Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why

The hybrid workforce exposes flaws in traditional access methods. Legacy VPNs expand attack surfaces with excessive network access and agent-based ZTNA involved complex management overhead. Meanwhile, VDI is complex, costly, and delivers a poor user experience. Neither can deliver the secure, seamless access organizations require.
It is clear that legacy remote access can no longer meet the demands of our modern workforce. To truly achieve zero trust and simplify remote access, organizations need an entirely new approach to application access.
Menlo Security Is the Only Enterprise Browser Company to Be Named a Leader and Outperformer in the GigaOm Radar Report for Zero-Trust Network Access (ZTNA)




Menlo Secure Application Access is a cloud-delivered solution that makes zero trust access effortless for remote and hybrid workforces on managed or unmanaged devices, using any browser. It creates a protective barrier, ensuring a compromised endpoint can never infect an enterprise application. This approach provides superior security by eliminating the risks of VPNs and the complexity of VDIs without requiring any software on the user's device; it's easy to deploy, protects sensitive data, and maintains a high-performance user experience.
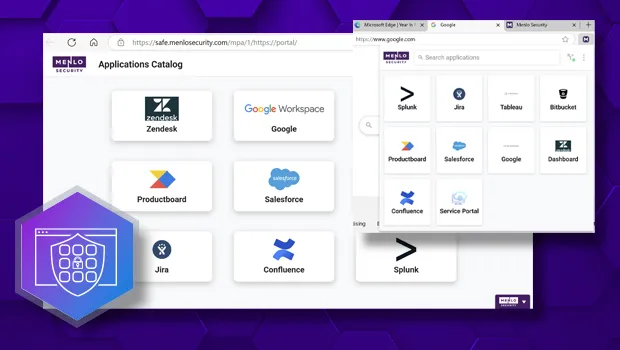
Menlo SAA moves beyond simple network access to enforce highly detailed least-privileged access to SaaS and private applications. SAA separates the potentially compromised client from infecting the network and the application servers. This unique architecture enables IT to securely onboard any user, including BYOD or third-party users, through an agentless approach, while advanced controls protect sensitive data at all times and stop the spread of malware via file transfers.
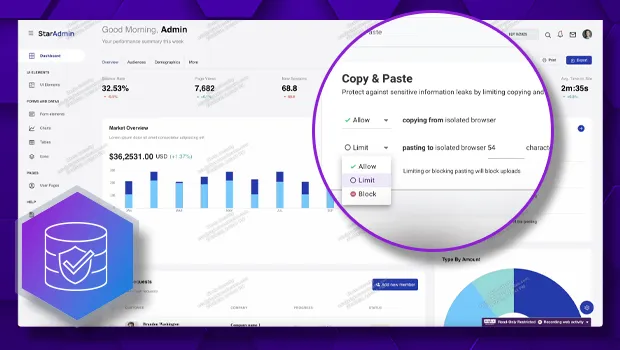
Menlo delivers ZTNA with Browser DLP and File Security that goes beyond the basic secure connectivity that ZTNA solutions offer, and dramatically reduces the need for VDI. Menlo prevents known and unknown cyber-threats and prevents data exfiltration and misuse in real time, for both managed and unmanaged devices using such controls as dictionary DLP for web fields and files, copy/paste, file upload/download, and watermarking. Menlo protects applications and their data, enabling safe zero-trust use of AI, SaaS, email, collaboration tools, and cloud storage, with unparalleled control over sensitive information.
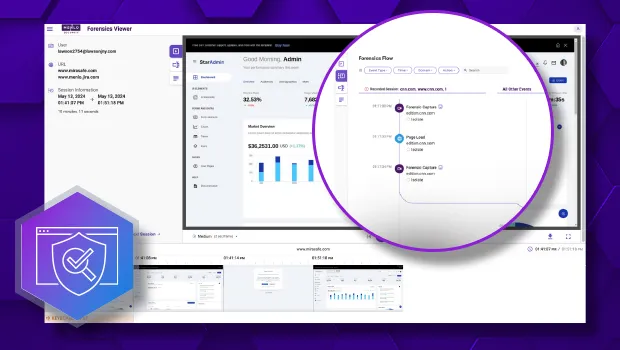
Menlo Security provides the crucial data needed for effective security operations. By capturing a contextual forensic record of user activity within applications, you eliminate the blind spots common in traditional encrypted traffic. These deep insights are available instantly via Browsing Forensics, centralized dashboards, and logs. These insights are fully integrated with your existing SIEM/SOC solutions, enabling rapid incident investigation and simplified compliance auditing.
Your Browser Is The Remote Access Client

By adopting a cloud-delivered application access architecture, organizations gain proven security while dramatically reducing operational complexity and cost.

