world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

Menlo Labs is tracking the Russian invasion of Ukraine which has not only escalated substantially physically, but also in the cyber realm. From increased distributed denial of service (DDoS) attacks that impacted both the Ukrainian government and banking institutions, to a new variant of wiper malware named HermeticWiper that was discovered in Ukraine. Shortly after that, a new round of website defacement attacks was also observed impacting Ukrainian government organizations, and Russian ones as well.
Historically, when it comes to Russian cyber activity, everyone is fair game, and we anticipate a continuous rise in activity. We assess with moderate confidence that many may see an increase in scanning, phishing, and other types of SWAG (stuff we all get) attacks on targets outside of the conflict coming from Russia. Menlo Labs also believes with moderate confidence that there will be an increase in scams and phishing campaigns pretending to seek donations for Ukrainian refugees.
To keep you apprised of the increased cyber activity because of the Russia-Ukraine conflict, we’ll be updating this activity bulletin based on what we’ve analyzed and have observed across the intelligence community (IC):
As members of the REvil ransomware gang await sentencing for their role in 2021’s Colonial Pipeline attack, their lawyers have proposed collaboration between the cybercriminals and the Russian special services in the war against Ukraine. Russian outlets also report that the Russian Federal Penitentiary Service announced a strategy to hire IT professionals from Russian prisons to work remotely for commercial companies.
Russian hacker group Killnet has launched a cyberattack on Lithuania in direct response to their decision to block the transit of goods to Kaliningrad. The group claims it has cut off 70% of Lithuanian internet infrastructure from the rest of the web, primarily targeting state institutions, media websites and transport infrastructure. Killnet also claims to have crippled the websites of Lithuania's four airports.
Hackers from Anonymous took down websites for Russia's Federal Service for Supervision of Natural Resources, a federal government body responsible for ensuring rational and environmentally safe usage of natural resources; Nordavia, a Russian low-cost airline; and the Stavropol Regional Library for the blind and visually impaired.
Cyber attacks on Ukrainian entities have been traced to Russian state-backed hacking groups. 128 organizations in 42 countries outside Ukraine were also targeted by the same groups in espionage-focused hacks — the U.S. was the most-targeted country. The hacks were successful about 29% of the time, and some cases led to data being stolen.
Anonymous operatives DepaixPortuer and BOOdaMooda hacked a wide range of Russian websites, including the Federal Customs Service of Russia, a website belonging to a dental clinic in Saint Petersburg and a top Russian law firm. The hackers leaked 1 terabyte of data from the law firm to the DDoSecrets website, including attorney/client emails, court files and lists of clients.
Anonymous operatives hacked into a company that handles Russian military drones and stole classified documents with information about Russia's drone plans and tactics. These documents include the list of exporters and competitors of the country in terms of innovations in the unmanned vehicle industry, and military plans and documents collected from Russian military companies and government sources.
Russia warned the West that cyber attacks against its infrastructure will risk direct military confrontation, and attempts to challenge Moscow in the cyber sphere will be met with countermeasures. Russia's foreign ministry blamed the U.S. and Ukraine for cyberattacks on critical infrastructure and state institutions.
Senior U.S. cyber officials urged companies to remain on high alert for cyberattacks stemming from Russia’s war in Ukraine, saying the warnings are based on intelligence assessments of potential strikes. Russia is notorious for its malicious cyber activity, whether it's through a state-sponsored entity or through criminally aligned groups.
Phones used by Ukraine’s public servants came under sustained targeting from malware attacks, though there was no evidence of a successful breach. Top European Commission officials also had their phones targeted using "zero click" spyware that requires no interaction from the victim — a particularly feared form of attack. The deputy head of Ukraine's State Special Communications Service declined to comment on whether any such attempts against their own devices had occurred.
Anonymous operative Rootkit_sec gained control of the Russian software system used in running the Central Bank of the Russian Federation (CBR), which protects the stability of Russia's national currency, the ruble. In addition to compromising the system, the hacktivist also leaked the bank’s data. Anonymous has leaked more than 12 million files and emails of government agencies, business and other websites in Russia.
