world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

During October 2022, the Menlo Labs research team posted details on camouflaged template injection documents that contained a decimal IP address or used an obscure URL format to fetch the remotely hosted template. This article was a follow-up to the post detailing how weaponized template injection attacks work and how these attacks can be prevented. The weaponized documents used RTF exploit templates to deliver malware like FormBook, Snake Keylogger, and SmokeLoader.
Because the TTPs used by the weaponized document attacks had identical footprints, we performed a deep dive on the IOCs in order to fingerprint and attribute the data points to a single threat actor. Based on the attribution of the attacks and the trail of data points we uncovered, we assess with high confidence that the threat actor is operating out of North Korea and is likely tied to the Lazarus group.
During our analysis, we noticed that North Korean threat actors have used TTPs similar to the TTPs that were mentioned and seen in the IOCs from our previous blogs.
A 2020 article by Fortinet detailed how North Korean threat actors leveraged a seemingly benign Word document on South Korea’s response to Covid-19 that had a malicious macro inside to trick victims into downloading the BabyShark malware. North Korean threat actors also sent malicious emails spoofing FedEx, encouraging readers to open a PDF that was actually an executable LokiBot exflitrating data to kbfvzoboss[.]bid/alien/fre.php. This IOC can be seen being used by LokiBot in very similar attacks going back to 2018.
We also found the sample shown below on Joe Sandbox while doing research. Curiously, it shows that North Korean is the resource language, and it contains both the LokiBot URL mentioned above and a similar URL structure to the LokiBot sample: http[://]sempersim[.]su/gj8/fre.php. This sample is also related to ones we analyzed for the previous two blogs mentioned above (it is the secondary malware of this infection chain that the malicious template downloads). We noticed many of the malicious documents tended to download only a handful of secondary malware.


Inside the malicious documents we saw metadata that was repeated in all 57 samples we analyzed for both of the previous Menlo Labs blogs on template injection attacks.

While the metadata matched, we noticed some samples used camouflaged URLs with periods, while others did not. All samples analyzed also used template injection TTPs and exploited CVE-2017-0199.

Similar TTPs were observed being used by a North Korean APT, BlueNoroff, which is currently focusing on targeting cryptocurrency companies. Throughout its SnatchCrypto campaign, BlueNoroff stalks and studies successful cryptocurrency startups before abusing trust in business communications. The infiltration team builds a map of interactions between individuals to understand possible topics of interest. This lets them mount high-quality social engineering attacks that look like totally normal interactions. BlueNoroff compromises companies through precise identification of the necessary people and the topics they are discussing at a given time. This allows the threat to fly under the radar and not trigger any suspicion.
By manipulating trust in this way, BlueNoroff can rely on regular macro-enabled documents or older exploits. One exploit that they stick to is CVE-2017-0199. The vulnerability initially allowed automatic execution of a remote script linked to a weaponized document. The exploit relies on fetching remote content via an embedded URL inside one of the document meta files. The document fetches a remote template that is another macro-enabled document. The first one contains two Base64-encoded binary objects (one for 32-bit and 64-bit Windows) declared as image data. The second document (the remote template) contains a VBA macro that extracts one of these objects, then spawns a new process (notepad.exe) to inject and execute the binary code. The VBA macro does a cleanup by removing the binary objects and the reference to the remote template from the original document and saving it to the same file, essentially de-weaponizing the document.
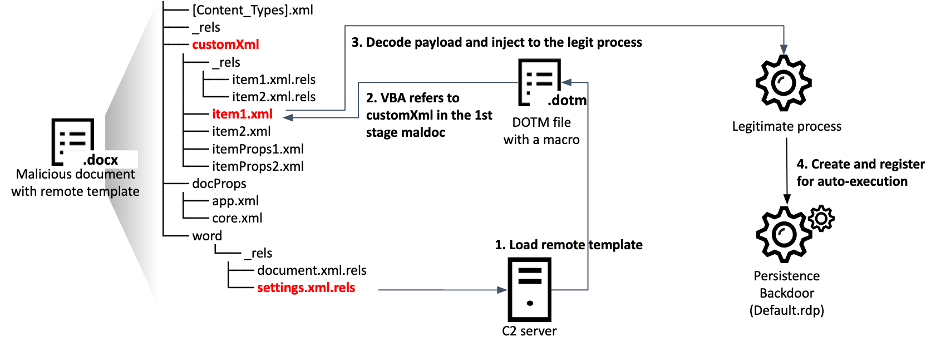
In another separate malicious campaign that used similar TTPs, North Korea used malicious emails that appeared to be from job recruiters. Inside the malicious email was an even more malicious document, which also exploits CVE-2017-0199, just as our other samples mentioned thus far. This document executes a malicious DLL that steals victims’ information, which is then exfiltrated to one of the four command and control servers (C2). The exfiltrated data is compressed, XOR encrypted, and then Base64 encoded before being transmitted to the C2 server.
One of the malicious domains that the above malware will exfiltrate to is shopandtravelusa[.]com. It hosted a webmail login that appeared to possibly be a phishing site. This suggests that this may have been a multi-use C2 when it was being used.

If this was indeed a phishing site, it would not have been the first that North Korea had used.
On June 27, 2022, Twitter user “Phantom XSec” reported a North Korean phishing site (naver[.]challengedrive[.]42web.io) targeting “defectors” in South Korea. The link contains a Base64-encoded Google drive URL and victim email.


The site asks you to identify yourself before you can download the malicious document, which is hosted on a Google drive link. This is a common TTP for North Korea. Analysis of the Google drive link revealed the following information:
Document ID : 1YdiX8eN2O-fiJeauLnAM8TUq4SauCGeG
[+] Creation date : 2022/04/01 01:02:00 (UTC)
[+] Last edit date : 2022/04/01 01:02:12 (UTC)
Public permissions :
reader
[+] Owner found !
Name : SungJi Lee
Email : sungjilee327@gmail.com
Google ID : 05253374549522814493
[+] Custom profile picture !
=> https://lh3.googleusercontent.com/a/default-user=s64
North Korea's threat actor activity is well known for its repeated reuse of aging malicious infrastructure. We don’t anticipate a change in TTPs. While new malware and infrastructure may be added to their arsenal, the continued overlap in TTPs enables analysts to keep a close eye on cyberthreats from this nefarious nation-state.