
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


Attackers are exploiting legitimate Remote Monitoring and Management (RMM) tools (like Atera and ConnectWise) to bypass security controls and gain persistent access.
Imagine your organization’s most trusted tools—the ones designed for smooth, remote IT support—suddenly being used as a persistent backdoor for ransomware gangs and state-sponsored spies. This isn't theoretical; it's the reality of Remote Monitoring and Management (RMM) tool misuse, and it represents one of the most dangerous blind spots in browser security. This specific attack flow is just one critical example of how attackers are exploiting the inherent trust placed in legitimate software to bypass your EDR and replacement browsers, gaining ready-made, silent infrastructure for their most devastating attacks.
Legitimate remote monitoring and management (RMM) tools, like Atera Agent and ConnectWise, are increasingly being misused in cyberattacks. There are several benefits from using an RMM to deliver an attack. First, when an attacker uses an RMM as a first-stage payload, it is not malware. It is, in fact, digitally signed and trusted, containing no malicious code until the attacker executes commands. Once these commands are executed, they may well not be immediately caught, because the RMM uses standard, often encrypted protocols to communicate, just as the tool would when used for legitimate purposes, so it is doing what is expected. Making the attack still more difficult to identify, the attacker doesn’t install malicious external software once connected, but uses the RMM’s own console to run native tools like Power Shell or net.exe, making the activity look like a systems administrator performing remote maintenance.
These powerful tools, designed to help internal IT efficiently manage and support systems remotely, offer attackers a powerful, ready-made infrastructure. As these tools are legitimate pieces of software they aren’t detected by EDR or replacement browsers, making it challenging to detect their misuse within an organization—leaving your most critical systems exposed to an invisible, persistent backdoor.