Anonymous took down Belarus’ Internal Affairs Ministry website just days after it blocked several Belarusian government websites because of the country's alleged support of Russia's invasion of Ukraine. Websites for the Ministry of Education, the Ministry of Communications, the Ministry of Justice, the National Legal Information Center, the State Customs Committee and the State Committee were taken down on May 29.
The Ukrainian IT army — now consisting of 270,000 volunteers from all over the world — attacked over 1,800 Russian online resources. Some of the army's most successful cases include the hacking of Rutube, the shutdown of the Russian national system for marking goods and the 1C service.
General Paul Nakasone confirmed that the U.S. conducted a series of operations in response to Russia's invasion of Ukraine. The "hunt forward" operations allowed the US to search out foreign hackers and identify their tools before they were used against America. The “hunt forward” activities — started out of concern for Russian retaliation against the US — were an effective way of protecting America and its allies, according to Nakasone. The activities were lawfully conducted with complete civilian oversight of the military and through policy decided at the DoD.
Ukraine’s IT army attacked over 800 Russian online platforms within a week, shutting down services at banks, stock exchanges, and insurance companies. The attacks made clients from a number of Russian banks unable to use online banking services or run financial transactions using a smartphone, forced Russian exchanges to cut off access to clients abroad in order to resume normal operations, shut down microloan services, disrupted online insurance services, and forced the RuStore online store to hide from DDoS-attacks behind a geoblock just one week after launching.
Ukraine stands to learn a lot about cyber defense from Estonia, whose cyber defense infrastructure ranks third-best in the world behind the United States and Saudi Arabia, according to the Global Cybersecurity Index (GCI). Estonia strengthened their defenses after Russia invaded them 15 years ago, setting up the Cyber Defense League to help the government face cyber threats. The Cyber Defense League is a unit of volunteers who donate their time by practicing what to do if a service provider is brought down by a cyber attack.
Russian hacking group Coldriver intercepted and leaked emails containing alternative Brexit plans to former British Prime Minister Theresa May’s ‘clean’ EU exit deal. Coldriver was linked to the leak through technical indicators.
Russian hacker group Killnet used distributed denial-of-service (DDoS) attacks to target thousands of Italian government and transportation infrastructure websites in an attempt to overload servers, causing delays and downtimes. In response, the Italian government launched the National Cybersecurity Strategy 2022-2026 to strengthen resilience, anticipate threats, manage crises and counter disinformation.
Russian President Vladimir Putin said that the number of cyber attacks on Russia has increased since the start of the war, and that Russia must strengthen defenses by reducing the use of foreign software and hardware and switching to domestic technology and equipment. Putin said Russia should make the switch because of sanctions on Russia restricting foreign IT, software and products and western suppliers stopping technical support of their equipment in Russia.
Anonymous Italia and allied hacktivist groups are preparing to launch their “final offensive” against Killnet in response to DDoS attacks against Italy — heavy damage to Russia is expected. The goal of the offensive is to sink the pro-Russia hacking group once and for all. The Italian group has already done some damage against Russia by temporarily blocking the Kremlin and Russian satellite communications agency websites.
Hacktivists launched a website that is designed to robocall and connect two Russian officials to confuse, distract, and annoy the officials as they try to figure out why they’re talking to each other. The site pulls random phone numbers from a leaked list containing Russian government, military and intelligence phone numbers. In case Russia tries to retaliate, the website is protected from DDoS attacks.
Hackers from pro-Russian cybercrime groups Killnet and Legion attempted to crash the live streaming of the Eurovision Song contest finale and disrupt the voting for the Ukrainian Orchestra that was in the competition. The DDoS attack targeting the network infrastructure was mitigated by Italy’s postal police, which fights cyberattacks.
A group of human rights lawyers and investigators from the Human Rights Center at UC Berkeley's School of Law requested that the International Criminal Court (ICC) in the Hague charge Russian hackers with war crimes for cyberattacks against Ukraine. The request pointed to Sandworm, a hacking group within Russia’s GRU military intelligence agency, and to two of their most egregious acts of cyberwarfare: Sandworm caused blackouts that targeted electric utilities in Ukraine in 2015 and in the capital a year later affecting hundreds of thousands of civilians. The charges against Sandworm would represent the first case of “cyber war crimes” ever brought by the ICC — the precedent established would help see justice for those harmed by Sandworm’s cyberattacks and also deter future cyberattacks affecting civilian infrastructure around the world.
