Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why


The centralized VPN model wasn't built for the hybrid, cloud-first world. This architecture creates an unacceptable external attack surface while introducing the latency and bottlenecks that frustrate users. Even worse, the traffic within the VPN tunnel is often invisible, leaving security teams blind to critical user activity. The continuous investment and complex management overhead make the operational burden unsustainable.
It's clear that VPNs compromise security, frustrate users, and drain budgets. They leave critical blind spots where attackers can hide. Instead, organizations need a modern access architecture that eliminates the risk and scales effortlessly with granular, application-level visibility.
Menlo Secure Application Access (SAA) provides a replacement for vulnerable, costly VPNs by implementing an application-centric architecture. We solve the challenges of risk, complexity, and latency through three main pillars that redefine remote access:
Unlike VPNs that provide broad network-level access, SAA guarantees application-by-application access. This principle instantly eliminates the external attack surface and lateral movement risk by ensuring users never directly access application servers.

Menlo SAA provides one consistent solution for all client types by leveraging a flexible, multi-mode deployment model. The platform prioritizes a clientless, browser-agnostic approach for all web applications, a lightweight browser extension, and finally, a dedicated client is available for non-browser-based applications, ensuring universal and consistent security from a single platform.

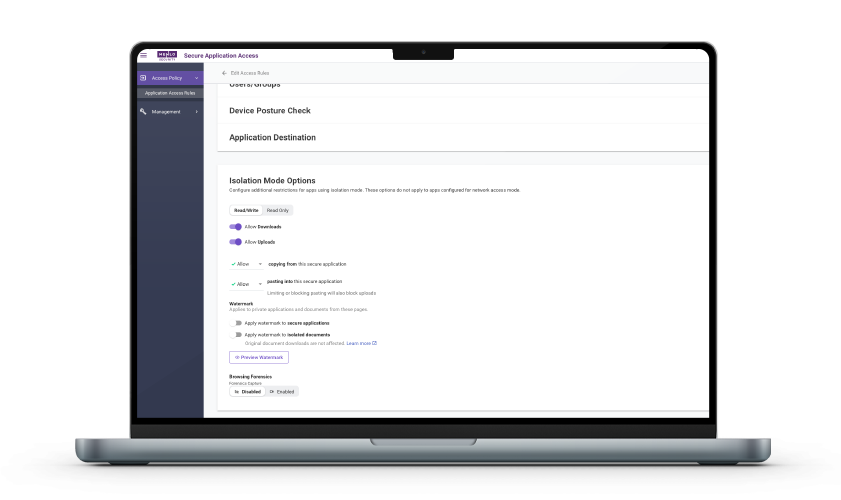
Menlo SAA delivers data protection by integrating security directly into the user session. We enforce strict DLP controls such as copy/paste, watermarking, and data redaction to prevent data leakage. File Security inspects all data transfers which blocks malware in uploads and prevents leakage during downloads, while Secure Storage ensures sensitive information is never transferred to unauthorized or insecure file storage locations, maintaining the integrity of your data within the corporate boundary.

By replacing legacy VPNs with an application-centric, cloud-delivered architecture, you gain a strategic advantage that goes beyond security. You reduce operation burdens and deliver a superior experience to every user.
Menlo SAA shifts your architecture from broad network-level access to precise application-level access. This eliminates the VPN attack surface, and guarantees that users only get access to what is necessary. This is the only way to prevent lateral movement and achieve true zero trust security.

The solution is entirely cloud-delivered and truly agentless, allowing you to instantly retire all VPN hardware and client software. This simplifies and secures access for your entire workforce, especially unmanaged devices and contractors. Additionally, this eliminates complex patching and hardware maintenance, thereby freeing up specialized IT teams and dramatically reducing your total cost of ownership (TCO).

Menlo SAA leverages a global, cloud-native platform that eliminates the traffic backhauling and "hairpinning" caused by VPNs. This results in superior application speeds and a native-like experience for every remote user, boosting both user satisfaction and overall productivity.

Learn how to solve application access challenges in a hybrid environment by adopting a "secure by design" Zero Trust strategy that addresses the risks of unmanaged devices and legacy systems.



The superior security, cost savings, and latency-free access is made possible by a cloud-native architecture. Below are the key, built-in capabilities—from network separation to application-by-application level access, that work together to fundamentally eliminate network risk and retire your VPN.

