Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why

While the zero trust security model has been established for years, the deployment of traditional ZTNA solutions remains low. Why? A few factors attribute to the widespread limited adoption in today's hybrid cloud environment.
Menlo Security is the Only Enterprise Browser Company to Be Named a Leader and Outperformer in the GigaOm Radar Report for Zero-Trust Network Access (ZTNA)




Menlo SAA delivers a superior, cloud-delivered zero trust approach to application access. The Menlo Cloud creates a protective barrier, ensuring no endpoint can directly access your application servers. This secure architecture allows explicit and continuous verification of every request for strict least-privilege access, while simultaneously enforcing strong application controls including Data Loss Prevention (DLP), file security, and secure file storage. Delivered agentlessly via any browser, SAA provides seamless deployment, eliminating VDI cost and ZTNA friction.
Menlo Security extends zero trust to the browser itself, turning it into the secure enforcement point. This means no user or device will ever get direct access to application servers. Instead, the Menlo Cloud provides a protective barrier between potentially compromised endpoints and enterprise applications, ensuring all interactions are intermediated, inspected, and controlled.

Enforces policies around identity, device posture, and data at every application request, ensuring true least privilege access and providing the visibility legacy ZTNA lacks.

Delivers zero trust through a user's standard browser with zero infrastructure changes, removing the high cost and complexity barriers of legacy ZTNA approaches.

Learn How the Menlo Solution Aligns with the Technical Requirements of the ZTMM 2.0
By replacing legacy VPNs with an application-centric, cloud-native architecture, you gain a strategic advantage that goes beyond security. You reduce operation burdens and deliver a superior experience to every user.
The architecture of Menlo SAA ensures that a compromised endpoint, even unmanaged or BYOD devices, cannot access, or pass malware to, the application infrastructure. Data is protected with advanced controls enforced directly in the browser session.

Menlo Secure Application Access (SAA) eliminates the operational friction, cost, and complexity of deploying agents, VDI infrastructure, or legacy ZTNA components. This ensures all users get secure access immediately, without increasing the management overhead or resources required by your IT and security teams.
No network rebuilds, no firewall refreshes required, no changes to DNS records are needed, and no need to import certificates.

Menlo SAA delivers immediate, measurable cost reduction by completely eliminating significant capital and operational expenses. This agentless model removes the total cost of ownership associated with expensive VDI licensing, removes the staffing hours spent on agent deployment and patching, and allows organizations to instantly sunset costly legacy ZTNA. Menlo SAA leads to lower IT spend.

The strong security posture and operational efficiency organizations need are achieved through the Menlo Cloud, which fundamentally changes how access is granted. The capabilities detailed below work together to help organizations achieve zero trust goals. This includes effectively separating applications from potential threats and consistently protecting sensitive data where legacy remote access methods often fall short.

