world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

The word from the top is Zero Trust or bust.Although Zero Trust strategies for cybersecurity have been gaining momentum for the past decade, the push for Zero Trust received a giant boost with President Biden’s Cyber Executive Order (EO) of May 2021. A key element of the EO is the recommendation to adopt a Zero Trust architecture (ZTA) for cybersecurity, as outlined in the CISA Zero Trust Maturity Model.
Zero Trust as a concept is easy to grasp. Never trust, always verify. Instead of extending trust to users and entities that are permitted access to a network, a Zero Trust approach continues to suspect that those granted access might still be infected or malicious. The CISA Zero Trust Maturity Model is not the only attempt to codify the concept. Industry analyst firm Gartner created Secure Access Service Edge (SASE), a cloud-based cybersecurity blueprint as detailed in its report, “2021 Strategic Roadmap for SASE Convergence.” 1 NIST, meanwhile, has created its Special Publication 800-207, which details what’s needed to build a Zero Trust cyber defense. And the DoD has gone far to create specifications for a Zero Trust architecture.
While you could spend months reading up on these frameworks, the fact is that you’ve got to get going. There are bad actors out there who would like nothing more than to penetrate your organization and steal your data. If you are embarking on your Zero Trust journey today, here are five recommendations:
It is built on five pillars: Identity, Device, Network/Environment, Application Workload, and Data. Cybersecurity measures are graded across these pillars according to three levels of maturity: Traditional, Advanced, and Optimal. Measure your agency against the model. When taking stock of your agency’s current defenses, you might find you are Advanced for Identity, Traditional for Workload, but Optimal at the Data level.

Source: CISA Zero Trust Maturity Model June 2021
No agency or department is the same and there are many paths to Zero Trust. The Maturity Model provides a framework that will help you set clear and realistic goals. While achieving Optimal status might be possible immediately for some pillars, it might be more distant for others. In general, you should aim to move beyond the Traditional level and into the Optimal level.
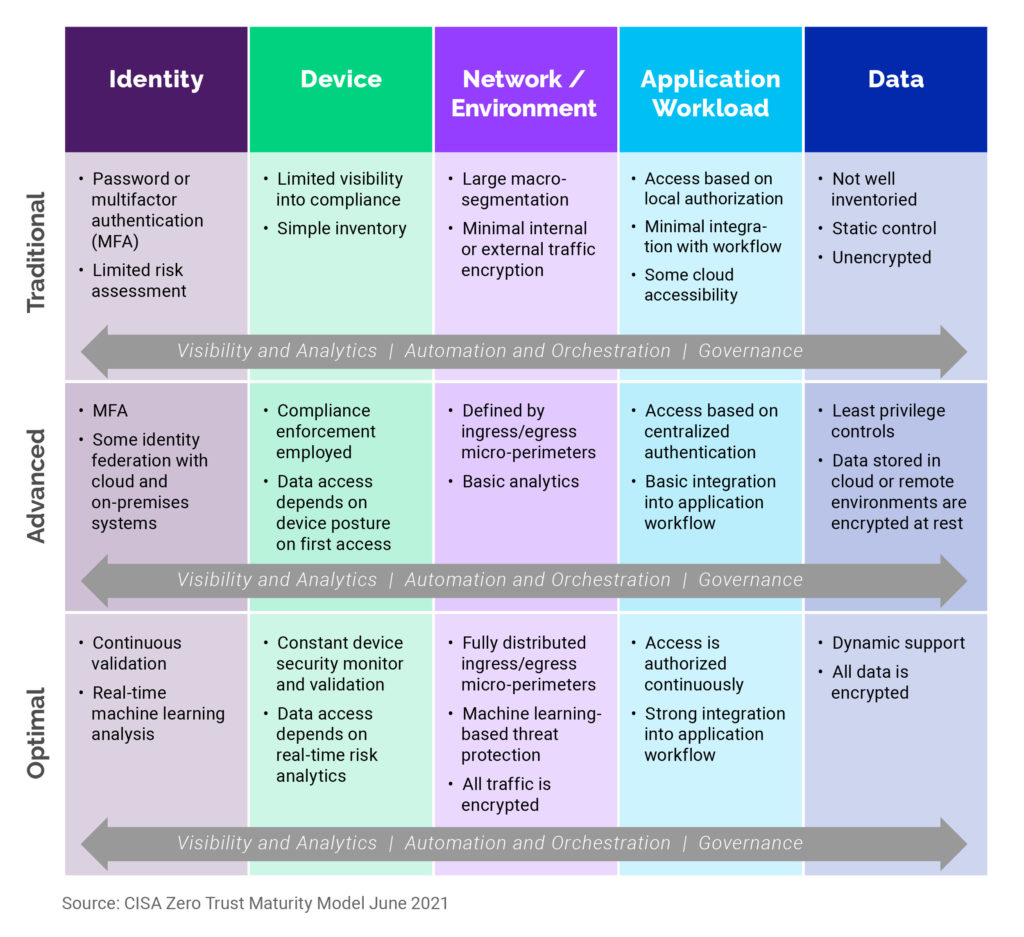
Source: CISA Zero Trust Maturity Model June 2021
Key building blocks are multi-factor authentication (MFA), least-privilege access, and micro-segmentation. But that’s just the beginning. Encryption is essential for critical data, whether in motion or at rest. And a Secure Web Gateway (SWG) is key to making web browsing safe for your agency’s employees. A SWG inspects web traffic, subjecting it to whitelists and blacklists. Suspicious traffic can be sent to Data Loss Prevention (DLP) and sandboxing tools for analysis, detection, and remediation.
Assess the measures you have put in place for effectiveness, looking for opportunities to improve. Achieving the Optimal level could prove challenging, since it calls for encrypting all data and applying real-time machine learning (ML) across several pillars. However, using machine learning to analyze identities, for example, means you can more fully understand the behavior of persons and entities as they access and roam about your network. Not only is your data protected through encryption, but you are always watching over it with the aid of ML.
Consider approaches such as Menlo Security’s remote browser and email isolation, which creates a virtual air gap, preventing malicious web traffic from ever reaching the computers of your agency’s employees. Our technology builds on SWG technology and improves on it by completely isolating web and email traffic from end users. While a SWG applies whitelists and blacklists, Menlo’s cloud-based SWG, powered by an Isolation Core™, goes further by not allowing web or email traffic into your network at all, thus protecting your users not only from known threats but from unknown and future threats as well. Users can see and interact with the data they are accessing, even though it doesn’t reach their computers.
Menlo’s isolation approach is particularly beneficial at a time when many federal employees are working remotely due to the COVID-19 pandemic, and will continue to do so in the future. Learn how Menlo Security isolation enables them to enjoy protection regardless of where they access network resources.
1. 2021 Strategic Roadmap for SASE Convergence, published March 25, 2021, by authors Neil MacDonald, Nat Smith, Lawrence Orans, Joe Skorupa.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
