Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why


Security Service Edge, or SSE, recognized the crucial need to replace outdated IT security equipment, consolidate vendors, implement zero trust access, and secure cloud consumption. But the internet abounds with stories from IT teams about long, complex SSE deployments.
The user experience today is web-based applications, either software as a service (SaaS) or internal applications, accessed with a web browser. If you are on an SSE journey, ask yourself, will SSE protect my organization against the latest web-borne threats, including malware in files, archives and active code? Select Menlo Browser SSE, achieve your SSE goals, and close the browser security gap at scale for all user activities in their preferred browser.
The security services in SASE and SSE are SWG, CASB, and ZTNA—with DLP scattered among them. Menlo Browser SSE has them all:
All these capabilities are delivered from a scalable architecture operating in leading hyperscaler clouds with global points of presence and the fastest network connections, making all the security services above transparent to users.
Get the Longer Story in the Browser SSE Solution Brief

A single management pane, SWG, and CASB controls you're already familiar with, and security for the modern enterprise makes Browser SSE the right alternative to complexity and cost.
As an illustration of rapid deployment, in less than two weeks, Synapxe, Singapore's National Healthtech Agency, onboarded more than 67,000 users to the Menlo environment.

Security Service Edge offerings are perceived by many decision makers as expensive. Vendors explain that they’re delivering integration that saves time. The explanation is laid bare as false as so many SSE offerings require multi-screen management.
Menlo Browser SSE is cost-effective, costing up to 60% less than most SSE offerings, with flexible licensing. As customers see increasing value in Menlo, we offer midterm subscriptions on additional features.

The odds are good that your last few legacy apps will finally transform to a cloud-delivered model. SSE struggles to secure these apps, but Menlo Browser SSE is designed from the ground up to secure your internal web apps, your SaaS usage, and all your users’ web activities. Talk to us about your legacy apps, too.

Analyzes GenAI use and risks: Shadow AI, data loss, compliance, phishing, and malware.



Security Service Edge is a multi-step journey. Here are some of the steps:
Shorten your journey to SSE. Make Menlo part of your SSE journey with these capabilities:

Browser SSE offers full SWG functionality and much more. SWG core functionality starts with traffic categories and URL filtering. Because a SWG is a network device, it is not capable of seeing an entire browsing session. Most, if not all, modern highly evasive threats leverage this fundamental weakness in SWGs. At the web application level, the Menlo Cloud renders the web session in the cloud, and removes active content as well as inspects all files and archives, including those that are password-protected. The Menlo Cloud stops threats no SWG can stop.
The Menlo Browser SSE inline CASB controls SaaS consumption with an intuitive administrative workflow and a user-friendly experience, beginning with a curated list of thousands of known web applications. Application Discovery gives you information needed to manage SaaS consumption. Rules give you unique combinations of security and flexibility, on a per-application basis. Exceptions to least-privileged access rules offer the same level of specificity.
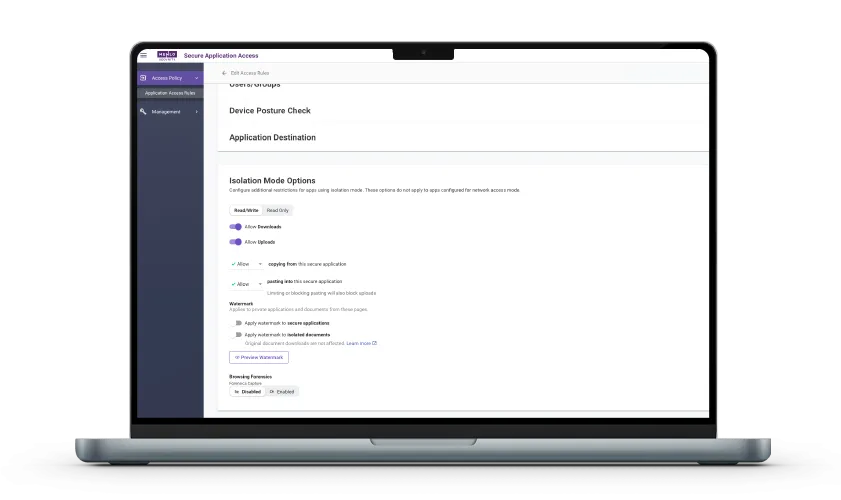
ZTNA is an SSE core component. Browser SSE delivers ZTNA with the cloud-delivered Secure Application Access (SAA) solution. SAA offers effortless, agentless ZTNA for remote and hybrid workforces on managed or unmanaged devices, using any browser. The Menlo Cloud creates a protective barrier between endpoints and applications, ensuring a compromised endpoint can never infect an enterprise application, eliminating the risks of VPNs and the complexity of VDI.
Stopping zero-day phishing attacks is perhaps the best reason to choose Browser SSE over mainstream SSE offerings. Menlo Heat Shield AI detects fraudulent web sites that have been set up by threat actors to steal credentials, personally-identifiable information (PII) and other sensitive data. The Menlo partnership with Google has added Google Vertex Gemini AI analysis to further strengthen fraudulent site detection.
Answers to the burning questions in your mind.


SSE, which stands for Security Service Edge, calls for migrating to the cloud the configuration, management and monitoring functions for Secure Web Gateways (SWG), Cloud Access Security Brokers (CASB) and Zero Trust Network Access (ZTNA). Other factors driving SSE include vendor consolidation and replacing VPNs with ZTNA. For more information, read this article.

Menlo Browser SSE differs from regular SSE because it is centered around browser security while simultaneously delivering all SSE functions. Regular SSE tends to be centered around a specific SSE function depending on the SSE vendor's core strength. In addition, regular SSE suffers from providing either checkbox browser security delivered either with outdated pixel-streaming-based remote browser isolation (RBI) or crippled-function replacement browsers.

Menlo Browser DLP has two advantages over most mainstream SSE solution's DLP:
Read more about Menlo Browser DLP here.

The browser security gap refers to attacks embedded in web traffic that are specifically designed to evade detection by legacy network security devices such as SWGs, CASBs, IDS/IPS appliances, and Firewalls. Read about those attacks here.
While many SSE offerings offer a form of browser security, those that do not cannot close the browser security gap. The SSE offerings that provide a form of browser security do so with replacement browsers or pixel-streaming remote browser isolation, both of which have their own disadvantages. Read about the disadvantages of pixel streaming. Read about the disadvantages of replacement browsers in our blog series part 1 and part 2.

Yes, Menlo Security fully supports and accelerates the implementation of a Zero Trust architecture. The Menlo Cloud is a foundational element, ensuring that access is granted only on a least-privileged basis and that all web requests are isolated from threats. The Menlo solution is simple to deploy and manage, making Zero Trust access easy to achieve across all users and devices, including BYOD.
Menlo Secure Application Access delivers the SSE ZTNA component.

This is a subtle point! Because all the main components of SSE are network security, they have to be in the user data path. SSE definitions mandate that the management, configuration, and monitoring components of SSE be cloud-based. Fulfilling the mandate, Browser SSE delivers all of these activities from the cloud.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.



Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
To protect its 67,000+ users, Singapore’s healthtech agency Synapxe replaced its disruptive, pixel-streaming RBI solution. They adopted the Menlo Security Enterprise Browser, which uses Adaptive Clientless Rendering™ (ACR) and DOM mirroring to deliver a lightweight, safe view of websites. This provided seamless security without the performance degradation of their previous solution.