Anonymous leaked 800,000 documents from Russian state-run nuclear energy facility Rosatom, mostly related to the nuclear company’s clients, affiliates, and contracts. This is the second time in less than three months that Anonymous has breached Rosatom.
As sanctions continue to hurt the Russian economy, the fear of a Russian cyberattack in retaliation rises. One risk is that Russia will strike Western governments in retaliation for cyberattacks against Russia from vigilante hackers — Russia may misinterpret these vigilantes’ support for Ukraine as being a product of backing from Western governments and attack accordingly.
Russian payment processor QIWI was hacked with 7 million bank cards stolen by NB65, a part of the Anonymous hacking collective. QIWI denied the reports of compromise, but NB65 published all of the card data on the web as proof of the hack.
The malicious cyberactivity against Ukraine includes Russian military cyber operators deploying multiple families of the wiper malware; Russian government cyber actors compromising Ukrainian civilian entities including emergency services, energy, transport and communication; and Russia launching cyber attacks against commercial satellite communications networks to disrupt Ukrainian command and control infrastructure. In addition to condemning these cyberattacks, Australia is imposing costs on state-based or state-sponsored malicious actors who undermine an open, free, safe and secure cyberspace.
A joint announcement from the US, EU, and UK confirmed that the primary target of an attack against American satellite internet company Viasat was the Ukrainian military, and the UK's National Cyber Security Centre (NCSC) said it was “almost certain” Russia was behind the attack. Viasat provides high-speed satellite broadband to commercial and military customers, and tens of thousands of their terminals were damaged beyond repair in the cyber attack, leaving several thousand Ukrainian users without internet. The attack spilled over to other countries too, knocking 5800 wind turbines in Germany offline.
Tens of terabytes of data from Russian companies and government bodies have been leaked as a part of a widespread campaign by low-level pro-Ukrainian hackers. The hackers leaked millions of emails spanning 20 years from the All-Russia State Television and Radio Broadcasting Company, and hundreds of millions of documents from targets such as the Russian government, Russia’s Ministry of Culture, Russian power suppliers, and the Russian Orthodox Church.
After an alleged member of Russian hacking group Killnet was taken into custody by police, leaders of the group threatened to shut down all British hospital ventilators if the member wasn’t released.
The U.S. sent cyber forces to Lithuania in the wake of growing online threats since Russia’s invasion of Ukraine. The teams scan networks, help countries build defenses, and share new information about threats with government and private industry circles in the U.S. Since 2018, these cyber teams have carried out 28 missions in 16 countries, on more than 50 networks.
Russia’s cyber offensive operations in Ukraine may have reached their full potential. Since the start of the invasion, at least six groups of Russian hackers have carried out about 240 attacks on Ukraine’s digital resources, but due to recent sanctions, Russian hackers have lower capabilities and won’t be able to develop as they did before. However, Russian hackers are still a dangerous force, and are applying strong pressure in cyberspace to Ukraine.
Ukraine’s volunteer “IT Army” of hackers has been knocking Russian websites offline using DDoS attacks, including Russian online payment services, government departments, aviation companies and food delivery services, all targets that disrupt everyday life in Russia. The increased hacking activity comes from hacktivists, Ukrainian forces and outsiders from all around the world that have aided in targeting Russia and its businesses. Both Russia and Ukraine have used DDoS to disrupt each other but attacks against Russia have been more innovative and prolonged — the longest-lasting attack was more than 177 hours.
Since just before the invasion, six separate Russia-aligned nation-state actors have launched more than 237 operations against Ukraine. The cyber-warfare operations include ongoing destructive attacks that threaten civilian welfare and disrupt Ukrainian government and military functions. Microsoft tracked almost 40 cyberattacks that were aimed at hundreds of systems — a third of the attacks targeted Ukrainian government organizations at all levels, while 40% of the attacks went after critical infrastructure. Russia started preparing for cyberattacks in March 2021, almost a year before Putin ordered troops to invade Ukraine.
