world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

Menlo Security has been closely monitoring an attack we are naming “Duri.” Duri leverages HTML smuggling to deliver malicious files to users’ endpoints by evading network security solutions such as sandboxes and legacy proxies. Isolation prevents this attack from infecting the endpoint. Here’s what we know.
The goal of HTML smuggling is to make use of HTML5/JavaScript features to deliver file downloads, and it usually comes in two flavors:
In this specific attack, we observed the JavaScript blob technique being used to smuggle malicious files via the browser to the user’s endpoint. Constructing content on the client browser like this evades network security solutions such as sandboxes and proxies.
According to our observations, the Duri campaign started in the beginning of July and is currently active. Earlier this month, we identified a user’s visit to a website and subsequent file download, which was blocked because it was suspicious. Upon investigation, we discovered that the file was downloaded through HTML smuggling.Traditional network security solutions such as proxies, firewalls, and sandboxes rely on the transfer of objects over the wire. For example, a sandbox might extract file objects such as .exe, .zip, and other suspicious objects from the wire and then send them to the sandbox for detonation. With Duri, the entire payload is constructed on the client side (browser), so no objects are transferred over the wire for the sandbox to inspect.
The malware that Duri downloads is not new. According to Cisco, it has previously been delivered via Dropbox, but the attackers have now displaced Dropbox with other cloud hosting providers and have blended in the HTML smuggling technique to infect endpoints. We speculate that this change in tactic is being used to increase the success rate of compromised endpoints.
Once the user clicks on the link, there are multiple levels of redirection before the user lands on an HTML page hosted on duckdns[.]org. The landing page invokes a JavaScript onload that initializes data for a blob object from a base64 encoded variable as shown below.

As seen above, a ZIP file is dynamically constructed from the blob object with MIME type as octet/stream and is downloaded to the endpoint. The user still needs to open the ZIP file and execute it.
The ZIP archive contains an MSI file [T1218.007]. The .msi file extension indicates that the file is a Microsoft Windows installer and contains the application and all of its dependencies.unzip PUVG OKZAGE SBKZXONA ETRWDDQGBL .zipArchive: PUVG OKZAGE SBKZXONA ETRWDDQGBL .zip inflating: PUVG OKZAGE SBKZXONA ETRWDDQGBL (869261) .msi file PUVG OKZAGE SBKZXONA ETRWDDQGBL (869261) .msiPUVG OKZAGE SBKZXONA ETRWDDQGBL (869261) .msi: Composite Document File V2 Document, Little Endian, Os: Windows.Examining the MSI file shows that there is an execute script code action defined in the custom action of the MSI contents:
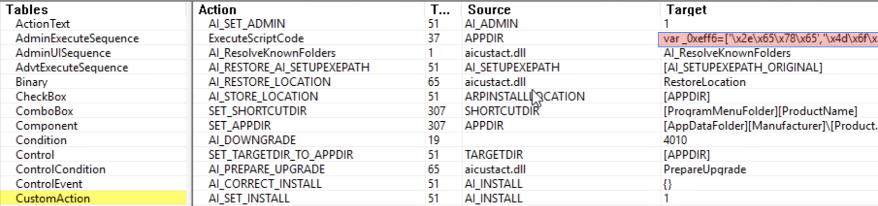

