Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why


The 2025 Menlo Browser Security Report revealed that 20% of attacks seen in the global Menlo Cloud are specifically designed to evade detection by network security devices: Firewalls, Secure Web Gateways (SWG), and Cloud Access Security Brokers (CASB), leaving enterprises exposed to phishing and malware. Meanwhile, most organizations still rely on VPNs and VDI for remote access, decades old and riddled with security issues all their own. Organizations of all sizes are forced to support managed and unmanaged devices, including contractors and BYOD users, accessing applications and enterprise data. This leads to a variety of different tools and infrastructure that's complex to manage and secure, not to mention a poor experience for users. Meanwhile, for decades VPN configuration complexity has resulted in shortcuts that offer more internal applications than most users need to access.
Clearly, teams need to prevent threat actors from penetrating the organization via web traffic or compromising internal web apps data. But how?
For the average enterprise, employees spend 90% of their time in the browser. It's where work happens. Menlo delivers a complete browser security solution. Menlo threat prevention stops phishing and malware in the cloud, before it reaches your network or your endpoints.
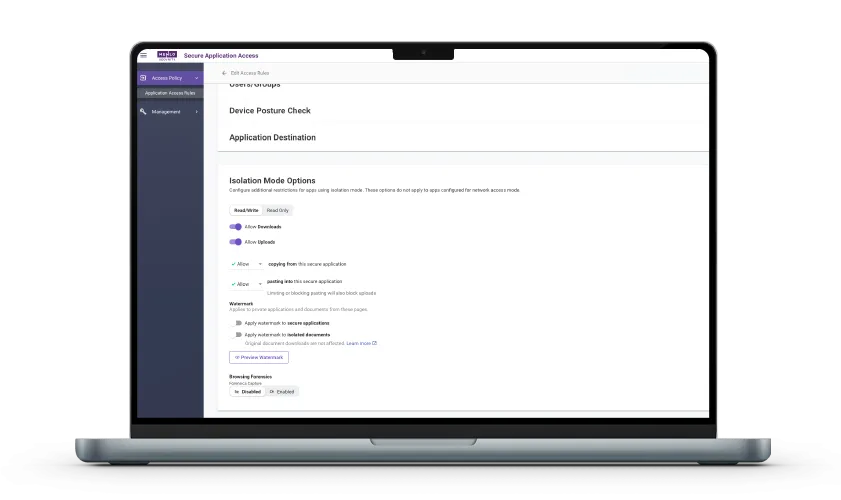
Menlo Secure Application Access delivers clientless ZTNA through the browser, for all your users, managed, unmanaged, and BYOD. Users get a fast, consistent experience regardless of what device they use, and what applications they access. Security and IT teams get a single policy and management interface, with no clients to deploy, patch, or update.
Menlo File Security makes file uploads, downloads, and email attachments sanitized and secure, including encrypted/password-protected files. Together with Menlo Browser DLP, they protect enterprise data and files sent and received via the browser and collaboration apps from inadvertent or negligent exfiltration. This includes controls and governance for GenAI applications.

Menlo isn't yet another browser. With Menlo, you don't have to deploy a replacement browser with design compromises that break modern, complex web apps. Our architecture secures users' browsers with our cloud-based secure digital twin browser that can support virtually any desktop or mobile browser, protecting your organization from web-borne threats and securing your internal web based applications.

The Menlo Cloud provides clientless zero trust access to mission-critical internal and SaaS apps for third party and BYOD users, with as little as a URL, username, and password. Lacking organizational security controls, unmanaged devices carry a higher risk of data loss. Menlo Browser DLP can prevent data loss from internal web apps, and reduce the risk of exfiltration from unmanaged devices.

As a cloud-based solution, there is no need for backhaul to centralized network security or bumps in the wire through other third-party cloud solutions. From any location, every user with any browser is protected by the Menlo Cloud. It is even possible to grant highly secure access to internal applications without a VPN for all users.

It's fast and easy, and it just works.
No clients to deploy.
No Agents to patch or upgrade
No replacment browsers to rollout
No application compatibility headaches
The Menlo Secure Enterprise Browser solution protects against evasive threats and safeguards user productivity. It offers a secure, cloud-based solution compatible with any browser, anywhere. This technology is ideal for organizations seeking robust browser security and seamless user experience.

Protecting the web browser at the core of your user's workspace will change your organization's security posture. Cloud-based preemptive security will stop most phishing and ransomware attacks and enhance user efficiency as well! You will experience:

"It’s totally transparent to users. The table stake [was] isolation of my browser activity away from the local browser on the endpoint. Because Menlo’s working at the browser level, it’s actually able to see all the traffic."
Jack Satterfield of Pima Community College
Pima Community College, Tucson, Arizona, USA serves over 30,000 students with over 2,500 staff across 9 campuses and centers.
To protect its 67,000+ users , Singapore’s healthtech agency Synapxe replaced its disruptive, pixel-streaming RBI solution. They adopted the Menlo Security Enterprise Browser, which uses Adaptive Clientless Rendering™ (ACR) and DOM mirroring to deliver a lightweight, safe view of websites. This provided seamless security without the performance degradation of their previous solution.

Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
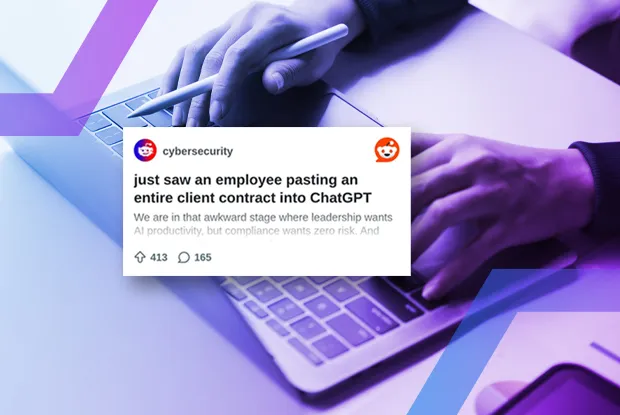
GenAI Access Happens in the Browser
GenAI and browser security are inextricably linked. Can you both permit and secure its use? With Menlo, you can. The Menlo Secure Enterprise Browser solution delivers control of both copy and paste operations in the web browser. It offers dictionary-based data loss prevention (DLP) that operates directly in browser traffic, in two crucial ways: first, for text inputs (form fields) including GenAI form fields and, second, for files and archives uploaded to GenAI (and elsewhere, including web-based email). Further, it can block, set as read-only, or watermark specific web properties, such as unapproved GenAI providers. Finally, the solution can help you eliminate Shadow AI, a problem of significantly higher risk than the use of Shadow IT two decades ago.
Your trusty old Secure Web Gateway (SWG). Its original vendor was acquired and then the buyer was acquired. Along the way your support costs have ballooned. Each renewal, your buyer asks you, do we still need to buy support for this?
Meanwhile, do you know that your SWG can’t really stop web-borne threats? That it can’t stop HEAT attacks such as HTML Smuggling?
The 2025 State of Browser Security Report indicated that the vast majority of phishing attacks and file-borne malware come from categorized sites. The days of category-based security are over. The Menlo Secure Enterprise Browser solution includes web categories you know, but unlike a SWG, sees entire files and archives, including those that are password-protected. And, it stops zero-day phishing and social engineering attacks. Your SWG cannot do that.


Lower your Virtual Desktop Infrastructure (VDI) and Desktop as a Service (DaaS) costs.
Desktop and network teams face dual miseries supporting VDI and DaaS: first, very high total cost of ownership and second, users frustrated by slow logins and chronic latency. Menlo Secure Application Access, a component of the Menlo Secure Enterprise Browser solution, eliminates these miseries by replacing desktop virtualization with a cloud-delivered, agentless solution. This shift delivers superior user performance and simplifies IT architecture, resulting in three key outcomes: first, you may be able to reduce VDI TCO by up to 80% by eliminating infrastructure. You will almost certainly Improve user experience with native-like performance for web-based applications and, you are likely to free up specialized IT resources from maintenance overhead.
Answers to the burning questions in your mind.


The Menlo Secure Enterprise Browser solution stops web-borne threats and prevents data loss via web browsers. Fraudulent site detection stops phishing and PII loss. File Security stops malware, including novel ransomware, embedded in files. Data loss prevention stops IP and sensitive data loss via the browser, especially data loss to web-based GenAI portals. The solution delivers secure zero-trust access only to permitted internal and SaaS applications to unmanaged insecure devices such as owned by contractors and BYOD users, preventing malware uploads from insecure devices and data harvesting from permitted internal and SaaS applications.
And when it comes to solving organizational problems, just a quick note on the endpoint, which probably is and will remain the biggest organizational security challenge, because users are fallible humans but perhaps more importantly, the endpoint is contested ground due to, and certainly not limited to: device proliferation and BYOD, lack of visibility, endlessly evolving threats targeting users, and, finally both alert and patch fatigue. Given such challenges, we think that neither replacement browsers or browser extensions can stop web-borne threats on contested ground.

Menlo is cloud-based. Unlike, for example, replacement browsers, with Menlo there are no Agents or other software to install and endlessly maintain on user devices. In the Menlo Cloud, we create a dedicated tenant for you with a wide range of traffic steering options from your devices to your tenant. Tenant management is fast and easy: you can use our web-based graphical user interface, and for the most advanced organizations, you can use our API to update policies from your organizational automation.

Unlike replacement browsers, which force many users into unfamiliar browsers in which they spend most of their day, Menlo supports any browser, for any user, in any location. In addition, the Menlo Cloud architecture enables preemptive threat prevention that protects both the organization from web-borne threats and sensitive internal applications and data from dangers lurking on unmanaged endpoints. In contrast, replacement browsers can't stop certain types of threats that are allowed to arrive on and then infect the endpoint.
Perhaps as bad as the potential to miss certain threats, the leading replacement browser disables the Javascript Just-In-Time (JIT) compiler and Web Assembly (Wasm). This design decision breaks large, complex web apps that need a high-performance browser. Admittedly, JIT and Wasm are subject to attacks. The Menlo architecture is therefore superior to replacement browsers as these performance-oriented Chromium features remain enabled in the Menlo Cloud, with only safe HTML going to the endpoint for rendering.

While browser extensions generally (but not fully) enable users to continue to use their preferred browser (solving the primary disadvantage of replacement browsers), extensions face the same bleak challenge that replacement browsers do: they run on the endpoint, which is contested ground, discussed three questions above. Any browser vulnerability can compromise the endpoint, failing the task at hand. In contrast, by delivering preemptive security in the cloud, the Menlo Architecture overcomes contested endpoint risk.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.