Atera Agent misuse has been notably linked to the APT Group MuddyWater, an Iranian state-sponsored actor, believed to be a subset of Iran's Ministry of Intelligence and Security (MOIS). They have also been linked to RMM Tools, Action1 and PDQ by Group IB.
Qilin, one of the most active ransomware groups in 2025, has also been linked to RMM misuse, specifically installing AnyDesk through ATERA Networks’ remote monitoring and management (RMM) platform and ScreenConnect for command execution, by Trend Micro.
The attack typically unfolds in four critical stages:
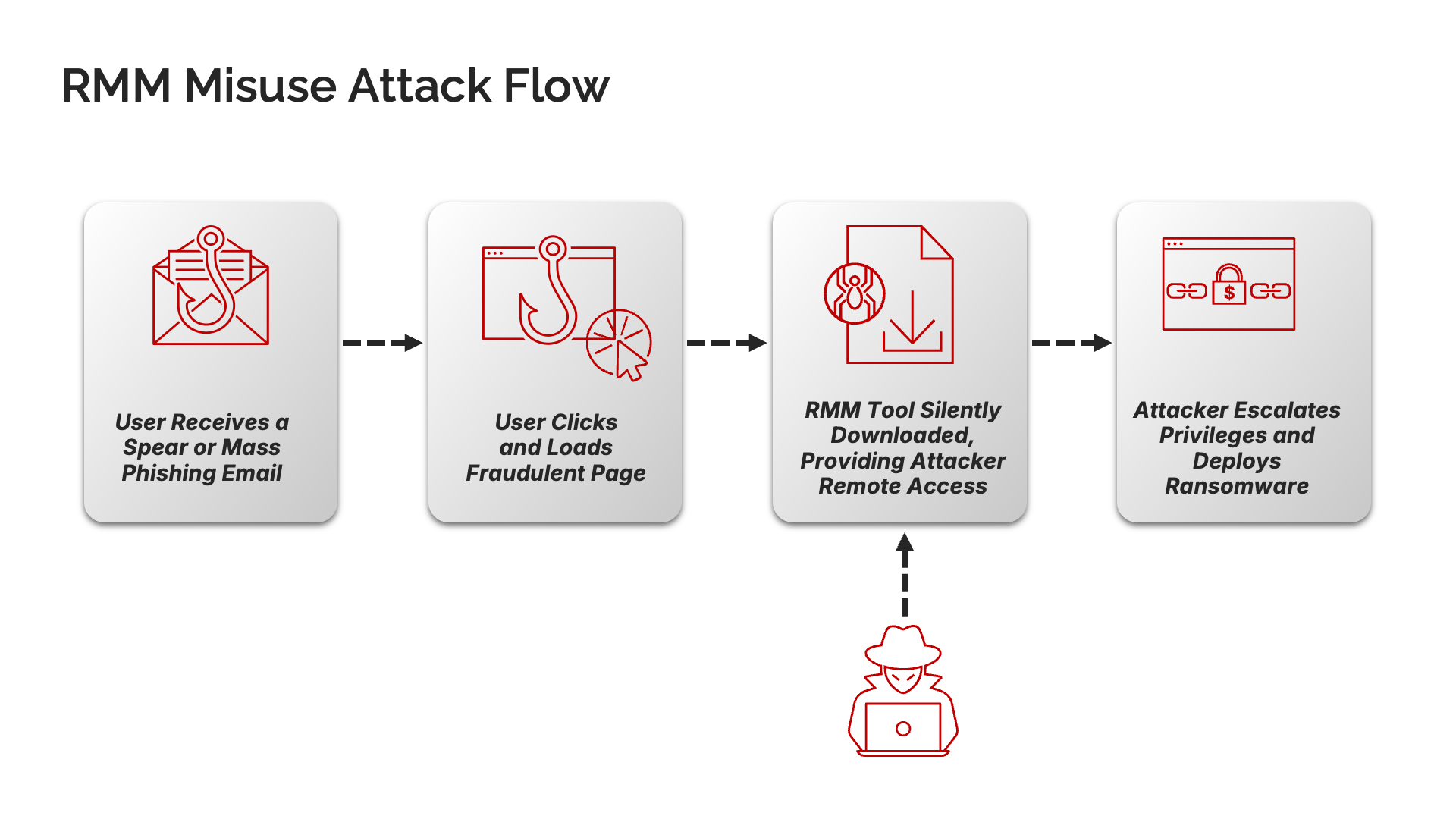
The most frequently observed initial delivery method is email, delivered via both mass phishing and spear phishing exploits. This aligns with findings from threat intelligence reports by X-Force Exchange about the use of Atera Agent and the abuse of ConnectWise—a legitimate IT platform often used globally by Managed Service Providers (MSPs) to manage client networks.
These types of turnkey, high-evasion attacks, often leveraging trusted entities like Adobe or employing evasive tactics like Turnstile CAPTCHAs, succeed because of the inherent limitations of reputation-based security. Many of these threats are issued from newly-created domains, so reputation-based detection methods may fail to catch them. Another vector by which an attacker can take control of an RMM is to exploit unpatched vulnerabilities within the RMM tool itself; there have been at least 4 such instances between 2024 and 2025 alone. A notable example is the malicious use of the ConnectWise installer (dubbed Evilconwi), which leveraged an inherent design flaw—known as Authenticode Stuffing—that allowed attackers to embed XML configuration data, icon resources, and other payloads alongside the signed code. This technique enabled unsigned, behaviourally critical configuration changes within a legitimate, signed binary, effectively bypassing existing security controls. These sites can include automatic downloads, designed so the end user doesn’t have to interact with the malicious page for the payload to execute—ensuring that the initial threat penetrates the network before traditional defenses even recognize it exists.