Menlo SAA is cloud-delivered and clientless. Access is granted instantly via any standard browser, eliminating all hardware dependencies, client software installation, and the need for time-consuming network restructuring.
Learn Why Menlo SAA Is a Leader in Zero Trust
Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
Security and IT leaders face diverse challenges, from securing contractors and users on unmanaged devices to eliminating costly VDI. Menlo Secure Application Access is designed to adapt to your operational reality, providing tailored solutions across every key access scenario.

The high risk of malware and data loss from unmanaged devices forces costly VDI and complex agent solutions. Menlo Secure Application Access eliminates this trade-off by enforcing network separation, stopping the potentially compromised client from infecting the network and the application servers, and maintaining precise control over enterprise data. This approach provides key outcomes, allowing you to eliminate application-layer threats, prevent unauthorized data uploads and downloads (DLP), reduce VDI/VPN operational costs via agentless consolidation, and accelerate business value by onboarding contractors in minutes.
VDI has a high total cost of ownership and high complexity, frustrating users with chronic latency and slow logins. Menlo Secure Application Access eliminates this burden by replacing desktop virtualization with a single, cloud-delivered, clientless solution. This shift delivers superior user performance and simplifies IT architecture, resulting in three key outcomes: reduce VDI TCO by up to 80% by eliminating infrastructure, improve user experience with native-like performance, and free up specialized IT resources from maintenance overhead.


Achieving true zero trust is often undermined by the lateral movement risk of VPNs and the complexity of legacy ZTNA. Menlo Secure Application Access eliminates this exposure by enforcing true least privilege access at the application layer. This simplified approach reduces the overall attack surface and accelerates compliance against CISA Zero Trust models.
Learn How the Menlo Solution Aligns with the Technical Requirements of the ZTMM 2.0
Traditional VPNs pose a major risk with broad network access while frustrating users with latency. Menlo Secure Application Access provides a clientless solution, enabling granular application-by-application access, and by delivering cloud-native speed. This results in drastically reducing the external attack surface, improving application performance, and eliminating the high costs and complex maintenance of VPNs while providing the deep visibility your team needs for complete control.

Answers to the burning questions in your mind.


No. While Menlo Secure Application Access is primarily designed to deliver secure, clientless access to modern web and SaaS applications via any standard browser, it also provides options for non-browser applications. The Menlo Security Client enables access to legacy client-server applications.

Yes. Menlo Secure Application Access is designed to integrate seamlessly with your existing Identity and Access Management (IAM) infrastructure. It supports all major industry standards, including SAML 2.0 and OpenID Connect, allowing it to integrate out-of-the-box with popular Identity Providers (IdPs) like Microsoft Entra ID (Azure AD), Okta, Google Workspace, and others. This ensures consistent authentication (SSO) and Multi-Factor Authentication (MFA) enforcement across all applications.

Menlo SAA goes beyond where ZTNA falls short by eliminating the complexity and inherent risks of legacy ZTNA. Menlo SAA is fundamentally different because:
It delivers zero trust access without requiring complex network changes, firewall rules, or any endpoint agent.
The Menlo Cloud creates a protective barrier, guaranteeing that no application code or data ever executes on the user's endpoint.
It allows enterprises to implement zero trust access with speed and ease, moving beyond the high complexity of legacy ZTNA solutions.

Menlo Secure Application Access (SAA) is a solution that provides policy-driven, zero trust access to internal and web-based applications and data for both managed and unmanaged devices. It simplifies zero trust access, protects applications and data, and enables organizations to reduce their dependency on costly legacy infrastructure like VDI and VPNs. The solution ensures least-privileged access by limiting permissions by user, group, location, and application.

Menlo provides secure access by routing all user traffic through the Menlo Cloud. This shields the application from a potentially compromised endpoint. For browser-based applications, it offers clientless, zero-touch deployment, making it simple to provision secure access for users, including contractors and BYOD users.

Yes, Menlo Secure Application Access is built on zero trust principles, focusing on granting access only to the specific applications a user requires, not the whole network. It enables fine-grained and conditional access policies defined by users, groups, source IPs, and geographies. The architecture ensures continuous enforcement and protection, delivering least-privileged access that is simple to deploy, even for remote and BYOD users.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.