Anonymous hacked the website of the Federal Bailiffs Service of Russia (FSSP), a Russian federal agency that serves as the judiciary’s enforcement arm and is responsible for the safety of court officers and providing security within court buildings.
A network of railway workers, hackers and security forces disabled railway links connecting Russia to Ukraine through Belarus, wreaking havoc on Russian supply lines. In the first attack, The Cyber Partisans, a group formed of exiled Belarusian IT professionals, hacked into the railway’s computer network in the days leading up to the invasion, slowing rail traffic before Russian troops had even crossed the border. Infiltrating the railway network’s computers was easy because the railway company was still using Windows XP, an outdated version of Windows known to contain many vulnerabilities.
Elon Musk’s Spacex Starlink satellite network rapidly fought off an attempt by Russian attackers to jam the network in Ukraine — SpaceX engineers thwarted the attempt by patching code just one day after initial reports of the attack.
The “Five Eyes” intelligence sharing network, consisting of the US, Britain, Canada, Australia, and New Zealand, have warned that Russia is contemplating cyber attacks on countries backing Ukraine, and could also work with cybercrime groups to launch attacks on governments, institutions, and businesses — some cybercrime groups have recently publicly pledged support for the Russian government.
NATO’s annual cyber wargames, known as the Locked Shields exercise, simulate fictional cyberattacks that cyber experts have to defend against under time pressure. The exercise is significant for the participating countries because their cyber defense units have been on high alert since the outbreak of the war. This gives them the chance to communicate with each other about attacks on the same technologies that several governments use.
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a social engineering campaign designed to leverage Zimbra exploits and deliver the IcedID malware. Attributed to threat cluster UAC-0041, the attacks begin with an email containing a Microsoft Excel document that, when downloaded, prompts users to enable macros, leading to the deployment of IcedID. The second set of intrusions belongs to a new threat cluster termed UAC-0097, and begins with an email including image attachments with a content-location header pointing to a remote server hosting a piece of JavaScript code. Downloading the image attachment activates an exploit for a Zimbra XSS vulnerability (CVE-2018-6882), then the injected JavaScript is used to forward victims’ emails to an email address under the threat actor’s control.
Ukraine’s energy sector was targeted by Russian military hacker group Sandworm in an attempt to shut down their infrastructure by infiltrating computers connected to multiple substations and deleting all their files. Though the malware successfully infiltrated some computers in Ukraine’s energy sector and even caused disruptions at one facility, the threat was resolved quickly with the help of IT staffers, Ukrainian intelligence officers, Microsoft, and Slovakia-based cybersecurity company ESET. The collaborative effort resulted in the discovery of Industroyer2, a new variant of the Industroyer malware. Thankfully, no customers lost power.
Anonymous targeted Russian firms Aerogas, an engineering firm catering to Russia’s oil and gas sector; Petrovsky Fort, which owns the largest office complexes in Saint Petersburg; and Forest, a Russia-based logging firm. The attacks resulted in over 400 GB worth of leaked emails.
Russia’s own ransomware was used by an Anonymous-linked hacker group, Network Battalion 65 (NB65), to successfully attack Russian space agency, Roscosmos. NB65 claims the stolen files show that Russian President Vladimir Putin no longer has control over spy satellites. One of the stolen files’ source code was made up of 66% of the same code as Conti, a piece of Russian ransomware used to extort millions of dollars from the US and Europe’s hospital and health services. NB65 located Conti’s source code on VirusTotal, then used a modified version to break into the space agency.
Australian Signals Directorate boss, Rachel Nobel, warns that Russia could still launch a major cyber attack against the Ukraine. Nobel believes that Russia has held back out of fear of what western countries would do in return.
A new wave of cyber attacks are targeting Telegram Messenger accounts. Digital marauders are using a phishing domain to send messages with malicious links to the Telegram website to gain unauthorized access to records. The attacks (threat cluster UAC-0094) originate with Telegram messages alerting recipients that logins had been detected from a new device located in Russia and urges users to confirm their accounts by clicking on a link. The link prompts the victim to enter their phone number as well as the one-time passwords that are then used by the threat actors to compromise the accounts.
