Menlo Security Named a Leader & Outperformer in the GigaOm Radar for ZTNA
Learn Why

Traditional detection-based security tools, including AV, EDR/EPP, firewalls, IDP/IPS, and SWGs/CASBs fail to address new zero-day threats because their reactive approach relies on signatures and IoCs, limiting their effectiveness to only attacks that have been seen before. Even AI tools integrated into these traditional systems are typically trained on existing attacks and Indicators of Compromise (IoCs), fundamentally limiting their ability to stop zero-day threats and giving enterprises a false sense of security. While many enterprises have attempted to improve browser security, they continue to focus on improving security at the network or endpoint level, failing to prevent sophisticated malware or advanced phishing threats for a number of reasons including:
While many enterprises have tried to improve browser security, they tend to focus on security at the network or endpoint level. These tools are not equipped to combat evasive threats in the browser and often don’t even see them until it’s too late.
Explore the latest browser security threats like AI-driven phishing and zero-day exploits with Menlo Security's 2025 report.



Menlo is the first and only proactive solution to stop browser-based attacks in the cloud, guaranteeing they never reach your network or endpoint. No software or infrastructure changes are required. The Menlo Cloud isolates browser traffic, disarms and sanitizes malicious files, and provides AI-powered on-click inspection that blocks evasive threats, including impersonation and fraudulent sites, as well as polymorphic phishing and malware attacks. We integrate seamlessly with all leading network and endpoint security solutions for complete, unified protection. This preventative approach delivers safe browsing and provides access to fully functional files and archives, while preventing security and identity compromise from emerging evasive threats.
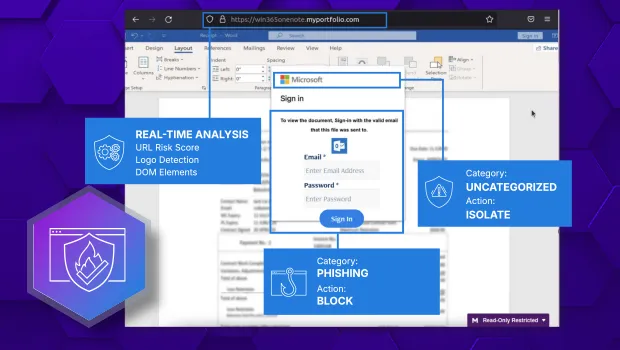
HEAT Shield AI is the only AI-powered, proactive defense that redefines browser security by stopping zero-day phishing attacks and evasive social engineering threats. Its high-efficacy model delivers an effectiveness rate of 90%+ detection of zero-day attacks, preventing threats like polymorphic phishing and brand impersonation attacks long before signature tools can identify them. What further sets it apart is the integration with Google Gemini's advanced generative AI analysis. No other security solution on the market can provide the same deep integration and level of visibility, providing an unparalleled, multi-layered defense against today's most dangerous attacks.
The Only Solution You'll Ever Need to Stop Phishing Threats
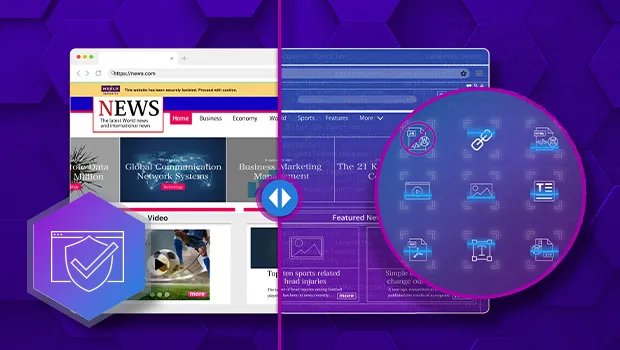
Menlo's foundational technology dynamically builds a hardened digital twin of the user's browser in the cloud, where patented Adaptive Clientless Rendering technology executes active web content and sends only safe, sanitized HTML to the user's browser for endpoint rendering. This advanced browser isolation technology eliminates zero-days and highly evasive threats posed by malicious embedded code, significantly reducing bandwidth consumption. Menlo delivers security without compromise, ensuring a seamless user experience on any browser, and on any device.
Prevent Active Code Attacks and Malware Detonation
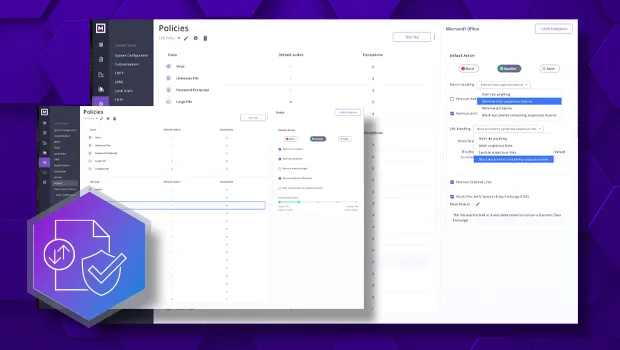
Menlo File Security takes cloud content inspection a step further by assuming all files are malicious. It is powered by Level 3 Content Disarm and Reconstruction (CDR), which uses patented Positive Selection® technology to disarm and reconstruct files. This delivers clean, safe content to the user while maintaining the file's full functionality and original format.
Stop Known and Unknown Threats in 220+ File Types, While Safely Preserving Macros
Traditional security tools can't detect evolving AI-powered phishing and brand impersonation attacks. Menlo HEAT Shield AI, now with Google Gemini, provides proactive, in-browser defense to block these never-before-seen threats in real-time, with no endpoint agent required.




