. And this access is provided based on pre-set rules. However, in order for this to work, organizations need to identify, without a doubt, exactly who is asking for access and what they plan on doing once they get it.
Zero trust identity is more than just username, password and multi-factor authentication (MFA). You need another level of security checks to ensure that the person, application or device is who or what they say they are. This includes other clues such as device information, physical location and, ultimately, behavior.
Traditional identity tools were designed for hub and spoke models where a few entities outside a hardened firewall connected to the network through a VPN. All traffic would flow back to the data center where it could be monitored and policies would be applied. Organizations just had to authenticate the entity at the first touch and then not have to worry about monitoring or securing east-west traffic. Authenticating with a username, password and MFA worked well for this architecture.
However, we don’t live in that world anymore. In today’s highly distributed enterprise, users, applications, devices, and data are spread out across private data centers, public cloud infrastructures and Software as a Service (SaaS) platforms, and the network is too spread out, too complex, and too interconnected with third-party entities. A user may be able to gain initial access, then have unfettered access to the rest of the network. The inability to continually authenticate and restrict access on a granular level is a major security gap that threat actors are using with a high degree of success.
It’s all about assessing how certain you are of an entity’s identity and then using that assessment to provide or limit accessibility. For example, a known user could log in to an application with the correct credentials and pass MFA. However, what if the user has been determined to be located in a country such as Albania. Not only is that a strange location for this particular user to be located in, it’s a known hotbed of hacker activity. In addition, the user, a marketing executive, is trying to access the payroll app – again, an abnormal behavior.
Do you provide access or not? With zero trust identity you can apply policies that provide the authenticated user access to the application but limits him to read-only. This granular level of control protects the application from potentially malicious activity without disrupting the user’s productivity – just in case the user really does have a legitimate reason for accessing payroll from Albania. Zero trust identity allows you to assess the level of trustworthiness, provide granular accessibility, and apply these policies globally.
You can’t secure what you don’t know. Any zero trust identity strategy starts with cataloging your applications so you know where they sit in the network and what users need access. You can then define levels of accessibility to determine who gets full access, who gets read-only and whether users can get upload or download permissions.
Once you know what you have, you can bake levels of control into your zero trust strategy. It’s almost like calculating a risk score. In the above example, the user provided the correct username and password and passed MFA but was exhibiting abnormal behavior from a risky location. The result is read-only with no ability to download or exfiltrate the data. Zero trust policies allow you to set these various levels of security based on identity and pre-set rules and apply them globally.
Once you’ve cataloged your network and set identity policies to determine trustworthiness and the corresponding accessibility levels, it’s time to actually connect users without exposing applications to malicious threats. You can do this with a client – such as a VPN – or, ideally, in a clientless architecture. Not requiring a piece of software to be installed on a device reduces IT overhead and allows you to extend zero trust identity to unmanaged devices – such as a partner, supplier and contractor or an employee’s personal device.
On the application side, you need to deploy a connector to grant access to trusted users. These connectors reside wherever the application sits – whether it’s in a data center or the public cloud – and act as a gateway to allow access for authenticated users. However, today’s distributed enterprise requires direct user to application access across the public Internet, requiring applications to be publicly discoverable. Closing this critical security gap requires a central control point through which all traffic flows that provides a private tunnel over the Internet that is only accessible to authenticated users.
Access is granted only to specific applications that are necessary for a user's job function, not the whole network. The zero trust principles are built into the foundation of Menlo Secure Application Access, enabling both granular and conditional access policies to even highly distributed employees or third parties. Organizations can define access by users, groups, source IPs, and geographies. For non-browser based policies, organizations can enable a posture check of an endpoint before a user can gain access to an application.
Modern enterprises need to make sure distributed entities (users, devices, remote offices, and SaaS platforms) are able to securely connect to applications. While this market is increasingly converging toward a Security Service Edge (SSE) agent-based architecture for the majority of deployments, according to Gartner, it is also seeing increased demand for agentless-based deployments in the case of unmanaged devices and/or third-party access.
A successful ZTNA approach should meet the broad security requirements for managed devices, maximize attack surface reduction, and provide a path to unify highly dynamic, adaptive access control policies in support of your organization’s adoption of zero trust principles.
