Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why

The high infrastructure demands of desktop virtualization (VDI and DaaS) were not built for today's dynamic hybrid environment. This rigid architecture introduces immense capital expenditure and specialized labor, while chronic latency frustrates users. Ultimately, scaling VDI to meet growing demand becomes prohibitively expensive and architecturally unsustainable.
The architectural burden and excessive cost of VDI are no longer sustainable for securing managed and unmanaged devices. You need a solution that drastically cuts infrastructure costs, simplifies IT management, and delivers superior performance without the complexity of desktop virtualization.
A combined 71% of organizations require VDI specialist intervention at least weekly. This includes 31% who report daily problems and an additional 40% who report them weekly.
Nexthink Research.
When users report issues to IT, nearly half (47%) of all complaints are related to slow performance. This makes it one of the most common and disruptive problems in VDI environments.
Betanews.
Beyond just running slow, the single most-reported VDI problem is application functionality failures, which are cited as the top complaint by 54% of organizations.
Nexthink Research.
Menlo Secure Application Access (SAA) is the superior, application-centric alternative to vulnerable VPNs and costly VDI, delivering frictionless, agentless ZTNA. Its unified cloud architecture integrates strict DLP and File Security to actively prevent data leakage and threats, all while providing comprehensive Forensic Visibility for compliance and auditing.
Eliminate the need for VDI's host-based isolation. SAA establishes a protective barrier in the cloud, guaranteeing no application code, session data, or sensitive files ever execute on the end-user device. This completely removes the endpoint as a threat vector, ensuring VDI-level security without the complex management or agent deployment.

Provide a seamless, faster user experience than traditional virtual desktops. By delivering applications directly through a standard browser, SAA eliminates the latency, performance bottlenecks, and backhauling issues common in VDI. Users get instant, reliable access to their needed applications without complex client software or frustrating lag.

Bypasses network bottlenecks and hair-pinning to deliver highly available application speeds for every user, anywhere.

Modern secure access requires eliminating the high costs, complexity, and performance issues of legacy VDI. VDI leads to a high total costs of ownership due to expensive and multiple licensing costs, potential hardware costs, extensive operational costs, and future scaling costs. Instead, Menlo SAA provides a streamlined, cloud-delivered, zero trust solution that secures access for every user and device without requiring any complex infrastructure overhaul, leading to a lower total cost of ownership.
Menlo SAA directly replaces the need for expensive VDI infrastructure, licensing, and maintenance. We achieve VDI-level security without the complex management or agent deployment, which is critical because it significantly lowers your total cost of ownership (TCO). This allows IT and security teams to redirect budget and manpower away from maintaining complex virtual environments and toward strategic projects. Menlo SAA shifts your architecture from broad network-level access to precise application-level access. This eliminates the VPN attack surface, and guarantees that users only get access to what is necessary. This is the only way to prevent lateral movement and achieve true zero trust security.

Menlo SAA delivers security equivalent to a VDI environment by ensuring no application code or session data ever executes on the endpoint. This protective barrier removes the risk of malware and lateral movement, which is critical because it allows your organization to retire expensive, complex VDI infrastructure while maintaining the highest level of data and application isolation for your entire workforce. All this protection is delivered without the need of an agent.

Menlo SAA completely transforms the user experience by delivering a seamless, easy, and high-performance application experience. It eliminates the constant lag and frustrating bottlenecks inherent in VDI. By delivering a native experience directly through the user's browser, it removes the operational friction and complexity that hamper productivity, ensuring your entire workforce gets instant, reliable access without the constant IT support calls common with VDI.

The seamless experience, superior security, and dramatic cost savings you can achieve are direct results of a fundamental shift away from network-centric, legacy approaches like VDI. Below are the key capabilities that enable Menlo SAA to deliver agentless, zero trust access without the complexity of virtualization.

