
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


Menlo Security has been closely monitoring an attack we are naming ISOMorph. ISOMorph leverages HTML Smuggling to deliver malicious files to users’ endpoints by evading network security solutions such as sandboxes and legacy proxies. Isolation prevents this attack from infecting the endpoint. Here’s what we know:
Data breaches, malware, ransomware, phishing, and DDoS attacks are all on the rise. And now another type of attack is quickly emerging. Menlo Labs is seeing an uptick of attackers using HTML Smuggling to get their malicious payloads to the endpoint. ISOMorph is one such campaign that is taking advantage of this technique on the heels of attacks by Nobelium, the threat actor behind SolarWinds, who used the same technique in their most recent spear-phishing campaign. Menlo Labs has identified malicious actors using the popular Discord app to host malicious payloads. The Remote Access Trojan (RAT) used in this campaign (AsyncRAT) has many capabilities that are used to evade detection, log passwords, and exfiltrate data. An enterprise infected with this RAT must assume that the goal of the attackers is exfiltration of sensitive data.
Beginning in 2020, when the world shifted to remote working, the browser became the place where work happens. “Even ahead of shelter-in-place and extensive work-from-home initiatives, business users reported spending 75 percent of their workday either working in a web browser or attending virtual meetings,” according to a Forrester study.1 HTML Smuggling delivers malware by effectively bypassing various network security solutions, including sandboxes, legacy proxies, and firewalls. We believe attackers are using HTML Smuggling to deliver the payload to the endpoint because the browser is one of the weakest links, without network solutions to block the payload.
Let’s start by providing a high-level overview diagram of the attack before we dig into the details. We’ve broken down the attack into sections, in accordance with the MITRE ATT&CK framework, to help detection and response teams easily incorporate these tactics, techniques, and procedures (TTPs) into their frameworks.

Menlo Labs has seen attackers leverage HTML Smuggling using both email attachments and web drive-by downloads.
HTML Smuggling is a technique attackers use to construct the malicious payload programmatically on the HTML page using JavaScript, as opposed to making an HTTP request to fetch a resource on a web server. This technique is neither a vulnerability nor a design flaw in browser technologies, and web developers use this technique often to optimize file downloads.
The attackers behind ISOMorph use the following JavaScript code to construct the payload directly on the browser.
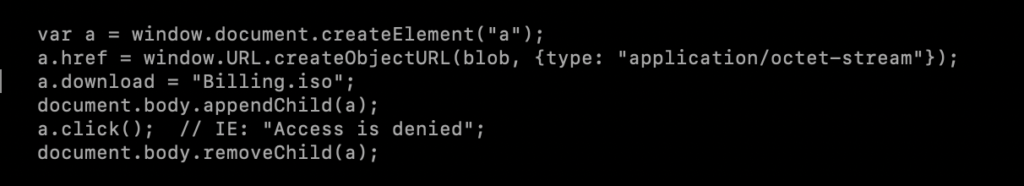
In a nutshell, the JavaScript code is creating an element “a,” setting the HREF to the blob and programmatically clicking it to trigger the download to the endpoint. Once the payload is downloaded to the endpoint, the user must open it to execute the malicious code.
What gets downloaded to the endpoint is an ISO file. Why an ISO file? ISO files are disk images that contain all the files/folders required to install software on endpoints. Attackers are always testing web and email gateway devices to see what file formats are exempt from inspection, then they incorporate those exempt file formats into their TTPs. ISO file formats are preferred by attackers because they do not require any third-party software to install.

