
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

Users in hybrid work environments around the world access private and SaaS applications in multiple clouds. To manage risk and ensure business productivity, organizations need to deliver safe, reliable, and consistent access to applications.
Today, most organizations have more than 1,000 applications in use, and the number is increasing year over year. These applications, which once resided in private data centers, are now spread around the globe in private and public clouds. Both SaaS and private applications serve a wide variety of purposes for enterprises, from product development to project management to collaboration and so much more.
Organizations use a wide range of applications day to day, which leads to a wide variety of data being transmitted across and stored in these applications. This data includes but is not limited to:
This data can be used by competitors and cybercriminals to gain an advantage over an organization.
Businesses are legally obligated to keep their customer and employee data safe. Violations of data protection laws and regulations, such as HIPAA, can result in large penalties as well as reputational damage and customer churn.
Beyond the risk of a data breach, application security is vital for business continuity. If a threat actor gains access to a critical application and takes control, how long will it take for operations to stop? Even if you manage to regain access without paying a ransom, the downtime and reputational damage are guaranteed to be costly.
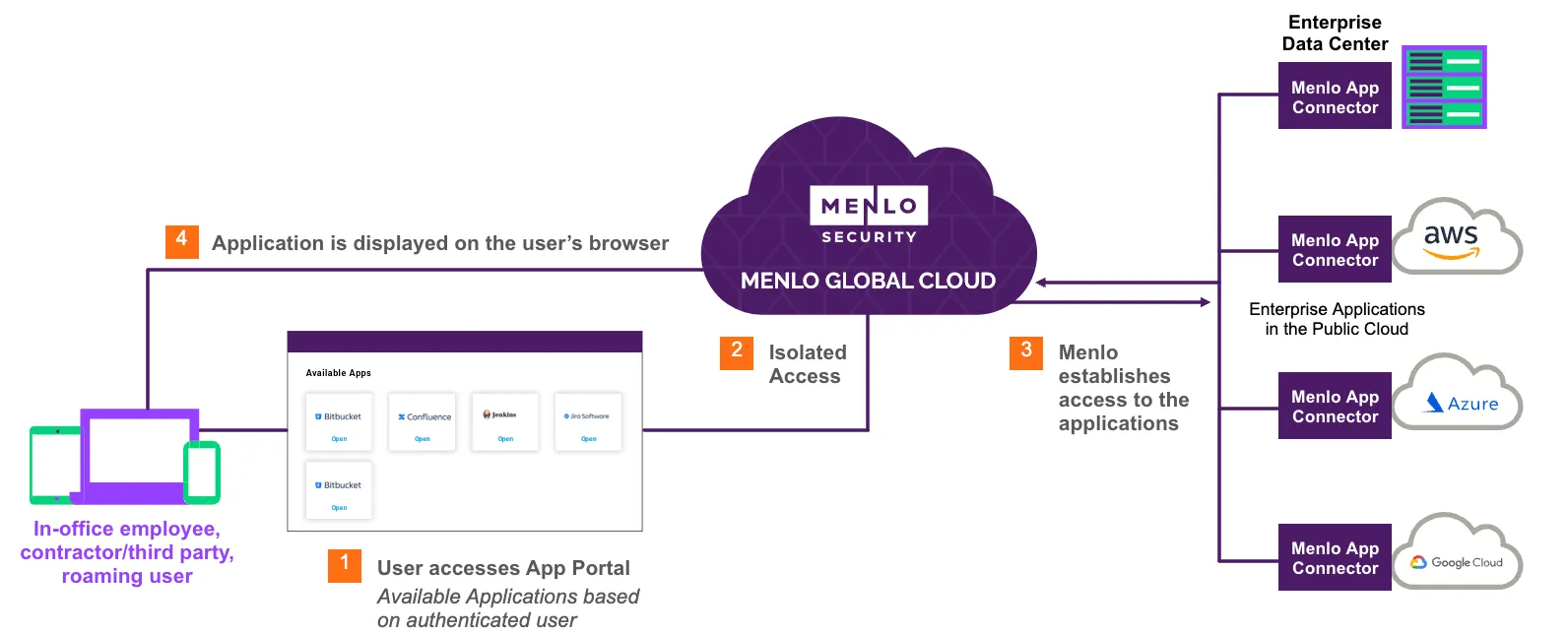
Providing secure access to SaaS and private applications with security and visibility enforced
IT and security teams need to know all the applications that are being used in the enterprise. This is true even when remote workers are accessing remote applications that require cloud solutions to monitor and control connections. Compliance and security teams need access to real-time reporting around application usage.
As data flows between end users and applications, data security needs to be enforced. Maintaining real-time visibility into all connections, along with control over the data being exchanged, is vital for every organization.
End users must be able to access the applications they need to do their jobs, generally a subset of the overall population of applications an organization uses. There should be no ability for an end user to access an unauthorized private application or a risky unsanctioned SaaS application.
End users are accustomed to having direct access to many applications in their personal lives. This expectation needs to be met in the corporate world as well, or users could look to circumvent control. Use a solution that offers a high-performance connection, with an end-user experience that has no learning curve, such as a dashboard of application tiles, which is consistent with many multi-factor authentication (MFA) offerings.
While protecting against data loss is vital, it is just as critical to prevent malware and other evasive threats from entering the network via applications. Even trusted applications must be treated with suspicion, and a control point that analyzes all content within a communication should look for malicious intent as well as sensitive data.
Menlo Security Secure Application Access makes Zero Trust access easy, delivering safe, reliable, and consistent access to applications, wherever employees log in around the world.
Make certain that unsanctioned SaaS applications are controlled and that users can only access the private applications they are authorized to use. Ensure your team has comprehensive visibility into application usage.
Remote employees are assured of the same seamless user experience and security policies no matter where they’re working in the world.
At the core of Secure Application Access is the Menlo Secure Cloud Browser, which fetches and serves the content for users while protecting applications from attacks, such as session hijacking, cookie manipulation, and other tactics that employ protocol manipulation.
Reduce IT operations complexity, freeing the security team’s time to focus on strategic initiatives.
Easily deploy with a clientless or client-based approach. All management is done through the same management console as the other Menlo Security solutions.