
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


Lockbit originally began in 2019 and functions as ransomware-as-a-service, meaning criminals are able to pay them a deposit for the use of their malware and then if successful they share the ransom paid by the victims.
In an ambitious effort to combat one of the most notorious ransomware groups, the UK National Crime Agency (NCA) spearheaded Operation Cronos, targeting the Lockbit ransomware gang. This operation, a significant stride in the ongoing battle against cybercrime, aimed to dismantle the infrastructure of the Lockbit gang, known for its widespread and damaging attacks.
Operation Cronos saw the NCA successfully infiltrating and seizing control of servers belonging to Lockbit, specifically their dark web leak site. This move was intended to disrupt the operations of the ransomware group, which has been responsible for numerous cyberattacks across the globe. The operation's climax was reached on February 20th, a day after Lockbit noticed anomalies in their systems, signaling the effectiveness of the task force's actions.
Despite the setback, Lockbit was quick to respond. Through their blog and Telegram channel, they issued several statements highlighting the resilience of their operations:

In a bold move to demonstrate their defiance, a Lockbit member uploaded a "voice memo," signaling that the group was not intimidated by the FBI's efforts. They also posted on their blog a little response to LEA claims of the group.

Earlier this year, LockBit shared a photograph of a young man whom they claim is believed by US intelligence agencies to be associated with their group.
In a bold retort, a LockBit member stated that they have neither seen nor heard of the man in question, but humorously added that should they come across any information about him, they would not hesitate to claim the reward offered by US intelligence for such information. This incident underscores LockBit's brazenness and their intent to publicly challenge and ridicule law enforcement's attempts to penetrate their operations.
The photo below is a photo stock image, the model appears to work for DGL Images. We found more than 200 sites using this image, suggesting it's a fake story to undermine US intelligence efforts.

The swift recovery of LockBit, taking reportedly five days to restore their operations after an attack, is a testament to their operational maturity. This rapid bounce-back capability indicates several key aspects of LockBit's organizational resilience:
By maintaining more than one backup location, LockBit demonstrates a well-thought-out strategy for data redundancy. This not only minimizes their downtime in the event of an attack or seizure but also ensures that critical data and infrastructure can be quickly reinstated.
The existence of possible staging locations further highlights LockBit's foresight in planning contingencies. Staging locations can serve as launchpads for restoring operations swiftly, indicating that LockBit has invested time and resources into developing a robust recovery process.
The ability to recover quickly from disruptions is a hallmark of operational maturity. It reflects a high degree of resilience, with established procedures and resources in place to respond to incidents effectively.
The technical skills required to execute such a rapid recovery are substantial. It suggests that LockBit possesses not only the technical know-how but also the operational discipline to manage their resources effectively.
The effort to ensure minimal operational disruption reveals LockBit's commitment to maintaining their activities and relationships with affiliates. It underscores the importance they place on business continuity, even in the face of law enforcement actions.
The quick recovery of LockBit after Operation Cronos showcases their operational maturity, preparedness, and resilience. It signals to the cybersecurity community that LockBit is a sophisticated and well-organized adversary, capable of sustaining its operations despite significant external pressures.
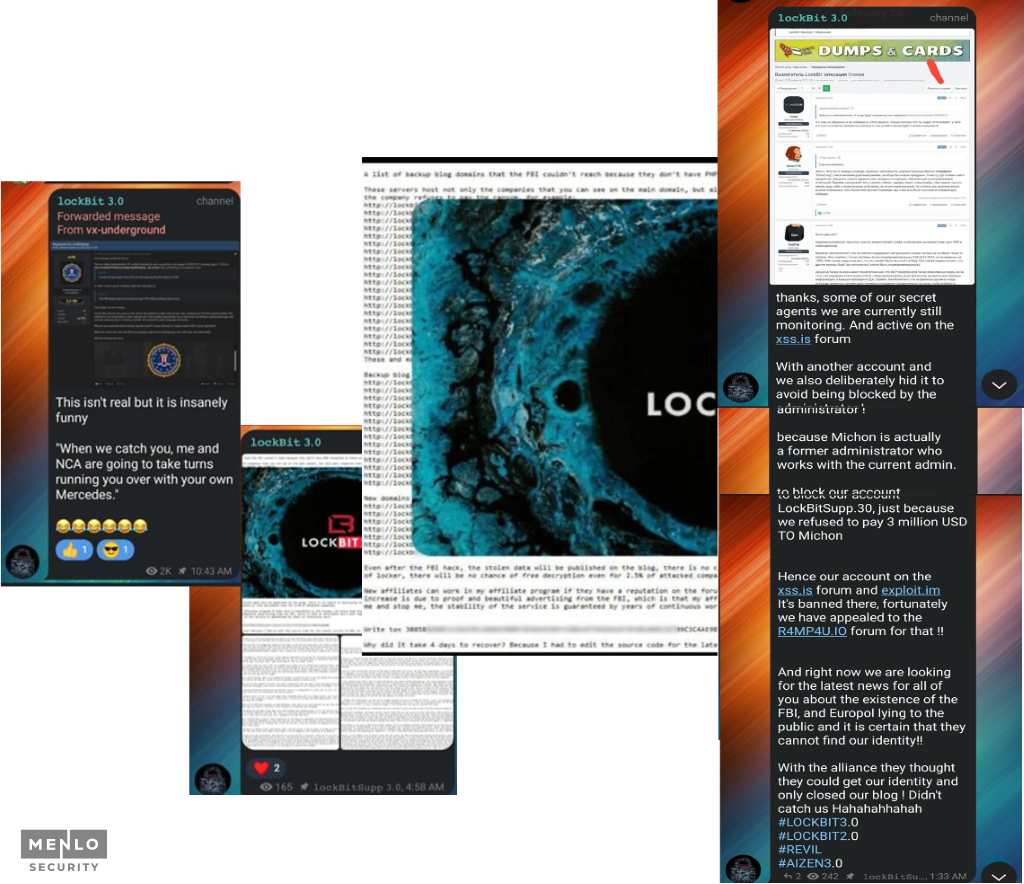
A closer examination of Lockbit's communications and activities reveals several key insights into their operations:



LockBit has established a significant and enduring presence within the Dark and Deep Web, fostering a pseudo-community that rallies around its brand. Some supporters have even tattooed the LockBit logo on their bodies in allegiance.
The Lockbit PR team actively engages in discussions about current events, reflects on the demise of rival entities like Conti, and participates in exchanges with both allies and adversaries. This deliberately cultivated community undoubtedly contributes to LockBit's capacity to secure not only loyal affiliates but also informants and collaboration opportunities with other threat groups and ransomware gangs.
While they do have a large following there are some who took the opportunity to troll the ransomware gang.

While we see Lockbitsupp facing recent bans from multiple dark web sites, including one for a payment dispute in which a threat actor ‘sold’ their initial access into a network to Lockbit, their popularity and activities show no signs of decline. In a specific instance from late January 2024, Lockbit allegedly failed to pay a ransom after the victim had already paid, indicating they don't appear to slow down their popularity or antics.

The saga of Lockbit's encounter with Operation Cronos sheds light on the resilience of large threat groups in the face of law enforcement efforts. Despite significant actions taken by the NCA and its partners, Lockbit's quick recovery and continued operations highlight the challenges of combating cybercrime. This incident not only underscores the sophistication and preparedness of ransomware groups like Lockbit but also the necessity for continued vigilance and innovation in cybersecurity strategies to counter such threats effectively.
Menlo Security