The screenshot above shows the contents of the ISO file. While the screenshot above has a VBScript script, we have identified many different malicious scripts being used. The following is a list of all the malicious scripts that we observed embedded in the ISO file:
Once the VBScript script gets executed, it fetches additional PowerShell scripts. The following flowchart details the actions resulting in the execution of the first-stage payload.
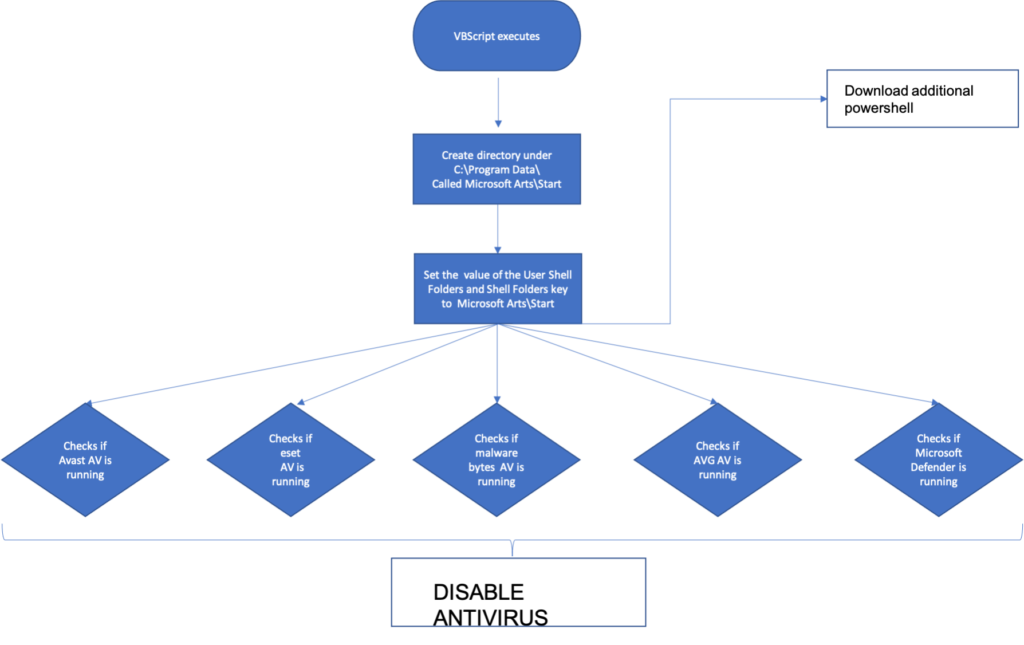
ISOMorph achieves persistence by first creating a Windows directory called “Microsoft Arts\Start” under “C:\Program Data\”. It then sets the registry key value under the “User Shell Folders” and “Shell Folders” to point to the directory previously created. The PowerShell script then downloads a file called “Dicord.lnk” under the “C:\Program Data\Microsoft Arts\Start\” directory. The figure below is a snippet of the PowerShell script that shows the values set to the registry keys, to enable the malicious code to execute on startup.

The bad actors behind this campaign execute the malicious code by proxy, by injecting it into MSBuild.exe. MSBuild is a trusted process, so by injecting into MSBuild, application whitelisting solutions are easily circumvented. The bad actors use reflection to load a DLL file in memory and inject the RAT payload into MSBuild.exe. Reflection enables developers to obtain information about loaded DLL files and the types defined within them, invoke methods, etc. AV usually looks at any files with .dll extensions that get loaded by monitoring the LoadLibrary API. By reflectively loading the DLL files and invoking certain methods, malware authors can bypass AV software. This directly maps to the Technique T1127.001 in the MITRE ATT&CK framework.

As seen from the previous step, a method (WpfControlLibary1.LOGO.hahaha) in the .NET RAT payload is called to start the AsyncRAT functionality. AsyncRAT encrypts its config using AES, as seen below.

The Base64 strings are the encrypted config for the RAT. Upon decryption using the hardcoded AES key, we can see the CnC server host/port, version, and other settings for the RAT.

Below is a screenshot of the campaign we’ve been tracking on VirusTotal. This campaign is available to the public.

NJRAT/AsyncRAT is the Remote Access Trojan that gets dropped to the endpoint. While this RAT family has been used by many different actors over the years, it was predominantly used to compromise high-value targets in the Middle East. While these groups have used the RAT, it does not mean that these groups are behind this specific campaign.
The following groups have been known to use NJRAT:
G0078Gorgon Group[5]G0043Group5[4]G0096APT41[6]
Attackers are constantly testing out newer methods to get their payloads to the endpoint. Menlo Labs has noticed an increase in bad actors using HTML Smuggling for their initial access. This technique is gaining popularity because attackers can get their payloads to the endpoint while bypassing all network inspection and analysis tools. Also, since the payload is constructed directly on the browser, there is a gap in logging and visibility for SIEM and EDR tools. Menlo Labs strongly believes that knowing and understanding the initial access methods is critical to a strong prevention, detection, and response strategy, and we are determined to plug that gaping hole.
1. A commissioned study conducted by Forrester Consulting on behalf of Google, “Cloud Workers Are Key to Disruption Preparedness,” 2020.
Menlo Security