Streamline zero trust deployment by enabling instant, secure access for all users, including BYOD and contractors, via any browser. This cloud-delivered, agentless approach eliminates the cost and maintenance of legacy client software.This capability eliminates the fundamental security flaw of VPNs by enforcing a separation between the user's endpoint and the corporate application. Every session runs entirely within the Menlo Cloud, guaranteeing that no application code or data ever reaches the endpoint. This design instantly removes the external attack surface and completely blocks lateral movement risk.
Eliminate application server-side risks by enforcing a complete separation between the user's endpoint and enterprise applications. Instead of running on the endpoint, the entire session runs within the secure Menlo Cloud, guaranteeing that application servers and data are never exposed to the endpoint network.
Enforce the "Never Trust, Always Verify" principle by dynamically validating the real-time health and compliance of every device, both before and throughout the session. Seamless, agentless integration checks OS status, firewall, and encryption to restrict or deny access to compromised endpoints. Furthermore, seamless integration with Google Chrome Enterprise enables granular posture checks without requiring users to install any additional software.
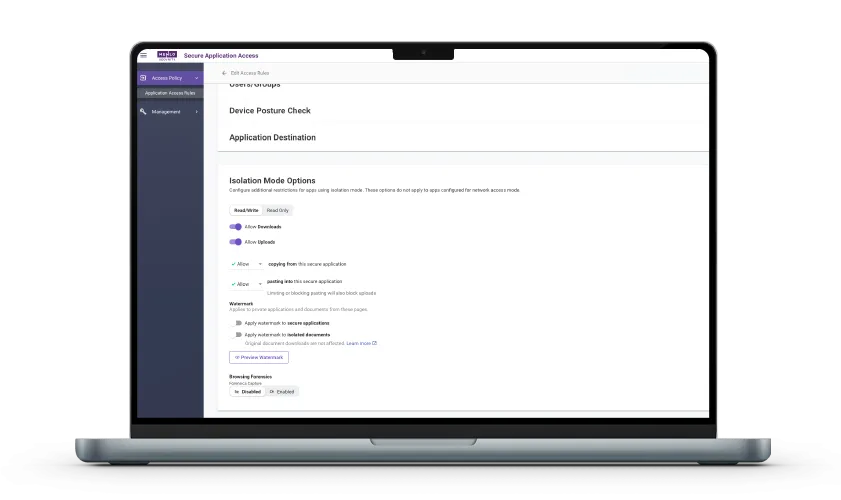
Move beyond broad network access by enforcing highly detailed policies based on user identity, group, geolocation, and source IP. This ensures every user gets the minimum access required "per-request," preventing over-privileged access and shrinking the attack surface. Additionally, you can apply data security controls, including watermarking, upload/download limits, and copy/paste restrictions, to protect sensitive data, even on unmanaged endpoints.
Organizations can enforce strong data security controls like watermarking, upload/download limits, secure file storage, and copy/paste restrictions to prevent leakage, even on unmanaged endpoints. Furthermore, Menlo ensures files transferred to and from applications are automatically sanitized and cleansed, guaranteeing absolute protection against malicious content.
Eliminate the security blind spots inherent in encrypted legacy access traffic. By capturing a complete, browsing forensic record of every session, organizations gain full visibility into user activity, even on unmanaged devices. This detailed, contextual logging allows security and IT to conduct rapid investigations, simplifying auditing and compliance efforts.
Answers to the burning questions in your mind.


Traditional ZTNA often focuses only on network access and still allows the endpoint to establish a connection to a network segment. SAA goes further by delivering the session through a secure, cloud-hosted browser environment, enforcing network separation. This means the endpoint never touches your corporate network and resources are shielded from browser-based threats, a level of protection legacy ZTNA cannot guarantee. Menlo SAA is also agentless compared to the complex agents that ZTNA requires.

Since the traffic is terminated in the Menlo Cloud, we can inspect and enforce policies on data movement directly within the browsing session. This includes real-time controls like blocking downloads/uploads, preventing copy/paste, and watermarking, capabilities that are difficult or impossible to enforce with encrypted, network-centric ZTNA solutions.

Menlo SAA is cloud-delivered and agentless which means deployment is faster and simpler than ZTNA. Applications can often be secured and users onboarded in hours, rather than the months required for complex network integration, infrastructure provisioning, and agent rollout.

Menlo supports Zero Trust Access by making it policy-driven, simple, and comprehensive. It uses the Menlo Cloud to isolate the user's session from the application and employs fine-grained policies based on user, group, and location, providing least-privileged access. It also incorporates device posture checks and provides full visibility into user actions with Browsing Forensics, ensuring continuous monitoring and verification.

Menlo SAA is cloud-delivered and agentless which means deployment is significantly faster and simpler than ZTNA. Applications can often be secured and users onboarded in hours, rather than the months required for complex network integration, infrastructure provisioning, and agent rollout.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.



Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
To protect its 67,000+ users, Singapore’s healthtech agency Synapxe replaced its disruptive, pixel-streaming RBI solution. They adopted the Menlo Security Enterprise Browser, which uses Adaptive Clientless Rendering™ (ACR) and DOM mirroring to deliver a lightweight, safe view of websites. This provided seamless security without the performance degradation of their previous solution.