Menlo Security Stops Unknown Phishing Attacks Up to 6 Days Before Other Security Vendors
Menlo Security HEAT Shield AI provides the ulitimate first line of defense against Highly Evasive and Adaptive Threat (HEAT) attacks, delivering superior, preemptive protection that legacy tools can't match. Integrated with Google Gemini models, Menlo's AI-powered engine uses real-time analysis to proactively stop even the most sophisticated zero-day phishing and brand impersonation attacks designed to bypass traditional defenses. The result is frictionless deployment with an invisible defense that stops threats before any malicious content ever reaches the user or endpoint.
Menlo Eliminates the File Security Gap, Ensuring no File-borne Threats ever Reach the Endpoint
Menlo delivers a powerful two-pronged defense against evasive malware and ransomware delivery right from the cloud. Its core benefit is a clientless architecture, where a secure, digital twin of the user's browser executes all active web content in the cloud—including malicious code—ensuring no threats ever reach the endpoint. This robust security extends across the enterprise: it addresses browser threats through isolation, secures file-based threats with hash checks and sandboxing, and offers patented CDR technology to proactively clean and deliver safe, fully functional files (including password protected files and nested archives), while also addressing email link threats.
Menlo Blocked More Than 170,000 Zero-Day Phishing Attacks Over the Last 12 Months
Menlo's preemptive Cloud architecture transforms the browser from a security blind spot into a source of intelligence, giving your security team unparalleled visbility into every user session. By embedding enterprise defense directly inside the Menlo Cloud, you gain access to deep, informative web logs and built-in analysis tools without needing endpoint software. This visibility powers Menlo Browsing Forensics, a key benefit that provides actionable, high-fidelity data, including a complete record of user activity and inputs during targeted attacks. This full picture of exposed assets significantly accelerates the incident response process, drastically reducing the time it takes your team to understand and contain a security incident.
Menlo Security Reduces SOC Alerts by Up to 80%.
Menlo Threat Prevention is engineered to deliver a seamless experience that benefits both your security teams and your users. The solution is designed to drastically reduce overhead by eliminating the alert noise and false positives that overwhelm your team, freeing them up to focus on high-level strategy instead of manual investigations. You benefit from effortless, fast deployment because the solution is entirely client-free, requiring no new endpoint software or hardward to manage. Best of all, your users experience zero-friction productivity as they can continue using their preferred browser (such as Chrome or Edge) without any noticeable performance degradation, latency, or disruption since the complex security work happens invisibly in the Menlo Cloud.
Effective Data Loss Prevention starts by preventing the breach in the first place. Learn how Jacobson Holdings used browser isolation to stop the web-based threats that lead to data theft, strengthening their defense-in-depth strategy before sensitive information could ever be put at risk.

