world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers

The Emotet malware is a very destructive banking Trojan that was first identified in 2014. Over the years it has evolved with new capabilities and functionalities, prompting cybersecurity agencies like the Australian Cyber Security Centre and US-CERT to issue advisories. Emotet malware generally spreads via malicious documents that drop a modular Trojan bot, which is used to download and install additional remote access tools. We wrote a blog post in January 2019 about how the malware had changed tactics, leading to a spike in the number of Emotet malware attacks. In the last week, we have observed a spike in the number of Emotet malware transactions across our customer base. US-CERT has also issued a fresh advisory regarding the recent spate of attacks.
Our research has discovered that the Emotet malware is still very active and continues to be one of the most destructive malware attacks. The malware has evolved through the years, and the actors behind Emotet have used the infected endpoints to build out a formidable botnet that is used to distribute multiple malware families such as Trickbot and Dridex, as well as ransomware such as Ryuk.
After taking a break through the holiday season in 2019, Emotet malware attacks have restarted in 2020, this time targeting the financial services industry. Similar to previous versions, the Emotet malware is only just the initial attack vector used to launch the attack. The attack is initiated with a malicious Microsoft Word document that is designed to be downloaded and opened by the user. Once opened, the malicious macro executes and contact is made with the command-and-control server to initiate the next stage of the attack.
Menlo Security Research analyzed the topics listed below to gain a better understanding of this most recent Emotet malware attack. Data for this analysis was obtained from the Menlo Security Cloud Platform, which supports millions of users across all industries, including financial services, educational institutions, and the military. In addition to analyzing the Emotet document macro and loader, the analysis breaks down the following for this most recent Emotet malware attack spike and shows the distribution of the industries affected.
Recent news shows that Emotet infections have crippled daily operations in a number of organizations. Emotet usually propagates in bursts, through delivery of malicious documents via mass compromised websites. Each infected host is then used to build out a botnet. The Menlo Security Research team noticed a spike in Emotet malware activity in January 2020. This spike was detected through our cloud isolation platform, which renders email attachments and websites visited from emailed links remotely, eliminating the possibility that malicious documents would reach an end user’s computer.The spike in activity occurred during January 14–22, affecting customers using our isolation service in the United States, Europe, and Asia. The following chart shows a spike in the number of Emotet document requests from January 14–22, 2020.
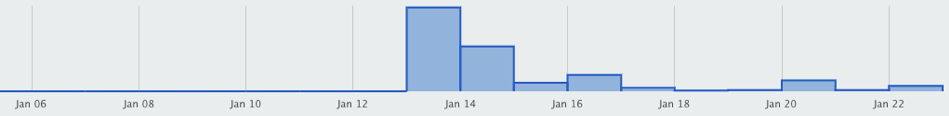
The chart above shows a Spike in Emotet Malware Detected
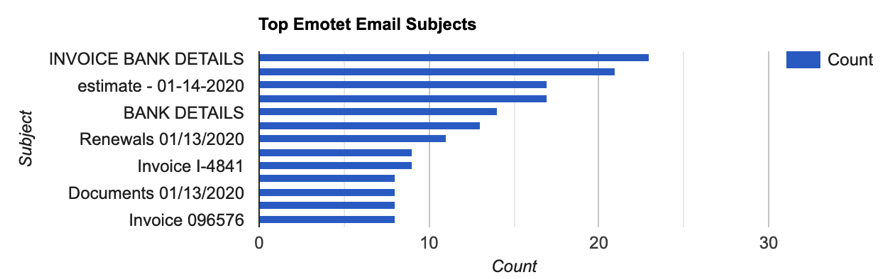
Like other Emotet malware versions, this recent attack also used malicious macros in a Microsoft Word document. The emails were crafted to appear as legitimate banking or financial transactions. Some examples of the subject lines used in this most recent campaign are given below.

The January 2020 campaign appeared to follow the kill chain similar to the attacks observed in late 2019. The initial attack is used only to gain a foothold in the network and establish contact with the command-and-control server. Once in place, additional malware is downloaded and the malware attempts to spread to other computers on the same network.

From the above flow, we can divide the Emotet kill chain as follows:
Our data shows that the January 2020 campaign targeted financial services companies primarily in the United States. The following charts show the industry/vertical distribution and regions where these requests came from. Other industries and geographies were included in the attack, though to a far lesser degree.

One of the techniques that Emotet malware uses is to distribute itself through other compromised legitimate websites, essentially creating new zero-day attacks. This makes the malware particularly difficult to protect against since the source of the malware is constantly changing. The following chart categorizes the distribution of the initial delivery URLs that served the malicious documents. The data shows very clearly why Emotet malware continues to evade security defenses and wreak havoc: 76 percent of the URLs used to distribute Emotet malware are actually categorized as safe by the leading threat intelligence databases. Some of the compromised websites were from academic institutions. This means that security products would not block or prohibit users from accessing and downloading content from these sites. Fortunately, Menlo Security customers were fully protected, because these malicious sites would have been viewed in isolation—completely protecting the end user.

Once the embedded macro inside the document is enabled, it spawns PowerShell to try a list of URLs to fetch the initial Emotet loader. Some observations of the macro behavior:

Further analysis shows that the January 2020 Emotet malware was a far-reaching campaign that was executed through multiple networks. A concentration of IP addresses occurred in certain countries with global financial centers.

The final Emotet bot that gets dropped is usually a modular Trojan that establishes a command-and-control channel by choosing an IP from a list of IP addresses in its config file. The Emotet loader is very well researched and documented, so we will not get into the inner workings of this bot here. Some of the variations we observed:

The Emotet malware has built a formidable infrastructure over time and can be destructive to an organization if not mitigated in a timely manner. Its techniques of leveraging multistage attacks and distributing malicious code through legitimate websites make the Emotet malware particularly hard to prevent with traditional security products that rely on signatures or threat intelligence.To protect against Emotet malware attacks, enterprises should:
For threat response teams: Keep a close watch on the techniques used by the Emotet actors; https://attack.mitre.org/software/S0367/ has a specific ATT&CK framework page for Emotet.Email and web isolation can provide complete protection from Emotet malware by inserting a secure, logically air-gapped execution environment in the cloud between the user and the malware. By executing sessions away from the endpoint and delivering only safely rendered information to devices, users are protected from malware and malicious activity. The result is that Emotet malware cannot infect a device it cannot reach. Isolation eliminates the possibility of malware reaching user devices via compromised or malicious websites, email, or documents. This approach is not detection or classification; rather, the user’s web session and all active content (JavaScript, Flash, etc.)—whether it’s good or bad—is fully executed and contained in a remote web browser in the cloud. Menlo Security has helped hundreds of Global 2000 companies and major government agencies use isolation to protect against Emotet and other malware, as well as phishing attacks, drive-by exploits, and other web- and email-based attacks.
Contact Menlo Security today to learn more about the Menlo Security Secure Internet with an Isolation Core™.