This capability eliminates the fundamental security flaw of VPNs by enforcing a separation between the user's endpoint and the corporate application. Every session runs entirely within the Menlo Cloud, guaranteeing that no application code or data ever reaches the endpoint. This design instantly removes the external attack surface and completely blocks lateral movement risk.
This capability moves beyond simple network access to enforce highly-detailed policies based on user identity, group, geolocation, or source IP. This ensures every user is granted the absolute minimum "per-request" access, preventing the broad network access of legacy VPNs. Additionally, you can apply data security controls, including watermarking, upload/download limits, and copy/paste restrictions, to protect sensitive data, even on unmanaged endpoints.
Eliminate the security blind spots inherent in encrypted VPN traffic. By capturing a complete, browsing forensic record of every session, organizations gain full visibility into user activity, even on unmanaged devices. This detailed, contextual logging allows security and IT to conduct rapid investigations, simplifying auditing and compliance efforts.
Unlike a VPN, which offers zero data control once the session is established, this capability protects your sensitive data through multiple layers of defense. Organizations can enforce controls like watermarking, upload/download limits, and copy/paste restrictions to prevent leakage, even on unmanaged endpoints. Furthermore, Menlo ensures files transferred to and from applications are automatically sanitized and cleansed, guaranteeing absolute protection against malicious content.
Menlo SAA enforcing true Zero Trust by validating the real-time security health of every device before and during a session. Unlike VPNs, our dynamic posture check verifies essential factors like OS patch levels, firewall status, and disk encryption. If a device fails, access is instantly restricted or limited, ensuring that your corporate applications are never accessed by a compromised or non-compliant endpoint. Furthermore, seamless integration with Google Chrome Enterprise enables granular posture checks without requiring users to install any additional software.
Streamline IT operations and eliminate user friction. By being truly agentless and cloud-delivered, Menlo Secure Application Access allows your entire workforce—including BYOD and third-party contractors—to gain secure access instantly via any standard browser. This shift eliminates the high cost and complexity of purchasing, patching, and maintaining VPN client software.
Answers to the burning questions in your mind.


Menlo Secure Application Access provides a modern, Zero Trust solution to replace the vulnerabilities and limitations of VPNs. VPNs grant broad network access and lack the necessary browser-level context for fine-grained security controls. Menlo replaces this by providing least-privileged access only to specific applications, includes granular controls like copy/paste limitations and data redaction, and logs all traffic with Browsing Forensics for complete visibility and faster incident response.

Menlo SAA delivers superior performance compared to a dedicated VPN connection. VPN performance suffers because it relies on a central server, forcing traffic backhauling ("hairpinning") and creating bottlenecks. Menlo SAA uses a highly distributed, global cloud-native architecture that routes traffic optimally and directly to the application. This approach eliminates the performance drain caused by VPN tunnels, providing a fast, native-like user experience anywhere in the world.

Organizations are replacing their VPNs because they cannot deliver the core principle of Zero Trust—least-privileged access—as they typically grant access to a broad network segment. VPN vulnerabilities also present an unacceptable risk because they are exposed to the internet, and their encrypted nature prevents the visibility needed for breach investigations. Menlo eliminates these issues with fine-grained access, browser-level controls, and complete session visibility.

Instead of granting access to the entire network, Menlo provides access on an application-by-application basis, which helps to prevent lateral movement by a threat actor who may have gained access. The solution also shields applications from malicious requests by preserving network separation and inspecting all requests with AI-driven protections within the Menlo Cloud. This approach also helps to prevent attacks based on unauthorized access, protocol manipulation, session hijacking, and cookie stealing.

Yes, you can quickly provision and de-provision access to applications without needing to change network topology or firewall rules. Access can be enabled for any user with any browser.

Menlo Secure Application Access supports secure connectivity to both private applications (including web-based and legacy applications) and SaaS applications. Users access their permitted applications via a web portal, a browser extension, or a client for non-web-based applications. Examples of supported applications include SAP, Splunk, Atlassian, Box, Workday, and other applications in the Private Data Center.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.



Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
To protect its 67,000+ users, Singapore’s healthtech agency Synapxe replaced its disruptive, pixel-streaming RBI solution. They adopted the Menlo Security Enterprise Browser, which uses Adaptive Clientless Rendering™ (ACR) and DOM mirroring to deliver a lightweight, safe view of websites. This provided seamless security without the performance degradation of their previous solution.
