world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

Disclaimer: Menlo Labs has informed the appropriate law enforcement agencies on the intelligence presented in this report.
XeGroup is a hacking group that has been active since at least 2013. The group is believed to have been involved in various cybercriminal activities. This threat actor uses many different attack techniques including:
We assess this group to be a low to medium level threat, going after victims of opportunity.
XeGroup's tactics, techniques, and procedures (TTPs) have been detailed in a report by Volexity, which suggests that the group may be associated with other cybercriminal organizations and may have links to state-sponsored hacking groups. Previously, they have stolen over $30 million from US-based corporations and compromised multiple websites and mobile applications with malicious code that is designed to steal payment card data from unsuspecting customers.
Recently, CISA has issued a follow-up advisory (AA21-209A) stating that XeGroup actors are still actively exploiting this vulnerability (CVE-2019-18935), and have successfully compromised a US government Internet-facing server running Internet Information Services (IIS). The vulnerability, tracked as CVE-2019-18935, allows an attacker to execute arbitrary code remotely on a vulnerable server by exploiting a deserialization vulnerability in the Telerik.Web.UI assembly. Menlo Labs has observed XeGroups targeting government agencies, construction organizations, healthcare across our customer base.
XeGroup is highly likely to be based in Vietnam and operates under the names "XeThanh" and/or "XeGroup". XeGroup is associated with ASPXSPY web shells, and its infrastructure contains the "XeGroup" naming convention. Multiple domains, including one used for XeGroup’s operations, were registered with the email address xecloud@icloud.com and xemembers@icloud.com. Web shells are scripts that are intentionally designed to be malicious, allowing threat actors to gain unauthorized access to web servers and carry out further attacks. Later in this write up, we will discuss ASPXSPY web shells used by this group, the connection to Xe Groups and how it helped lead us to the nearly full attribution of this group.
One of the prevalent techniques of this group included the injection of malicious JavaScript into web pages, by exploiting vulnerabilities in Magento e-commerce platforms and Adobe ColdFusion server software, in addition to the Telerik UI component. The group’s activities were first identified in 2013 when they successfully penetrated point-of-sale systems at retail stores around the world through their malware called “Snipr'' (Credential-Stuffing toolkit) which was created specifically for this purpose.
In addition to stealing financial information directly, XeGroup also attempted to gain access to corporate networks via phishing emails sent out using spoofed domains associated with legitimate companies such as PayPal and eBay. This activity continued until August 2020 when XeGroup was supposedly taken down after being tracked by Volexity’s researchers who reported their findings to law enforcement agencies worldwide resulting in multiple arrests across several countries involved with these activities.
However, it now appears that XeGroup is back and active. CISA reports the group is actively exploiting CVE-2019-18935 and possibly has been since August 2021.
The Menlo Labs threat intel team examined samples from various reports including CISA, Volexity, and our own telemetry to find similarities or any associations to assist in threat actor attribution and analysis.
We started by looking at the EXE used post exploitation. XeGroup uploads masqueraded EXE files as PNG files to avoid detection. These EXE files create a aspx file in C:\Windows\Temp and execute it thereby creating a reverse shell that communicates with XeGroups[.]com as shown in the figure1 below:

XeGroup also uses ASPXSPY web shells in some of their attacks. The web shell is a simple web application written in C# and ASP.NET. It provides a user interface to connect to a SQL Server database, execute SQL commands, and display the results in a table. Notably inside those scripts is a hardcoded User-Agent string. The hardcoded User-Agent string is base64 encoded, when decoded it reads “XeThanh|XeGroups”. The "ismatchagent()" function checks if the user agent matches this pattern, and it will return true if the user agent contains either “XeThanh” or “XeGroups”. If the string is not present in the communications, the web shell returns a fake error page.