Discover why organizations around the world rely on Menlo Security to protect the enterprise and enable secure access to applications, preventing attacks that legacy security tools cannot stop.
Traditional endpoint and network security tools are proven to fail against evasive threats targeting users through the browser. Prevent even the most sophisticated phishing and malware threats with Menlo Security.

Sophisticated phishing and social engineering attacks leverage the browser to steal credentials and compromise identity—a threat that legacy defenses simply cannot see. Menlo HEAT Shield AI, integrated with Google Gemini, shuts this down. The solution is clientless and requires zero configuration, instantly providing high-efficacy defense. Attacks are automatically detected in the cloud using AI-powered computer vision and powerful multimodal reasoning to inspect both visual and structural web page elements, instantly blocking zero-days and social engineering attacks before execution.
For security teams using Menlo's HEAT Shield AI, eliminating browser-based attacks becomes seamless and proactive. Operations are highly efficient, delivering easy visibility and forensic logging, which integrates seamlessly with leading SIEMs (like Splunk, CrowdStrike) and Google Threat Intelligence, making reporting and threat investigation a snap. This preventative workflow guarantees that credential theft and malware delivery never reach the endpoint, ending the initial breach and securing identity.
Attackers leverage the browser as the primary vector for evasive ransomware, using tactics like HTML smuggling and password-protected files to bypass your detection-based security. The Menlo Cloud takes a Zero Trust approach, executing all web traffic and code remotely in the cloud. This preventative approach is reinforced by Level 3 CDR technology, which sanitizes every download, ensuring that no malicious code or evasive payload ever reaches the endpoint, guaranteeing endpoint immunity against encryption and double extortion. With Menlo, file security is easy and fast, with the full power of CDR protecting both web downloads and email attachments. It operates seamlessly, requiring no complex configurations or time-consuming support, providing comprehensive defense across both of the most critical threat vectors.
Answers to the burning questions in your mind.


Menlo HEAT Shield AI with Google's Vertex AI Gemini models delivers preemptive protection against zero-day phishing attacks and highly evasive threats. This advanced phishing and social engineering prevention engine provides real-time analysis of browser sessions and dynamic web content. Its high-efficacy model delivers an effectiveness rate of 90%+ detection of zero-day attacks, catching threats long before conventional signature tools can identify them. HEAT Shield AI is designed to see beneath the surface of seemingly benign traffic and content to find attacks that cannot be seen by users, including zero-day phishing, imposter websites, and brand impersonation.

Traditional detection-based security tools, including AV, EDR/EPP, firewalls, IDP/IPS, and SWGs/CASBs fail to address new zero-day threats because their reactive approach relies on signatures and IoCs, limiting their effectiveness to only attacks that have been seen before.
Menlo Threat Prevention stops all browser-based threats by proactively inspecting web traffic and content before it reaches the user’s endpoint. Because we do not rely on signatures, which only apply to known attacks, Menlo’s AI-driven approach prevents even new zero-day threats, including polymorphic malware, zero-day phishing, and social engineering attacks, long before existing industry protections know they exist.

Menlo Security offers frictionless deployment because our browser security solution is entirely cloud-based, requiring only a simple configuration change (like a PAC file or proxy chain) rather than a complex agent rollout across thousands of endpoints. Furthermore, our architectural focus on prevention means we reduce the alert noise that overwhelms existing SIEM/SOAR platforms, allowing them to focus on genuine threats. We provide rich, high-fidelity data and open APIs for seamless integration with your existing security tools, acting as a powerful threat intelligence solution that complements and makes your current security investments more efficient.

The "protection gap," also referred to as the browser security gap, is the critical blind spot created by traditional network and endpoint security tools that fail to detect evasive browser-based threats. Attackers exploit this gap with increasingly sophisticated threats like zero-day phishing and social engineering attacks not recognized by signature-based defenses. Menlo Security closes this gap by treating all web content as potentially malicious and executing all content in the cloud before it ever reaches the endpoint.
Take a self-guided tour to observe some of the ways that Menlo products enable secure app access, block sophisticated attacks, and provide critical insight into browsing sessions.
See exactly how Menlo can be tailored to solve your unique security challenges. We offer a live demo customized to your teamʼs goals, showing you how to secure your stack and protect your users. A truly secure browsing experience is one click away.