The U.S. secretly removed malware worldwide to pre-empt Russian cyberattacks, according to a report by The New York Times. The U.S. Justice Department and FBI were given secret court orders and assistance from worldwide governments and disconnected networks from the G.R.U.’s own controllers. The FBI was able to go into domestic corporate networks and remove the malware, sometimes without the company’s knowledge. The malware would have enabled Russians to create botnets controlled by the G.R.U., though its intent was unclear.
China is being accused of hacking Ukraine days before the Russian invasion – the attacks are allegedly on Ukraine’s military and nuclear facilities. More than 600 websites belonging to the defense ministry in Kyiv and other institutions suffered thousands of hacking attempts.
The attacks may have started before the end of the Winter Olympics and peaked the day before Russian troops and tanks crossed the border. The attacks – which could be distinguished by the trademark tools and methods of the People’s Liberation Army – were allegedly designed to steal data and explore ways to shut down or disrupt vital defense and civilian infrastructure.
The North Atlantic Treaty Organization (NATO) and other European militaries were targeted by Russian hacking group Coldriver via credential phishing campaigns. The campaigns utilized newly created Gmail accounts as well as other email accounts outside of GSuite.
U.S. analysts believe that hackers backed by Russia’s military intelligence agency crippled tens of thousands of Viasat satellite modems in Ukraine. Intruders took advantage of a misconfigured VPN device to gain remote access to the management network for the company’s KA-SAT satellite. From inside the network, hackers sent rogue commands to tens of thousands of modems all at once to overwrite key chunks of data in the device memory – making them inoperable. The attack affected users from Poland to France and knocked off remote access to thousands of wind turbines in central Europe
A powerful cyberattack on Russian Federal Air Transport Agency, Rosaviatsia, erased 65 terabytes of data along with all documents, files, aircraft registration data and server emails. No backup of data exists due to lack of funds from Russia’s Ministry of Finance. Hacktivist collective Anonymous is presumed to have carried out the attack, but the group has denied the allegation.
Ukrtelecome, one of Ukraine’s largest Internet providers and biggest fixed line telecommunications company, was hit with powerful cyberattack. Described as the most severe cyber attack since the start of Russia’s invasion, the attack caused outages across the country. Once the attack was neutralized, Ukrtelecom was forced to limit services to the majority of private users and business clients in order to preserve network infrastructure and to continue to provide services to the Armed Forces and other military formations.
Ukraine’s Computer Emergency Response Team (CERT) has observed a spear-phishing campaign that uses a new malware called DoubleZero. ZIP archives that were discovered are labeled “Virus…extremely dangerous!!!. Zip.” DoubleZero is a malicious destructor program developed using the C# programming language.
The malware primarily leverages two techniques. In the first it overwrites content with zero blocks of 4096 bytes (using FileStream.Write) or using API-calls NtFileOpen, NtFsControlFile (code: FSCTL_SET_ZERO_DATA). The technique involves deleting Windows registries – HKCU, HKU, HKLM \ BCD – before shutting down the infected system.
Anonymous was back in the spotlight after it claimed to have hacked the Central Bank of Russian Federation. The group also leaked documents tied to the hack.

Victor Zhora, deputy chief of Ukraine’s information protection service, said Russian hackers are attacking logistical lines in Ukraine, including those delivering food and humanitarian support. He went on to indicate the attacks have mostly been unsuccessful or caused minor disruptions.

President Biden of the United States addressed the nation and indicated that companies should harden their cyber defenses. The President mentioned "evolving intelligence" to suggest Russia could conduct malicious cyber activity against American companies and critical infrastructure.
Russia is a dominate threat actor in the cyber space and as the war continues, companies should be prepared for increased and possible targeted attacks. In an effort to provide guidance, the Cybersecurity and Infrastructure Security Agency (CISA) created Shields Up, a resource center that provides insights and recommendations for organizations.
