
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


Another day, another CVE threat. This time, it’s CVE-2025-6554, a zero-day vulnerability affecting the Google Chrome browser.
On June 30, 2025, Google posted an update to Chrome to fix a high severity security issue. Further, they indicated that an exploit existed in the wild for this vulnerability, making it the fifth 0-day impacting Google Chrome in 2025. This recurrence highlights the need for browser security solutions that take a proactive, zero trust approach in the prevention of web-based threats, such as CVE-2025-6554.
What’s more, this risk is not limited to Chrome. Outside of Safari and Firefox, virtually all browsers, including Microsoft Edge, are based on Chrome and are affected by these 0-days.
CVE-2025-6554 is a flaw in the V8 JavaScript engine used by Chrome and all Chrome derivatives. It is described by Google as a “Type Confusion in V8”. Based on proof-of-concept code that can already be found on GitHub, the issue lies with leaking the now somewhat infamous “TheHole” value, which can then lead to memory corruption, allowing remote code execution in the renderer process.
In plain English, a visited website can load JavaScript that, through unexpected behavior, will lead to the ability to run binary code on the victim’s machine. No interaction is required from the user, and the visited site does not need to be granted any special permission. This code will still be constrained by sandboxing mechanisms that exist in Chrome, but the attacker now has a solid foothold from which they can chain another exploit, targeting either the main Chrome browser process or the underlying operating system.
While vulnerabilities have been found in many areas of the Chrome code base, bugs in the V8 engine are a frequent culprit. Sometimes, the V8 issues are in the Just-In-Time compiler component of V8. As a result, some Chrome derivatives, including Edge, disable the JIT as a result. This can be a costly trade-off, as it will impact the performance of the browser. However, in this case, the flaw appears to be in the interpreter itself, so this trade-off would not have paid off in this instance, leaving only disabling JavaScript altogether as an option to avoid exposure to this type of vulnerability. In most instances, disabling JavaScript is not a viable option, as most web applications would no longer work.
Timeline at a Glance:
Infosec Institute reports that the average remediation window is 60 to 150 days, meaning that users without the proper security tools in place will be left vulnerable as the patch rolls out to all platforms and users in the following days/weeks. In the meantime, it’s been advised that users update their Chrome browser to versions 138.0.7204.96/.97 for Windows, 138.0.7204.92/.93 for macOS, and 138.0.7204.96 for Linux.
According to a recent report by the Google Threat Intelligence Group, 2024 saw 75 zero-day vulnerabilities exploited in the wild, with Chrome receiving a majority of the attacks, a stat that comes as no surprise for those already reliant on cloud infrastructures and an increasingly remote workforce.
Recent Chrome Zero-Days:
CVE-2025-2783: Incorrect handle provided in unspecified circumstances in Mojo in Google Chrome on Windows prior to 134.0.6998.177 allowed a remote attacker to perform a sandbox escape via a malicious file. (Chromium security severity: High)
CVE-2025-4664: Insufficient policy enforcement in Loader in Google Chrome prior to 136.0.7103.113 allowed a remote attacker to leak cross-origin data via a crafted HTML page. (Chromium security severity: High)
CVE-2025-5419: Out of bounds read and write in V8 in Google Chrome prior to 137.0.7151.68 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)
Year over year, threat actors have continued to turn their attention to web-based attacks based on the wealth of sensitive and material non-public information that is being stored online by enterprises, whether via cloud providers, SaaS applications, or accessed remotely by internal team members and third-party vendors.
The report also found that mobile devices were the target of multiple zero-day vulnerabilities, further putting an emphasis on the need for BYOD (Bring Your Own Device) solutions as more enterprises choose to implement remote working spaces where employees are expected to be available via their phones, tablets, and personal laptops.
Coming from Lecigne via TAG, the fear from this particular CVE is its likely connection to state-sponsored attacks, though Google has not confirmed this. As of July 2, 2025, CISA has also added CVE-2025-6554 to its Known Exploited Vulnerabilities (KEV) Catalog, stating that, “These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.”