Menlo SAA provides secure access through a standard browser (or extension) with no need to install, configure, or manage an endpoint agent or a thick client. VDI requires installing and managing client software on every access device. This capability eliminates the fundamental security flaw of VPNs by enforcing a separation between the user's endpoint and the corporate application. Every session runs entirely within the Menlo Cloud, guaranteeing that no application code or data ever reaches the endpoint. This design instantly removes the external attack surface and completely blocks lateral movement risk.
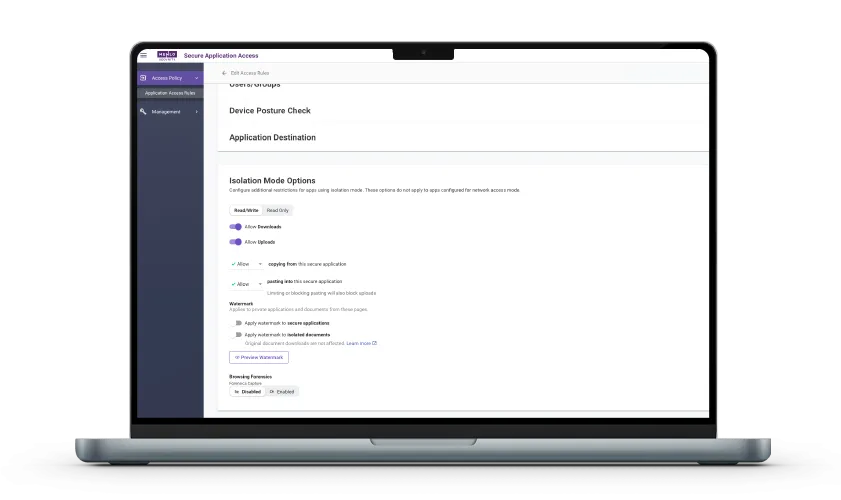
Menlo SAA enforces precise, in-session data controls (e.g., block copy/paste, restrict uploads/downloads, or apply watermarking) directly on webpages and files. Additionally, instead of downloading files, users can access and view files within the secure Menlo Cloud environment. VDI offers little to no granular control over data exfiltration once the user is inside the session. Menlo File Security ensures no malicious content in files ever reach application servers.
Menlo SAA with Browsing Forensics can provide complete, auditable logging and forensics of all user actions within the browser session, including keyboard and screen capture. This gives security teams deep visibility that is often limited or missing in VDI environments.
Menlo SAA enforces true zero trust principles by validating the real-time security health of every device before and during a session. Our dynamic posture check verifies essential factors like OS patch levels, firewall status, and disk encryption. If a device fails, access is instantly restricted or limited, ensuring that your corporate applications are never accessed by a compromised or non-compliant endpoint. Furthermore, seamless integration with Google Chrome Enterprise enables granular posture checks without requiring users to install any additional software, which is especially helpful for managed devices, BYOD users, and contractors using their own devices.
This capability moves beyond simple network access to enforce highly detailed policies based on user identity, group, geolocation, or source IP. This ensures every user is granted the absolute minimum "per-request" access, preventing the broad network access of legacy systems. Additionally, you can apply data security controls, including watermarking, upload/download limits, and copy/paste restrictions, to protect sensitive data, even on unmanaged endpoints.
Answers to the burning questions in your mind.


SAA supports the following application categories:
Modern Web Applications and SaaS: It provides secure, agentless access to applications like Microsoft 365, Salesforce, Workday, and other cloud-hosted solutions.
Internal Private Web Applications: SAA can secure access to corporate web-based resources hosted in a private data center or private cloud environments (AWS, Azure, GCP).
Legacy and Non-Web Applications: SAA also supports legacy applications via the Menlo Security Client.

SAA is a cloud-native service based on a simple, predictable per-user license. It eliminates the Capital Expenditure (CapEx) and continuous Operational Expenditure (OpEx) of VDI infrastructure, including servers, storage, desktop image management, and ticket support, resulting in 5x to 10x lower Total Cost of Ownership (TCO).

Yes. VDI streams an entire desktop display over the network, which often leads to latency and poor performance, especially for video and remote workers. SAA delivers a faster, native user experience because it avoids this video-streaming overhead by routing only secure application content to the user's local browser.

Not entirely. VDI solutions remain valuable for specific use cases, such as providing access to high-performance graphic applications (CAD/GPU) or highly customized legacy desktop operating systems. However, VDI Reduction aims to move web application access, which makes up most employee activity, to a modern, more cost-effective solution like Secure Application Access (SAA).

Organizations are displacing VDI by replacing VDI instances with Menlo Secure Application Access for web-based applications. VDI is often costly and complex, and its protocols are inefficient for the higher-latency environments of remote work compared to HTTP/S and HTML. Menlo delivers a secure, enhanced user experience with significantly reduced costs by providing clientless, zero trust access via the Menlo Cloud to private and SaaS applications.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.



Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
To protect its 67,000+ users, Singapore’s healthtech agency Synapxe replaced its disruptive, pixel-streaming RBI solution. They adopted the Menlo Security Enterprise Browser, which uses Adaptive Clientless Rendering™ (ACR) and DOM mirroring to deliver a lightweight, safe view of websites. This provided seamless security without the performance degradation of their previous solution.