The website of the Ministry of Emergency Situations of Russia was hacked. The culprits posted a message about the Russian army's death toll in Ukraine. Hyperlinked messages were also included, such as: "Don't trust the Russian media — they lie to you,” as well as, "Full information about the war in Ukraine" and "Russia's default is imminent."

A compromised Ukranian TV station transmitted a phony surrender announcement from Ukrainian President Volodymyr Zelenskyy. The message urged Ukrainians to stop fighting and surrender their weapons, while claiming that Zelenskyy “wanted to take Donbas” but was unsuccessful,” but was unsuccessful, so he fled Kyiv. Zelenskyy responded via YouTube confirming that it was a false announcement and declared that Ukraine would not give up its arms until it had achieved victory.
A new website built by Polish hacktivist group, Squad303, allows anyone to text random Russians about the war in Ukraine. The tool is meant to cut through President Putin’s media censorship and restricted social media access to reach average citizens. The site generates random Whatsapp numbers that can be used to send out messages. The program leverages a bank of nearly 20 million cell phone numbers that were obtained by compromising a Russian database. So far, nearly 30 million messages have been sent.
New wiper malware dubbed “Caddy” is making the rounds in the Ukraine. The malware erases user data and partition information from any drives that were connected to an affected machine. Files are corrupted and overwritten with null byte characters, losing the user data forever in the process. This is a destructive approach and has nothing to do with extracting money. Caddy is the third wiper to hit Ukrainian systems since the start of the war.
Digital marauders are taking advantage of the news, activity, and overall attention the Russian invasion of Ukraine is getting to do their dirty deeds. Online hackers have been more active since the start of he war and have been using it as a distraction to ramp up activities and steal more money the longer the conflict continues. The financial services industry is expected to be a major target following the recent sanctions implemented against Russia.
Following Canadian Prime Minister Justin Trudeau’s involvement in sanctioning Russia, the country is now expected to be at higher risk for cyberattacks emanating from Russia. Based off of Russia’s history of housing some of the world’s most notorious cyber hacking groups – including Sandworm – Canadian cybersecurity professionals are anticipating inevitable cyberattacks, driven by Russia’s need for money to combat the sanctions. Larger companies may be prepared, but smaller organizations should be wary given nearly half of Canadian small businesses suffered a cyber attack in 2021 due to having no budget allocation for cybersecurity.
A hacker accused of helping Russian military send instructions to troops has been detained in Ukraine. The suspect was accused of being on thousands of calls to Russian officials and accused of sending text messages to Ukrainian officials suggesting that they surrender. The suspect’s seized equipment was used to route Ukrainian mobile phone traffic to Russian networks.
Anonymous took to Twitter to share the names of the Russian websites it attacked and brought down, providing screenshots as proof. Sites include Moscow.ru, Russia’s Federal Security Service (principal security agency of Russia and the main successor agency to the Soviet Union’s KGB), and the Analytical Center for the Government of the Russian Federation, a Russian think tank for socio-economic development issues of the country), and the Ministry of Sport of the Russian Federation. The group also tweeted a leaked correspondence between Putin and Russia’s Defence Minister that outlines plans to cut down and sell Ukrainian forests.The group also brought down Rosatom, a Russian firm that seized the Ukrainian nuclear power plant, Zaporizhzhya. The group changed the interface on the site to make it inaccessible. They also claimed to have gained access to gigs of data which they plan to leak to the public.
Over 300,000 individuals – many from other countries – signed up to a Telegram group called the IT Army of Ukraine with the intent to disrupt Russian web services. Availability of the Kremlin and Duma (Russia’s lower house of parliament) websites have been intermittent since the invasion started. Media services, banks and the energy giant, Gazprom, have also been targeted.
An Anonymous offshoot dubbed GhostSec was able to take control of Russian printers and print information about war in Ukraine on them. The group seized over 100 Russian government and military printers to print the following message:
This is not your war. This is your government’s war. We lie to your brothers and sisters. Soldiers from some military units think they are in formation. But when they achieve their goal, which is to be a drill, they are met by bloodthirsty Ukrainians who want revenge for the destruction of their land that Putin’s puppets have inflicted on them. Some of them think they will go down in history, making the world a better place when they take part in the invasion of Ukraine. Brethren, open your eyes. Glory to Ukraine! God bless Ukrainians and Russians. Let the Russian government live what Ukrainians have to live every day.
