Menlo Security Now Leverages Gemini AI for Advanced Phishing and Ransomware Prevention
Read Blog


The cybersecurity world is defined by Zero-Day exploits and Highly Evasive and Adaptive Threats (HEAT), rendering old "detect and respond" defenses blind. Simultaneously, the explosion of remote work has created unacceptable risk with legacy VPNs and agent-based ZTNA tools, particularly with unmanaged devices. The problem is that nearly all threats—from web links and email to data exfiltration via Gen AI—converge in the browser, making it the single most important place to focus security efforts. Menlo Security solves this with the only Cloud-delivered Browser Security Solution, which completely eliminates risk by executing all content harmlessly in the cloud. This unified approach delivers the only true path to guaranteed zero-day threat prevention, frictionless remote access for all unmanaged devices, and precise data security controls required for safe Generative AI use.
Menlo offers the first and only solution that prevents zero-day exploits and highly evasive threats from ever reaching the endpoint. These protections are more vital than ever, as attackers are increasingly adopting the adversarial use of AI to come up with new or dramatically adapted threats. Using the Menlo Cloud, we execute all web traffic inside a hardened digital twin of the user’s browser in the cloud. We deploy HEAT Shield AI with Google Gemini for advanced generative AI analysis and on-click inspection, stopping even the most sophisticated attacks designed to bypass reputation-based security tools. You get safe, high-fidelity browsing and fully functional, sanitized files, all with no software or infrastructure changes required.
Key Preventative Use Cases:

Menlo Secure Application Access (SAA) is a zero trust, cloud-delivered solution providing effortless and safe access for your hybrid workforce.
Menlo SAA is the one solution for managed, unmanaged, and BYOD access, eliminating complexity and risk. Its core function is to act as a protective shield: an unmanaged or compromised device can never infect an enterprise application.
Menlo SAA is easy to deploy, eliminates VPN risks and VDI complexity, and is significantly more cost-effective and cheaper than ZTNA and VDI. It delivers a superior, consistent user experience through any browser, with no client software required, ensuring users are productive and secure.
Key Use Cases:
The Gen AI frontier is open. Don't just join the revolution— secure it.
Safe and appropriate use of Gen AI inside the enterprise requires three complementary elements—last-mile DLP with browser context, a method to steer users to sanctioned tools and away from those that are not, and policy monitoring to ensure that policies are working. Menlo has these features built-in.
Menlo has all the tools that you need to minimize the risks of Gen AI use in the browser. With Menlo, you can enable granular access by user and group. You can enable DLP protections inline for all users, including those on BYOD or unmanaged devices. And all from one console.


