
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


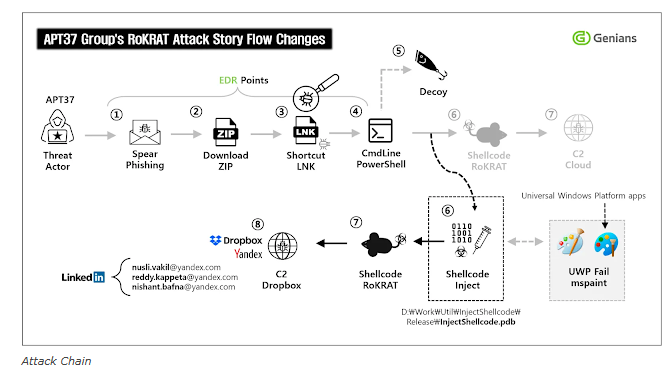
The cybersecurity community is once again watching APT37, a North Korean-linked threat group, as it launches spear-phishing attacks that lure unsuspecting users into downloading malicious files.
Recent tactics include:
https://cybersecuritynews.com/apt37-hackers-weaponizes-jpeg-files/
According to Cyber Security News, the CHM and LNK files act as droppers — a common trick used by sophisticated threat actors to bypass conventional detection and gain a foothold in target networks before downloading the malicious payload for further compromise and control.
Detection and response is an important layer of any proper cyber defense architecture. But when prevention is lacking, it causes overwhelming alerts and fatigue on the backend, leading to unrealistic expectations on the SOC even when powered by AI-driven tools.
What’s needed is a balanced, prevention-first approach: one that can stop the threat before the user even sees it.
That’s where the integrated approach of browser isolation and data security comes in — delivering real-time protection without relying on threat detection or user judgment or bias in AI.
APT37’s recent campaign illustrates a classic cyber kill chain:
But here’s what happens with browser & data security in place.
Step 1: The Malicious Email Attachment — Disarmed by CDR
If a user receives an archive with multiple LNK or CHM files (or any other document) as an attachment:
Result: The duplicated file is rendered harmless — even if it was previously weaponized.
Step 2: Weaponized Image or HTML via Dropbox — Isolated Through The Browser
APT37 also hides payloads in image files or HTML content hosted on Dropbox or similar platforms.
Result: The exploit can’t run. The endpoint remains untouched.
This approach delivers true zero-trust file and web access:
As threat actors like APT37 continue to innovate — hiding malware in images, documents, and web content — traditional detection-based tools fall short. You can’t rely on getting updated signatures or wait for alerts after compromises to respond and contain a breach.
With a browser isolation and data security solution, you stop attacks at the source:
This isn’t just another security layer. It’s a new way to eliminate risk — before it reaches your environment.
APT37 and other nation-state groups are raising the stakes. You can’t afford to wait for alerts after a compromise.
See how Menlo Security delivers zero trust web and file security that stops threats like APT37 before the first click:
Menlo Security