The embedded JSCRIPT is obfuscated, and it performs the following actions upon invoke:
The extension in the URL is .jpg, but it is a ZIP file.
While traditional security solutions rely on a detect-and-respond approach to cybersecurity, Menlo enables a Zero Trust approach by forcing a block-or-isolate decision at the point of click. All content is fetched and executed in a remote browser and is cut off from the endpoint, while only safe mirrored content reaches the user’s device. This prevents malware from accessing the endpoint.Campaigns like Duri, in which JavaScript is used to programmatically and dynamically generate the malicious payload, cannot evade the Menlo platform. Downloading files via Menlo is a two-step process. Every file download in the isolated browser triggers a unique event on our platform—whether it's because of a DataURL, a JavaScript blob download, or a link. As a result, the Menlo platform enables enhanced visibility into the contents of every file.Attackers are constantly tweaking their tactics in an effort to evade and bypass security solutions—forcing tools that rely on a detect-and-respond approach to always play catch-up. We believe HTML smuggling is one such technique that will be incorporated into the attackers’ arsenal and used more often to deliver the payload to the endpoint without network solutions blocking it. Menlo’s isolation approach prevents all content from reaching the endpoint—effectively blocking all malware without impacting the native user experience. It’s security without compromise.
References:
IOC—URLs
hxxp://huzirh.com/hidrol/
hxxp://isocamprh.com.br/
hxxp://hxxp.plasticospr.com/webmailgrupo?nzn11t6c68b5k40ry31c903ez3xaq/formulario_correios_37.pdf
hxxp://gmpbusdoor.com/
hxxp://hxxp.isocamprh.com.br/incolajes
hxxp://iboxrh.com/consultoriarh?1e0wq712tctv0232v000lnjsn4c7a/boleto.3673.pdf
hxxp://www.isocamprh.com.br/incolajes
hxxp://hxxp.isocamprh.com.br/incolajes/
hxxp://isocamprh.com.br/incolajes?page=boletos&idBoleto=8868
hxxp://hxxp.westermarh.com/waycompany?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://hxxp.grentrepostorh.com/
hxxp://update-completo.com/
hxxp://plasticospr.com/webmailgrupo?fotoswhatsapps/Imagem.htmldigitaloceanspaces.com/Fotos.html
hxxp://ultrafarmarh.com/transglobal?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://hidrolrh.com/
hxxp://hxxp.casadaembalagemriopreto.com/officeclean?NZN11T6C68B5K40RY31C903EZ3XAQ/Formulario_Correios_37.pdf
hxxp://www.fjpconstrucoes.com/predilecta
hxxp://grentrepostorh.com/webmailgrupo?page=boletos&idBoleto=8868
hxxp://casadaembalagemriopreto.com/officeclean?PU106006743Z5QP2SL6RC00CT2330/Boletim_Registrado38361526.pdf
hxxp://grjseguros.com/
hxxp://hxxp.huzirh.com/hidrol?page=boletos&idBoleto=8868
hxxp://usinasalgado.com/contabilidadecnt
hxxp://westermarh.com/
hxxp://www.fjpconstrucoes.com/predilecta
hxxp://fjpconstrucoes.com/
hxxp://www.graphiczonerh.com/mobile?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://www.westermarh.com/waycompany?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://www.iboxrh.com/
hxxp://westermarh.com/waycompany?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://hxxp.grjseguros.com/
hxxp://grentrepostorh.com/
hxxp://hxxp.continentalnetrh.com/tbvc?get-facebook-verified/get-facebook-verified.html
hxxp://hxxp.westermarh.com/waycompany
hxxp://hxxp.fachiniengenharia.com/predilecta
hxxp://gmpbusdoor.com/furnax
hxxp://hxxp.plasticospr.com/webmailgrupo?NZN11T6C68B5K40RY31C903EZ3XAQ/Formulario_Correios_37.pdf
hxxp://hxxp.update-completo.com/consultrh?page=boletos
hxxp://www.grentrepostorh.com/webmailgrupo
hxxp://www.fjpconstrucoes.com/
hxxp://hxxp.fachiniengenharia.com/predilecta?NZN11T6C68B5K40RY31C903EZ3XAQ/Formulario_Correios_37.pdf
hxxp://fjpconstrucoes.com/predilecta
hxxp://www.versatilsegurosrh.com/vbimport?woa/rest/Faturamento/v1/faturadigital/visualizar?data-vencimento
hxxp://fjpconstrucoes.com/predilecta
hxxp://www.laboratrh.com/contabilidadecnt?page=boletos&idBoleto=8868
hxxp://fachiniengenharia.com/predilecta
hxxp://hxxp.hidrolrh.com/heimatschutz
hxxp://fjpconstrucoes.com/predilecta?page=boletos&idBoleto=8868
hxxps://iboxrh.com/
hxxp://fachiniengenharia.com/predilecta?page=boletos&idBoleto=8868
hxxp://grjseguros.com/grjseguros?PU106006743Z5QP2SL6RC00CT2330/Boletim_Registrado38361526.pdf
hxxp://continentalnetrh.com/tbvc?get-facebook-verified/get-facebook-verified.html
hxxp://grentrepostorh.com/webmailgrupo
hxxp://isocamprh.com.br/incolajes?page=boletos&
hxxp://hxxp.westermarh.com/
hxxp://fachiniengenharia.com/predilecta?page=boletos&idBoleto=8868
hxxp://hidrolrh.com/heimatschutz
hxxp://bustvch.com/
hxxp://hxxp.grentrepostorh.com/webmailgrupo?PU106006743Z5QP2SL6RC00CT2330/Boletim_Registrado38361526.pdf
hxxp://isocamprh.com.br/incolajes?page=boletos&idBoleto=8868
hxxp://fjpconstrucoes.com/predilecta?page=boletos&idBoleto=8868
hxxp://casadaembalagemriopreto.com/
hxxp://hxxp.bustvch.com/
hxxp://iboxrh.com/
hxxp://hxxp.fjpconstrucoes.com/predilecta?PU106006743Z5QP2SL6RC00CT2330/Boletim_Registrado38361526.pdf
hxxp://www.continentalnetrh.com/tbvc?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://bustvch.com/adinoxrs
hxxp://hxxp.ultrafarmarh.com/transglobal?WhatsApp_Historico_de_Conversas?whatsapphistorico/index.html?visualizar=c06e8cf10aeaf00c33360d2b2bfb6792
hxxp://hxxp.update-completo.com/consultrh?page=boletos&idBoleto=8868
hxxp://hxxp.casadaembalagemriopreto.com/