
Menlo Security Acquires Votiro to Deliver Easy, AI-driven Data Security to Enterprises
Read Blog


Qakbot, also known as QBot or Pinkslipbot, is a banking Trojan that has existed for over a decade. It was found in the wild in 2007 and since then it has been continually maintained and developed.
Qakbot has become one of the leading banking Trojans around the globe. Its main purpose is to steal banking credentials (e.g., logins, passwords, etc.), though it has also acquired functionality allowing it to spy on financial operations, spread itself, and install ransomware to maximize revenue from compromised organizations.
The delivery vehicle of Qakbot is usually an email to the victim. This could be either an email attachment or a link in the email. The email attachments generally involve a document that downloads the Qakbot payload. Menlo Labs has been seeing several such strains of Qakbot campaigns recently.
In this blog, we’re going to discuss the different Qakbot campaigns that use various Highly Evasive Adaptive Threat (HEAT) techniques, and we’ll also explain how the Qakbot payload works.
The different HEAT techniques used in Qakbot campaigns identified by Menlo Labs are as follows:
We will provide examples of each of these techniques.
In this campaign, a benign domain is compromised to host the malicious payload, and the link to the payload is sent via an email. To evade existing defenses, Qakbot used password-protected ZIP files, a known HEAT technique. Below is a screenshot that shows the poor detection of these password-protected payloads on VT.

The screenshot below shows the initial access method that Qakbot uses to evade existing defenses.

The attack kill chain is as follows:
The screenshot below shows one of the malicious .lnk download JS files.

The obfuscated JS file decrypts during runtime to download and execute payload from C2, as shown below.

In this campaign, Excel 4.0 macros were used to add commands into spreadsheet cells and send the email attachments to the intended targets.
Below are some examples of emails with attachments using Excel 4.0 macros to deliver Qakbot.

Email showing attachments of Excel file.

Upon opening the XLS document, the user is asked to enable the macro to execute the Excel 4.0 macros.

These commands present in the XLS file download and execute payload from C2.

In this campaign, a CVE-2022-30190 vulnerability (also referred to as Follina) was leveraged to deliver Qakbot. When executed, the document containing the exploit calls out to an external HTML file that uses ms-msdt URL protocol to execute PowerShell code.
Below are some examples of emails with attachments using CVE-2022-30190 to deliver Qakbot.

The following are some examples of documents using CVE-2022-30190 (md5 - 7a91b01a037ccbfe6589161643d0a65a) to deliver Qakbot.

When we open the document, it tries to download the HTML file, which further downloads the Qakbot payload.

HTML (md5 - ea48f95ab4f3ca3b0c687a726cb00c49)

In this campaign, a specially crafted HTML attachment or web page was used to build the malware locally behind a firewall.
Below are some examples of emails with an HTML Smuggling attachment.

In this campaign, the spam email contains an HTML file (md5- 2881945BDF1DB34216CC565FEF4501D4) that was encoded with Base64, as shown.

The “var text” function was Base64 encoded with an Adobe image and a password-protected ZIP file “Report Jul 14 71645.zip” (md5- 5F57C9BF0923DE15046CCB14E41CE0A6 pwd - abc444) that gets constructed on execution, as shown below.

The infection chain of the attack is shown in the following image.

The infection chain of the Qakbot attack using the HTML Smuggling technique is as follows:
Next, we’ll explain the working of Qakbot payload, which uses the ISO file and the components present inside that are responsible for the Qakbot execution.
The ISO file downloaded from the archive contains 7533.dll, calc.exe, Report Jul 14 71645.lnk, and WindowsCodecs.dll.

The functionality and details of the file are as follows:
Upon executing the ISO file, the .lnk file executes calc.exe and uses .dll sideloading to load WindowsCodecs.dll, which then loads 7533.dll (Qakbot) using regsrv32.exe.
To detonate the Qakbot payload, the DLL sideloading attack evasive technique is used. Using this technique, calc.exe loads the masqueraded WindowsCodecs.dll to load 7533.dll using regsv32.exe, as shown below.

This final payload finally injects its malicious code into the wermgr.exe.