A threat actor – NB65 – who has indicated they side with the Ukraine, has purportedly leaked Kaspersky source code. According to some Twitter posts, this may have just been a stunt to keep Kaspersky IR busy.

Multiple sources reported hackers had taken over Bulgarian media to broadcast a meme that Russian President Vladimir Putin dislikes.
Elon Musk says Starlink is the only non-Russian communications system in parts of Ukraine, making it an attractive target for Russian hackers. SpaceX is focusing on bolstering its cyber defense after its Starlink signals get jammed.
Ukraine’s Minister for Digital Transformations, Mykhailo Fedorov, is calling for the assistance from anyone who has “digital abilities.” Federov is part of the IT Military of Ukraine, a group of ragtag hackers that work within and outside of the country to coordinate distributed denial of service attacks (DDoS). Their work has knocked several Russian authority websites offline. The purpose of these attacks is to create a distraction for Russia, forcing the country to address the problems quickly and divert their military efforts.
CyberKnown reports that Lulzsec is claiming to be back in action. This will be something to closely monitor in the day and weeks ahead.

The Guardian reports that Visa and Mastercard have announced they will be suspending operations in Russia following its invasion of Ukraine.
According to darkfeed.io, a ransomware gang is indicating that the war is disrupting their operation.

Anonymous announced that they had leaked network infrastructure information for Russian industrial control systems. This follows the leak of Russian military data in February.

An ESET researcher discovered a new data wiper malware – dubbed IsaacWiper – that was used against a Ukrainian governmental network. ESET telemetry shows that it was installed on hundreds of machines in the country. This follows a DDoS attack against several Ukrainian websites.

[The dialogue we’re observing among threat actors during this conflict is unprecedented. Threat actors have either publicly taken a side or remained neutral during this conflict. We believe the groups staying neutral are doing to not only keep paying affiliates, but also to keep peace among international group members. We also believe that if the conflict continues to intensify, we could have a possible disruption in threat activity as many use Russian infrastructure and many threat actors are Russian in origin.]
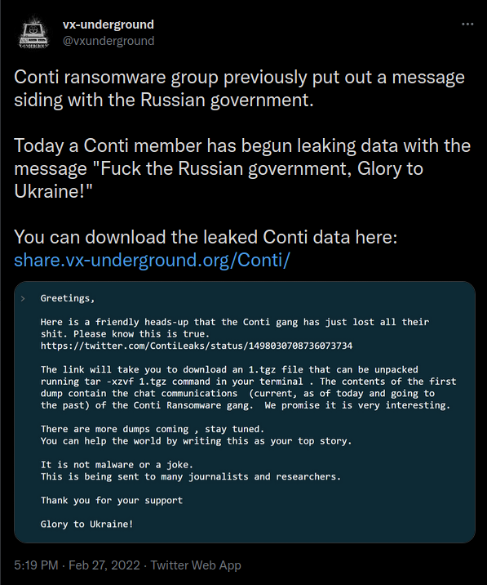
VX-Underground, a leading source of intelligence and threat actor drama, recently brought to attention to the IC that ransomware gang Conti had sided with Russia. And at the same time Anonymous was declaring a digital war with Russia.


On Twitter, Anonymous shared that they had taken down a Russian government site. Later that day, VX-Unground tweeted that a Conti member had begun leaking internal documents with a message “F’ the Russian government, Glory to Ukraine!” The member stated the data was being sent to a few journalists and researchers, however, it has now been made public.

Around the same time on a Dark Web forum, LockBit criticized Conti about their lack of operational security while reviewing the leaked documents. LockBit went on to say they will buy Emotet/Trickbot sources (a reference to Conti joining up with Trickbot in the past).
LockBit made a post on their leak site stating that they aren’t taking sides, possibly another jab at Conti. However, LockBit isn’t alone. Other ransomware gangs are also stating they won’t take sides, stating their “employees” and affiliates are all over the world.