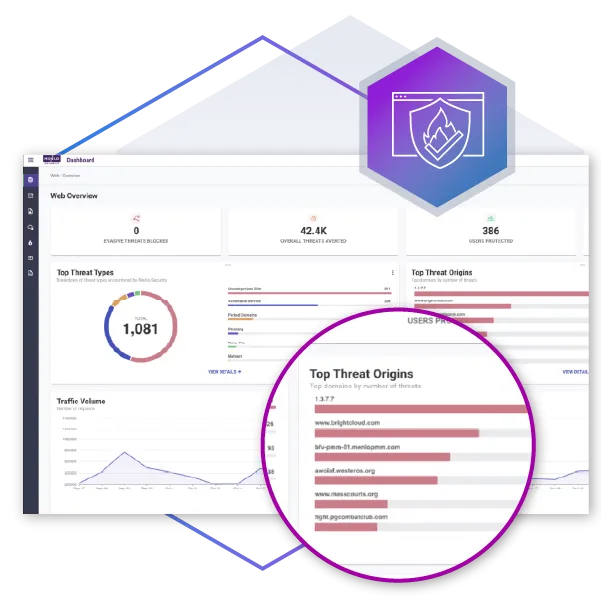
Despite the abundance of network and endpoint security tools, activities that happen in the browser have historically fallen into a blind spot. Security, SOC, and IT teams have had to infer what happened based on the affects of a browsing event downstream. But with Menlo Browsing Forensics, you can see what is happening, in near real time.
As traffic transits the Menlo Cloud, enterprises can quickly view detailed browsing sessions. With Menlo Browsing Forensics, you can choose to record selected browsing sessions, so you can get a near real-time view of how users are interacting with your apps and data, as well as potential phishing sites. This unparalleled visibility slashes incident response time and provides undeniable evidence for compliance and auditing.
Current file security tools force a critical trade-off: block workspace productivity to prevent threats, or trust that detection alone will stop malware from entering in the first place. This is unacceptable for modern, file-reliant workflows. For those that can't afford a breach, it's also non-negotiable.
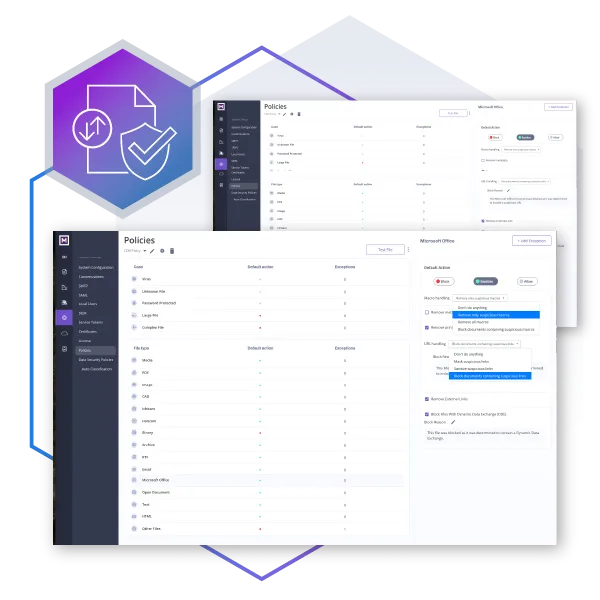
Menlo File Security delivers defense-in-depth by incorporating next-gen Content Disarm and Reconstruction (CDR), antivirus, hash check, and the ability to sandbox into a single solution that works behind the scenes and seamlessly integrates with current infrastructures. This allows end-users to work as normal while freeing security teams to focus on more important matters.
Zero Trust Equals Zero File-borne Breaches
We go beyond traditional CDR tools. Rather than scan for known threats, our patented Positive Selection® technology assumes all files are malicious, immediately detecting, dissecting, and reconstructing a new, clean file using only components guaranteed to be safe. This process eliminates evasive malware, ransomware, and zero-day file exploits (even those hidden in archives or password-protected files) while ensuring the final document retains its formatting and functionality (i.e., macros). With Menlo, both internal and third-party users can safely click, download, upload, and share without delay.
Answers to the burning questions in your mind.


Menlo Security addresses the problem of the web browser being a prime target for threat actors, as it is often the least protected attack surface in the enterprise despite significant cybersecurity spending. Traditional security tools lack visibility into browser traffic and behaviors, making them blind to evasive browser-based threats.

Menlo uses an AI-powered, on-click inspection system and computer vision technology to analyze web content in real-time. Web requests are executed within the Menlo Cloud, and only safe content is delivered to the user's local browser. This allows for the detection and blocking of phishing attempts, even with new URLs or impersonation techniques.

Menlo is easy to deploy and manage, supporting any browser on any device. There's no new endpoint software to manage, and enforcement actions are easily defined and monitored in the admin portal.

Traditional network access solutions (e.g., VPNs and VDI) are costly, complex, provide a poor user experience, and often lack adequate security and visibility.It offers a simpler and more secure way to provide zero trust access to enterprise applications and SaaS.

With Menlo, browser security policies can be deployed in a single click.


Menlo SAA shields applications and users from threats like cross-site scripting, cookie stealing, session hijacking, infected file uploads, and web-borne threats such as LURE attacks and HTML smuggling.
Menlo Security has been the leader in Browser Security for over a decade, offering the only Cloud-delivered Browser Security Solution. This solution transforms any browser into a Secure Enterprise Browser by creating a hardened digital twin of the user's local browser in the cloud. Best of all, there are no new browser installs or software changes required to manage for your users.
Because the browser has been our sole focus, we're able to deliver a powerful solution that provides the comprehensive security you want with the high performance and familiar user experience that your employees require.