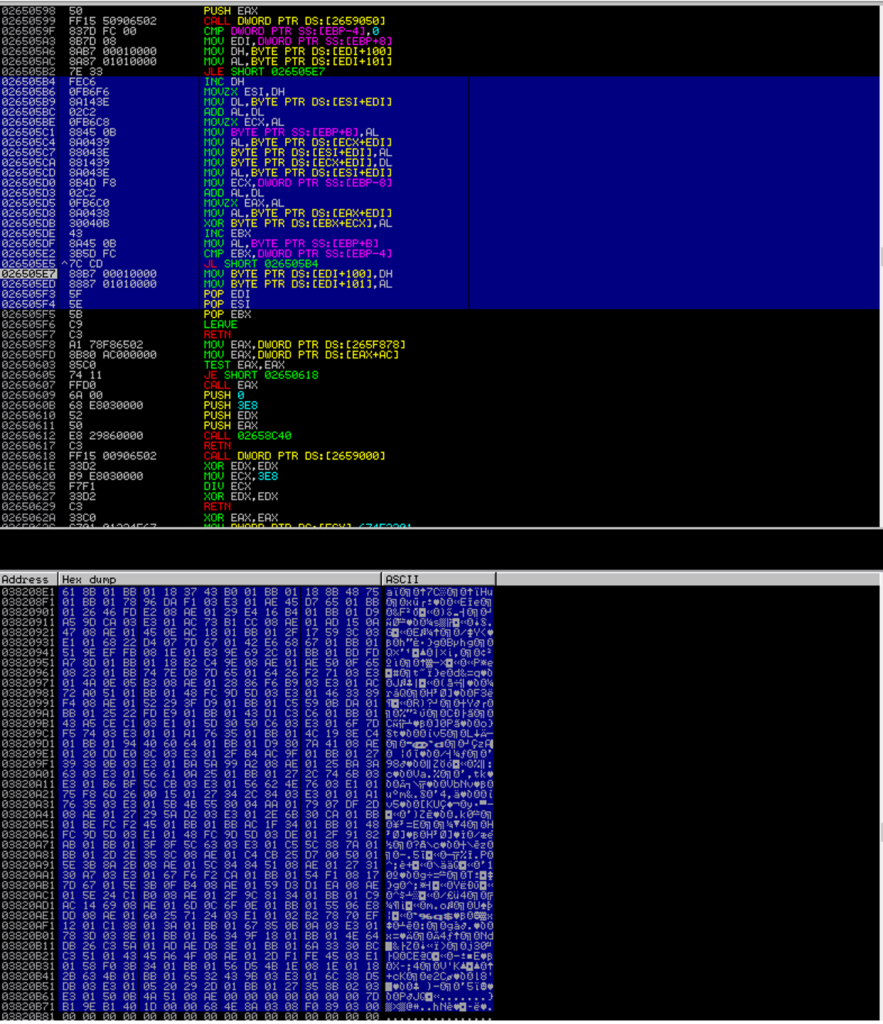
The Qakbot payload using regsrv32.exe to load the .dll file is packed using a runtime packer. The packer involves an XOR decryption to get the unpacked version of Qakbot, as shown below.

The unpacked payload is a 32-bit .dll file compiled on June 21, 2022.

This unpacked binary stores the C2 and Botnet ID in the resource section RCDATA (3C91E639 - C2, 89210AF9- Botnet ID).

It uses RC4 to decrypt its C2 and Botnet ID present in the resource section, as shown below.
We created a Python script (shown in the Appendix) to decrypt the Botnet ID and C2 using RC4. The binary we analyzed was using BotnetID Obama 201.

Customers using Menlo are protected against the initial access, thereby preventing endpoint infection.
The Menlo Platform protects against the following HEAT techniques employed by the Qakbot malware:
The Menlo Platform opens all documents and archives downloaded from the Internet in the Isolation Core™, away from the user’s endpoint device. Malware actors commonly password protect malicious payloads to evade security defenses. If a download is password protected, then the Menlo Platform prompts a user to enter the password. Once the password is provided, the platform inspects the file and ensures that it’s safe for download.
The Menlo email product wraps any attachments received from outside the organization. The wrapped attachment is then opened in the Isolation Core™, where the document is converted to a safe version that can be viewed by the user, while the inspection engines determine whether the file is good or bad. Policies can also be configured to ensure that all documents downloaded from the Internet are always viewed, or that a SAFE version of a document is downloaded to the endpoint. Menlo’s Safedoc feature strips out all active content, thereby ensuring that any malicious aspect is removed.
Follina is the name given to the exploit that takes advantage of Microsoft Diagnostic Tools to fetch and execute remote code. The Menlo Platform opens all documents and archives downloaded from the Internet in the Isolation Core™, away from the user’s endpoint. The document is converted to a safe version that can be viewed by the user, while the inspection engines determine whether the file is good or bad. Policies can also be configured to ensure that all documents downloaded from the Internet are always viewed, or that a SAFE version of a document is downloaded to the endpoint. Menlo’s Safedoc feature strips out all active content, thereby ensuring that the malicious aspect is removed.
The goal of HTML Smuggling is to make use of HTML5/JavaScript features to deliver file downloads, and it usually comes in two flavors:
While Qakbot uses HTML Smuggling via email attachments, Menlo Security has identified many malicious campaigns using the web vector for HTML Smuggling. A malicious payload that gets downloaded to the endpoint via HTML Smuggling evades all network inspection, because the payload is constructed on the browser. The Menlo Isolation Core™ has visibility into all types of JS and payloads constructed on the browser, and thus detects and blocks these kinds of attacks when delivered via the web vector.
In this post, we have showcased the different HEAT techniques used by Qakbot campaigns we analyzed. Customers using the Menlo Isolation platform are protected.
—----------------------Config Decrptor—-----------------------------------
import hashlib
from arc4 import ARC4
import struct
import socket, sys
key = b"\\System32\\WindowsPowerShel1\\v1.0\\powershel1.exe"
key = hashlib.sha1(key).digest()
print(key.hex())
file_res = open(sys.argv[1],"rb+") # c2 data from resource section
file_data = file_res.read()
file_res.close()
rc4 = ARC4(key)
data = rc4.decrypt(file_data)
print(data)
if len(data) > 70:
data = data[20:]
out = ""
while data:
flag, ip, port = struct.unpack(">BLH",data[:7])
ip = socket.inet_ntoa(struct.pack('!L', ip))
data = data[7:]
out += "{}:{}\n".format(ip,port)
print(out)

Menlo Security