After officially declaring digital war on the 24th, Anonymous posted tweets on the 26th that stated they hacked Russian State TV and were airing the real news about what was happening in Ukraine. Also that day they claimed to have intercepted Russian military communications.

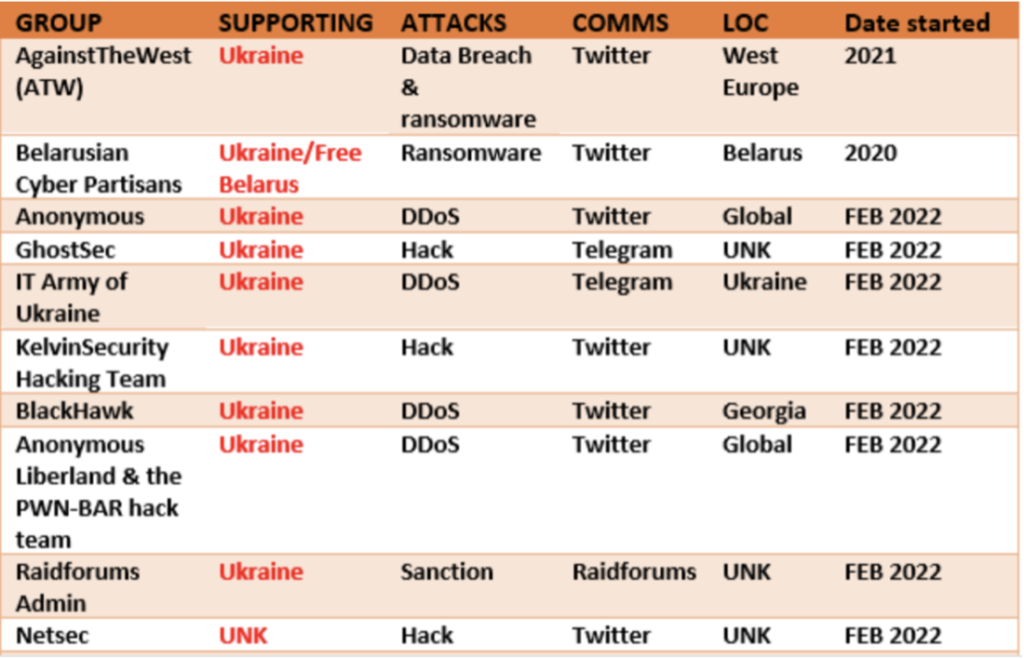
The SANS Institute provided numerous resources for companies to scan their infrastructure and build up defenses against known TTPs and malware emanating from Russia. Additionally, Cyber Know put out a list of known groups involved in cyber activity related to the conflict.
According to CrowdStrike, a new malware family dubbed WhisperGate was reportedly deployed against Ukrainian targets. The incident is widely reported to contain three individual components deployed by the same adversary, including a malicious bootloader that corrupts detected local disks, a Discord-based downloader, and a file wiper. Following infection, the threat actor leaves a fake ransom note. The activity was said to have occurred at approximately the same time multiple Ukrainian government websites were defaced.

Sentinel Labs reported that the threat intelligence community began observing a new wiper malware sample circulating in Ukrainian organizations. The malware shows a signed driver by Hermetic Digital Ltd (now revoked) that is being used to deploy a wiper that erases Windows devices, after deleting shadow copies and manipulating MBR after rebooting. The wiper has been dubbed, HermeticWiper.
The United Kingdom’s National Cyber Security Centre (NCSC), the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) have identified that the actor known as Sandworm or Voodoo Bear is using a new malware, referred to here as Cyclops Blink. The NCSC, CISA, and the FBI have previously attributed the Sandworm actor to the Russian General Staff Main Intelligence Directorate’s Russian (GRU’s) Main Centre for Special Technologies (GTsST).
Menlo Labs is closely monitoring the conflict and for new intelligence. While these attacks have mostly been confined within the Ukraine and Russia, it’s possible that similar attacks, in addition to the malware used, could be leveraged against other targets.