Eliminate Zero-Day Phishing and Evasive Ransomware. Period.
Stop threats cold in the cloud, before they ever reach your network or endpoints
Menlo Protect HEAT Shield AI prevents zero-day exploits and highly evasive threats from ever reaching the endpoint or penetrating the network.
In the Menlo Cloud, we execute all web traffic inside a hardened digital twin of the user’s browser and use AI-powered, on-click inspection to stop even the most sophisticated attacks designed to bypass network and endpoint security tools, all within your organization’s browsers of choice. These protections are more vital than ever, as attackers are increasingly adopting the adversarial use of AI to come up with new or dramatically adapted threats.
The result is safe, high-fidelity browsing and fully functional, sanitized files, all with no software or infrastructure changes required.


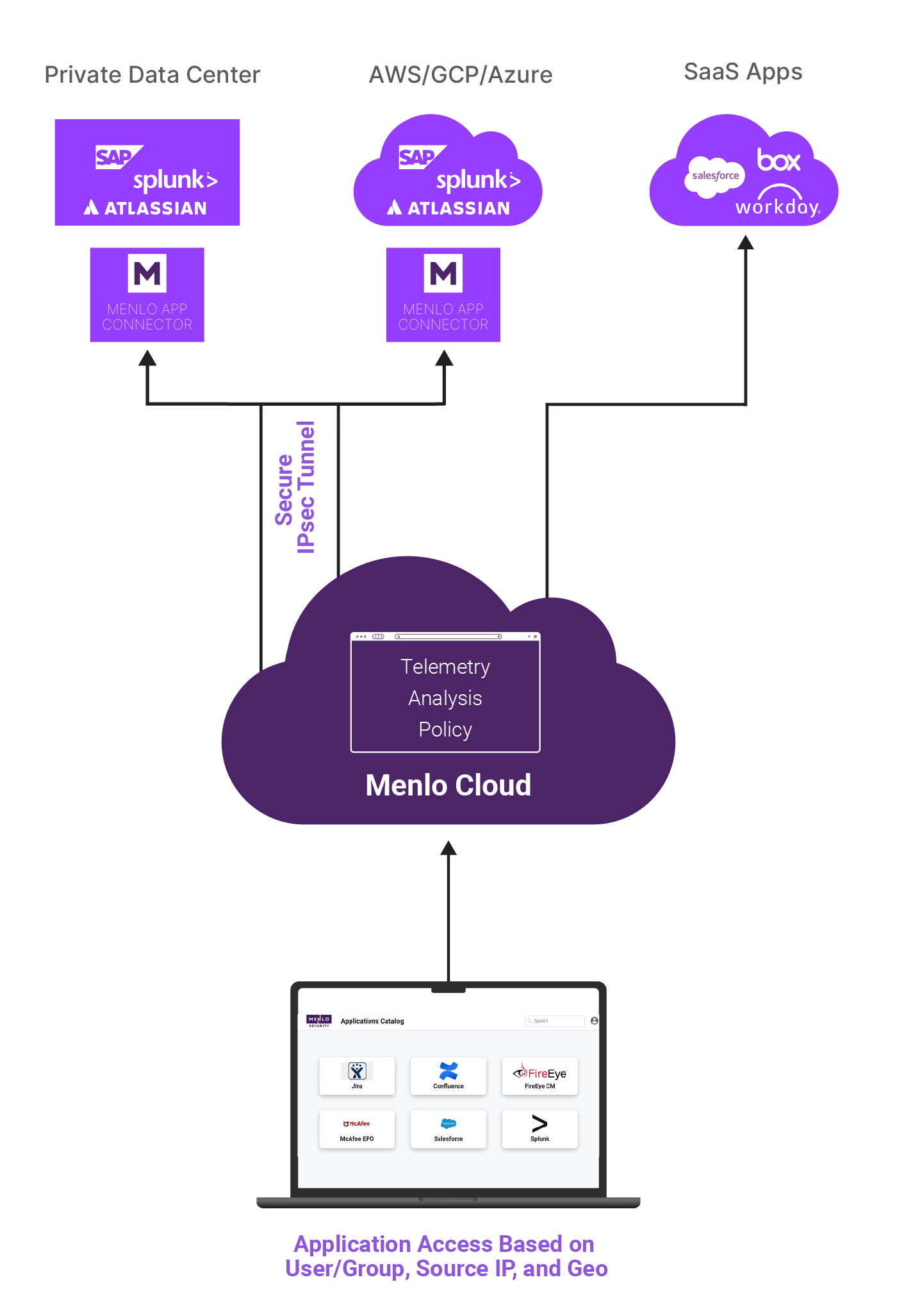
ZTNA For All Devices
Easy to deploy, clientless secure access for managed and unmanaged devices
Eliminate the risks of legacy VPNs and the cost and complexity of VDI with Menlo Secure Application Access (SAA)
Menlo SAA is a cloud-delivered zero-trust solution that makes access effortless and safe for your hybrid workforce. Because unmanaged devices are often unknown and unsecured endpoints on your network, they represent a critical vulnerability. Menlo SAA removes this risk entirely by acting as a protective shield, ensuring that an unmanaged or compromised user device can never infect an enterprise application.
By eliminating VPN risks and VDI complexity, SAA is easy to deploy, protects sensitive data, and delivers a superior, high-performance user experience right through any browser—with no client software.
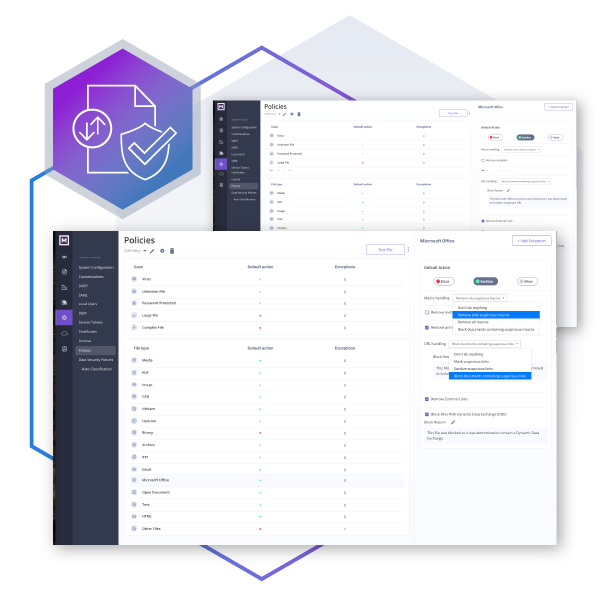
Menlo File Security Wipes Out File-Borne Threats
Current file security tools force a critical trade-off: block workspace productivity to prevent threats, or trust that detection alone will stop malware from entering in the first place. This is unacceptable for modern, file-reliant workflows.
Menlo File Security delivers defense-in-depth by incorporating next-gen Content Disarm and Reconstruction (CDR), antivirus, hash check, and sandboxing. Going beyond traditional CDR tools that simply scan for known threats, our patented Positive Selection® technology assumes all files are malicious, immediately detecting, dissecting, and reconstructing a new, clean file using only components guaranteed to be safe.
This process eliminates evasive malware, ransomware, and zero-day file exploits (even those hidden in archives or password-protected files) while ensuring the final document retains all formatting and functionality. With Menlo, users safely click, download, upload, and share without delay.


.svg)





























_(logo).svg.png)