Unlike VPN connections, ZTNA operates on a zero trust model in which access is granted only to authorized applications required for a particular person or role to do their job, wherever that application might reside. In this way, connecting to the network doesn’t provide the ability to scan or search across the whole network, and allows distributed applications to be accessed through a single connector. According to Gartner, organizations looking to replace their existing VPNs can benefit from significant risk reduction for their enterprise by leveraging ZTNA alternatives. Many of these ZTNA benefits include:
ZTNA solutions are used to connect end users only to authorized applications, wherever the user and application happen to reside. According to Gartner, ZTNA has evolved from being primarily a VPN replacement into a key component of a standardized zero trust architecture for remote and branch users.
For a ZTNA solution to be effective, it must validate the identity of the user and assess the security posture of the device being used, ensuring it aligns with the defined policy before granting access to the application. Once authorized, a secure connection is made between the user’s device and the application.
This approach ensures that users are only able to access applications based on a particular user’s identity and unable to view or access any other application for which they lack authorization for. Furthermore, it helps prevent lateral attacks in the event an attacker were to gain access, they would be unable to spread laterally throughout the organization.
While ZTNA solutions might seem ideal for providing highly scalable, direct connections between your applications and remote users, most ZTNA tools are designed to establish a secure connection and then step out of the way, allowing users to freely interact with their applications. The challenge with this approach is that it leaves security teams without visibility into user’s traffic, making them blind to potential data transfers that might take place between users and applications. This exposes them to potentially missing incidents involving sensitive data storage, access, or potential upload of malicious content.
This inability to monitor such inconspicuous behaviors, such as compromised user credentials, used data exfiltration, or other nefarious activities, poses a significant threat for security teams. Consequently, it is imperative for organizations to implement a ZTNA solution that not only provides access and visibility, but also enforces security after establishing a secure connection. This proactive approach ultimately prevents potential security incidents and achieves a true zero trust connection.
In today’s multi-cloud environment, applications can be distributed across multiple cloud platforms, as well as on-premise infrastructure. Modern organizations require their digital assets to be accessible from anywhere, on any device, to help meet the needs of their growing hybrid workforce. Next-gen ZTNA solutions should integrate seamlessly with your existing security investments to expand the protection and visibility needed. They should provide security teams with bidirectional visibility into all communications, allowing them to protect users from attacks originating from an application and implement data loss protection (DLP) policies where needed.
Next-gen ZTNA redefines trust, operating on the principle that nothing should be inherently trusted. Unlike traditional solutions that primarily concentrate on just securing access, next-gen ZTNA solutions like Menlo Security’s Secure Application Access incorporate enhanced security measures needed to safeguard today’s users, data, and applications against the growing menace posed by ever-evolving threats, and highly sophisticated threat actors. Secure Application Access meets the extensive security requirements for managed devices by leveraging our elastic isolation core to create a rendered image of the application on the endpoint device directly in the user’s browser, rather than interacting with the application itself. This ensures the safest path to accessing browser-based enterprise private and SaaS applications using dynamic access control policies and enabling granular filters in support of an enterprise’s adoption of zero trust principles while maintaining a seamless user experience.
Organizations implement Zero Trust Network Access as a way to provide secure access for users to applications, data, and services based on a defined set of access control policies. ZTNA differs from virtual private networks (VPNs) by providing access exclusively to specific applications, whereas VPNs grant access to the entire network, and therefore all applications.
Organizations that take a zero trust approach to security understand that the traditional detect-and-remediate approach to cybersecurity is broken. Zero trust mindsets assume that all content – regardless of whether it originates from a trusted source – is untrustworthy.
A zero trust security strategy begins with no access as the default. That means that no user, device or application – regardless of location or status – can access anything. This prevents threat actors from accessing endpoints and spreading through the network.
Zero trust security provides another level of security checks to ensure that the person, application or device is who or what they say they are. This includes other clues such as device information, physical location and, ultimately, behavior.
Modern applications are no longer monolithic stacks in a single data center. They’re now split up into thousands of microservices spread out across multiple cloud infrastructures. Zero trust security enhances this experience.
Taking a zero trust approach to security means flipping the philosophy of trust on its head. In this case, trust must be earned by all people and devices, whether they’re internal or external.