The reference to XeGroups and XeGroups[.]com is repeated through the threat actor code infrastructure and so is the reference to “XeThanh''. In fact, in a sample from 2010 we see XeThanh’s earlier card skimmers where he left contact information.
Menlo Labs also observed credit card skimming activity across our customer base where the attackers used a malicious web resource loaded from "object[.]fm". At the time of analysis, this domain was using the nameserver of "XeGroups[.]com". This strengthened the connection between the card skimmer activity and the DLL reverse shell.
We analyzed recent samples of the credit card skimmers used by this group and we noticed that there were minor differences in the evolution of the code but the overall functionality stayed the same. The screenshot below shows the differences observed between the latest code sample that we analyzed vs the samples provided by Volexity and MalwareBytes:

With all of the analysis done above, we were able to retroactively look and find samples from this group. As far back as 2014, the threat actor was seen creating autoIT scripts that automatically generated emails and a rudimentary credit card validator for stolen credit cards. The screenshots below show the threat actor name associated with the scripts created:


Examining the whois history for these sites, yielded email addresses and other identifying information that we then used for attribution.



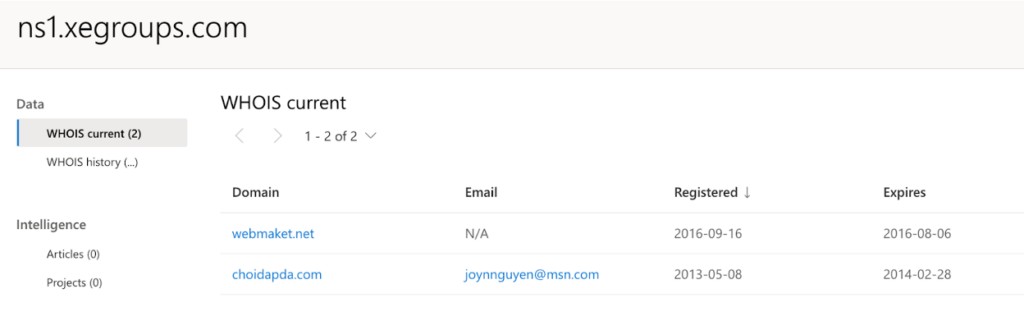
We started with the ns1.xegroups[.]com and ns2.xegroups[.]com that are associated with joynnguyen@msn[.]com. Scouring through tons of data, we found many instances of the name Joe Nguyen and string "XeThanh" found together all over the Internet. Below is an example of a GitHub code repository where we found this association.

Now we will look at the historical record of object[.]fm that was mentioned above in the technical analysis. Five months ago when we inspected the code for the site we noticed a “page title” and a “tag” in the page header referencing “XeThanh”.


Using the username XeThanh and the Icon/Font seen there, we use an OSINT tool and find the actor's Instagram and Friend Finder account, which are both using the same profile picture as well.


We also observed the same icon from GitHub and name Joe Nguyen on Crowdin, which is a cloud-based localization technology and services company. However, we noticed one small change, the alias XePhanmem instead of XeThanh as seen in the screenshot below.

Armed with this information, we diligently began utilizing OSINT tools to maximize data collection, leading to the discovery of additional valuable information. We were also able to identify a unique IP address and password.
In OSINT records for the email joynnguyen@msn[.]com (which was used to register the xegroups[.]com name server) we saw an IP address and a very unique password. We found new email addresses using this exact unique password and following the naming convention this allowed us to pivot further.
Based on the provided data, Nguyen Huu Tai, who also goes by the names Joe Nguyen and Thanh Nguyen, has the strongest likelihood of being involved with the XeGroup. Furthermore, the email address xxx.corp@gmail.com is highly likely to be associated with the group, but more concrete evidence would be needed to confirm this connection definitively.
XeGroup, a low to medium threat level hacking group with a history of cybercriminal activities, has resurfaced and is actively exploiting the CVE-2019-18935 vulnerability. Despite previous efforts to dismantle the group, XEGroup remains a continued threat to various sectors, including government agencies, construction organizations, and healthcare providers.
For additional IOCs please visit volexity and CISA.
Disclaimer: Menlo Labs has informed the appropriate law enforcement agencies on the intelligence presented in this report.