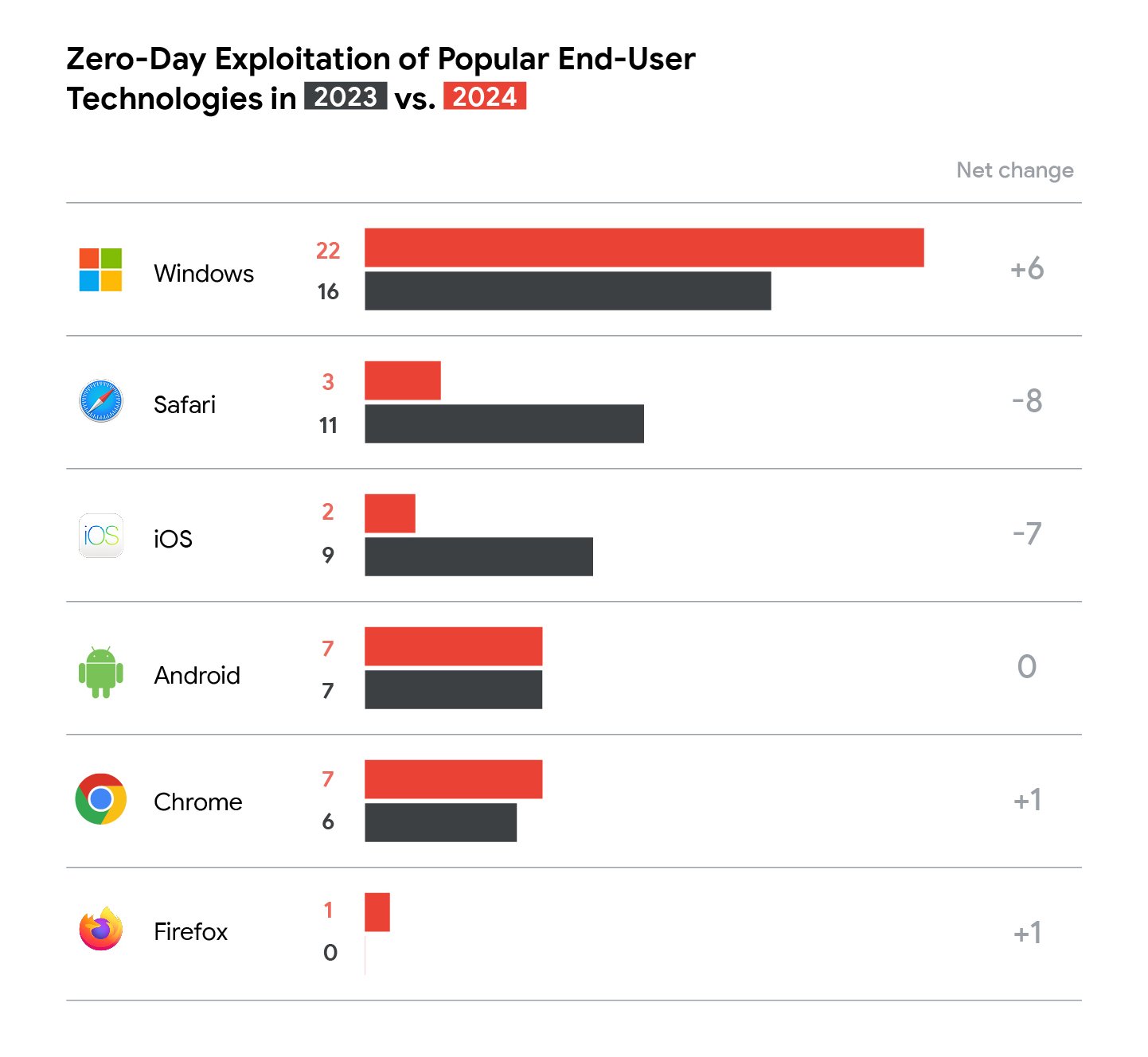
Zero-days in end-user products in 2023 and 2024 (Source: Google Cloud)
It’s also worth noting that an exploit of this nature is just one of many, as Lecigne of Google TAG identified a similar CVE in 2023. This signals a persistent category of type confusion threats that continue to evade detection and leave enterprises open to significant security breaches, including memory corruption and arbitrary code execution that can be used to bypass security checks and gain control of systems. Perhaps most alarming is how easy this kind of exploit can unfold. All it takes is a single visit to a compromised website to start an undetected chain of events, sparked by exploits that are easily created and repeatable thanks to a rise in AI-enabled phishing campaigns.
The browser is a critical tool for many organizations, from internal team members to third-party vendors, meaning that taking it away is not an option, even for a limited time. At the same time, the risk is very significant. To help mitigate this CVE, Chromium users should first take some immediate steps to protect themselves:
While this patch is a fairly innocuous one, not all patches are alike. It’s worth bearing in mind that deploying larger security patches across an organization’s IT infrastructure can present various logistical challenges, as identified here. For instance, there’s a risk of considerable downtime due to systems going offline and the time it takes to test and verify that patches will not adversely affect existing systems.
With a single intrusion acting as a powder keg for enterprise-wide system outages, productivity interruptions, and highly sensitive data exfiltration, it’s not feasible for security teams to manually detect zero-day exploits and roll out subsequent patches within a 24-hour window. Meanwhile, end-users are not keen to wait on patches and quarantine efforts, opting instead to circumvent processes, turn to shadow IT, or simply hope for the best as they look to maintain momentum.
Recognizing the realities being faced by enterprises reliant on the safe access and use of browsers like Chrome, Menlo Security has taken a zero trust approach to browser security, including the elimination of web-based threats, secure access to SaaS applications, and the files they interact with.
The Menlo Approach:
Additionally, Menlo removes JavaScript execution from the user’s browser, moving it safely away to a Secure Cloud Browser while only transmitting the rendered content to the end user. The Menlo Secure Enterprise Browser solution accomplishes this transparently to the user for all client browsers, including Chrome, Edge, Firefox and Safari. There’s no need to install any additional software and no false promises to prevent such exploits by crippling the browser.
Together, Menlo complements Chrome’s own built-in security to address the patch gap problem by transforming any browser (not just Chrome) into an enterprise browser, delivering protection from web-based threats while securing access to applications and enterprise data, no matter the device.
Hoping to avoid the stress that comes with the next, inevitable announcement of a CVE zero-day exploit? Menlo can help you review your organization’s browser security posture, book a demo with one of our experts today.
Menlo Security