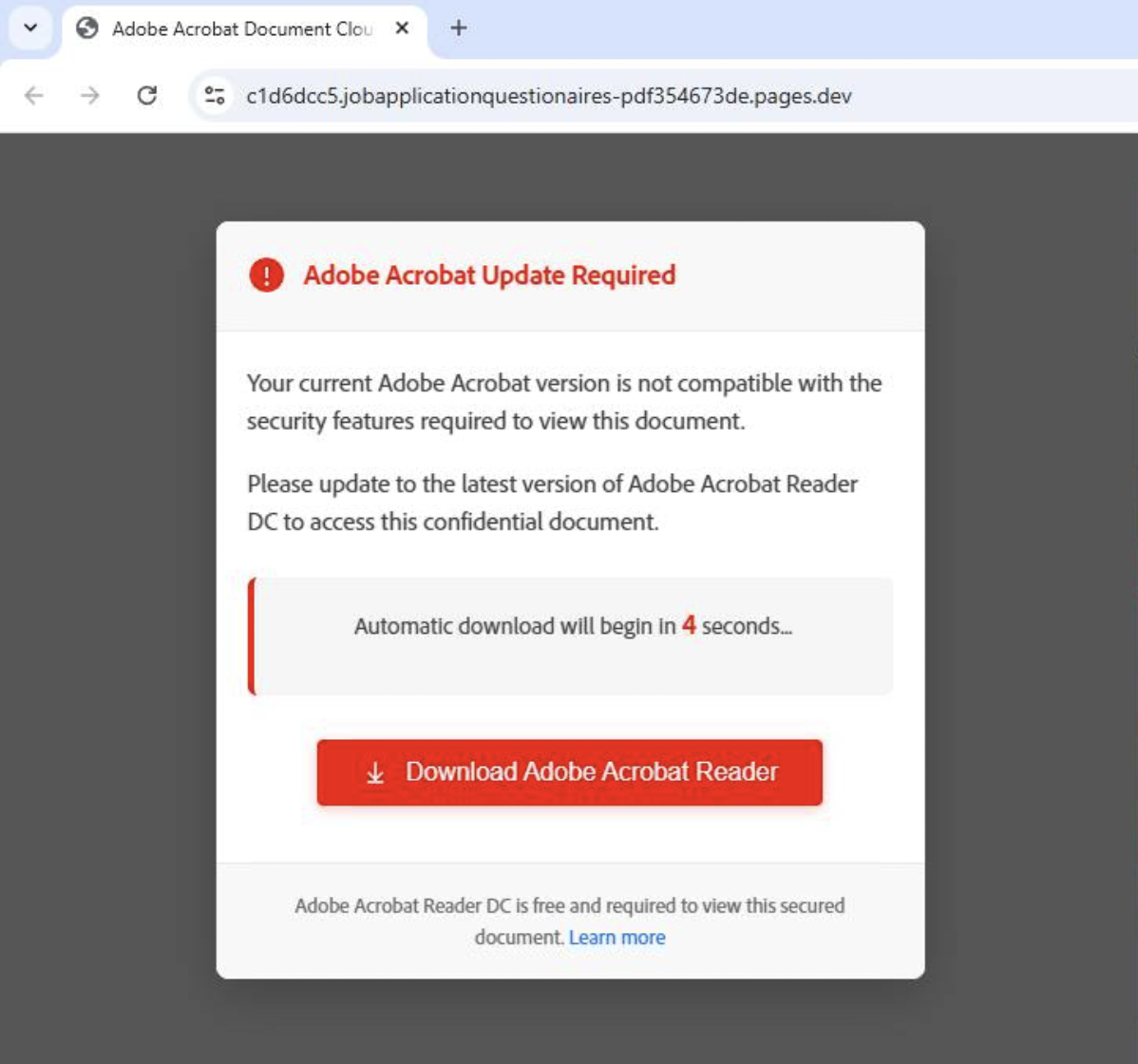
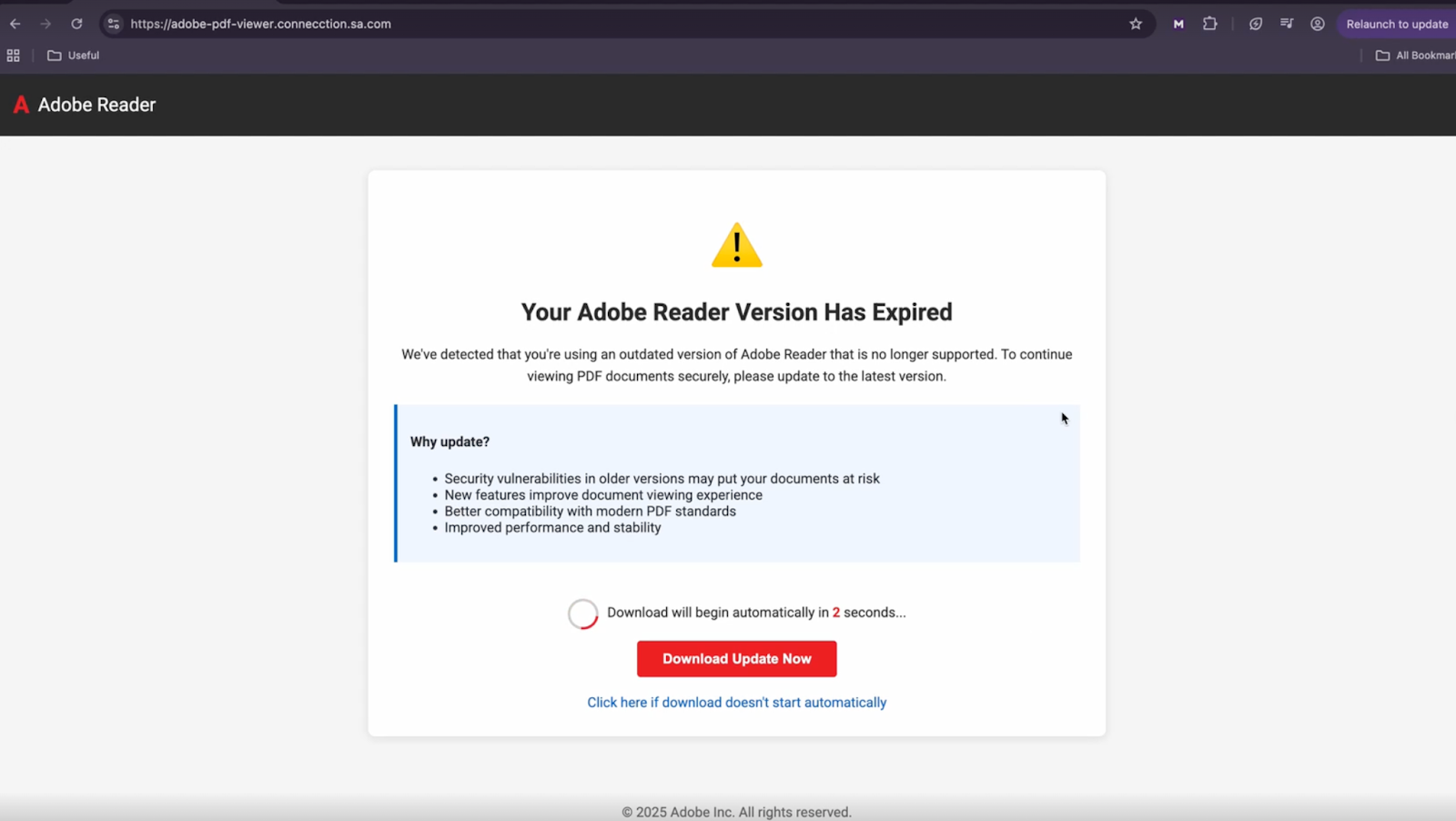
Upon successful download and execution, the threat actor utilizes legitimate RMM tools such as the Atera Agent, or ConnectWise, and takes advantage of free limited time evaluations offered by these vendors. As these tools are legitimate, they are not typically detected by EDR or replacement browsers failing to determine the true nature of these payloads. These tools provide the attackers with persistent remote access to the compromised system, serving as a critical stepping stone for further malicious activities.
With initial access established, the threat actor has a multitude of options for exploiting the compromised environment. This could involve selling initial access, particularly when targeting large enterprises due to the potential for significant financial gain. Crucially, the misuse of legitimate RMM tools has been strongly correlated with the most devastating outcomes, including major ransomware attacks. For example, groups like Qilin—one of the most active ransomware operations in 2025—have been observed leveraging RMM misuse to deploy ransomware payloads. Further actions may include escalating privileges within the network, deploying ransomware, disseminating various types of infostealers, among other possibilities depending on the attacker's objectives.
Menlo Security provides the definitive answer to the RMM misuse problem. While this highlighted attack demonstrates the critical failure of detection-based security (EDR, Antivirus, and Replacement Browsers), Menlo detected it at click-time. This is possible because we don't rely on known threat signatures or IoCs; instead, Menlo HEAT Shield AI with Google Gemini shifts the focus to real-time intent analysis. By leveraging advanced Generative AI to visually and contextually inspect the page, Menlo instantly identifies the social engineering and fraudulent intent, ensuring the attack is blocked before execution. This preventative approach effectively cuts off the attacker's supply chain, guaranteeing zero-day protection and preventing the trusted RMM tool from ever being launched from a malicious source.
Menlo Security
