world tour:
Join us for a live look at how Menlo’s Secure Enterprise Browser puts you ahead of attackers
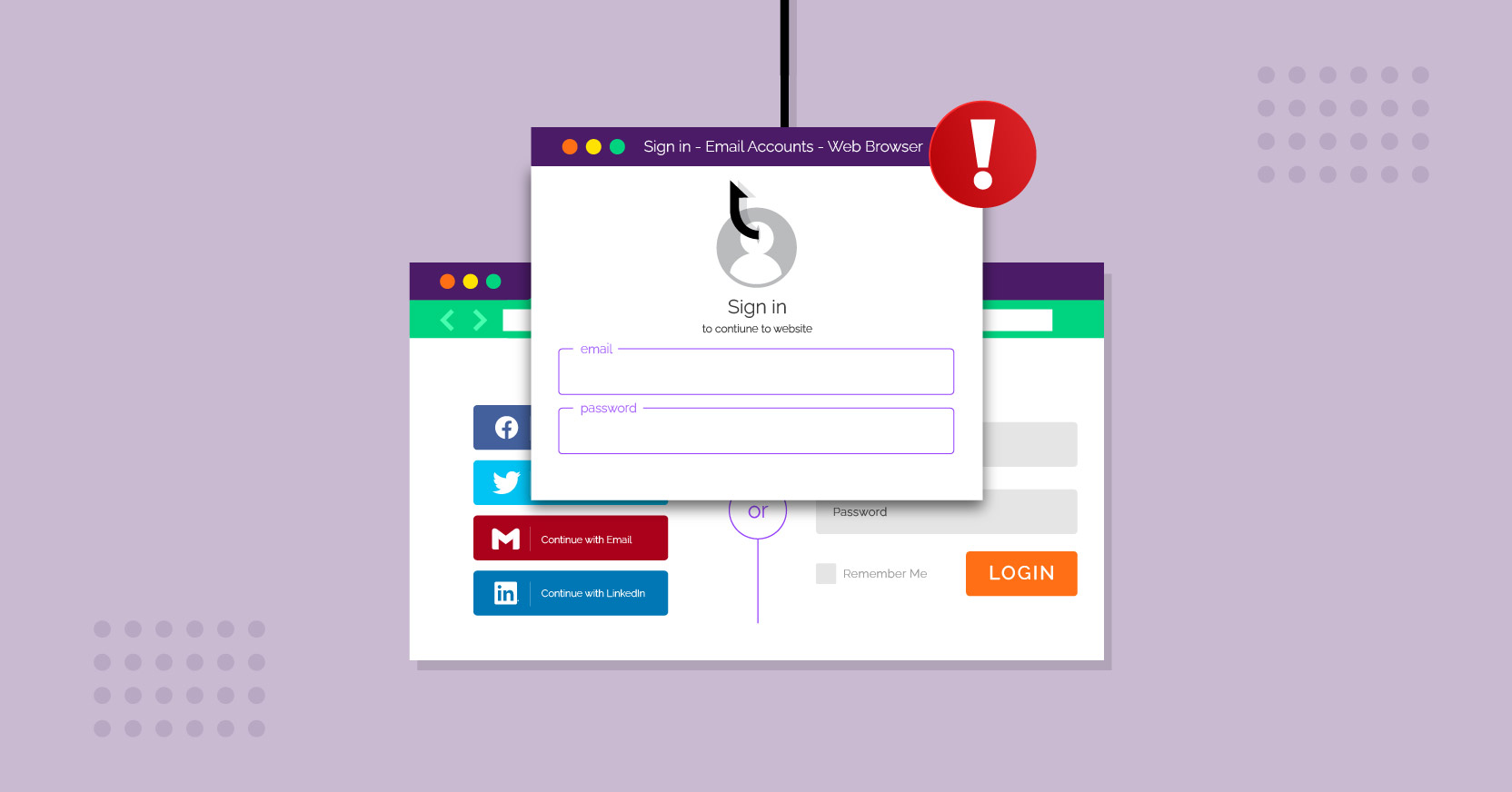
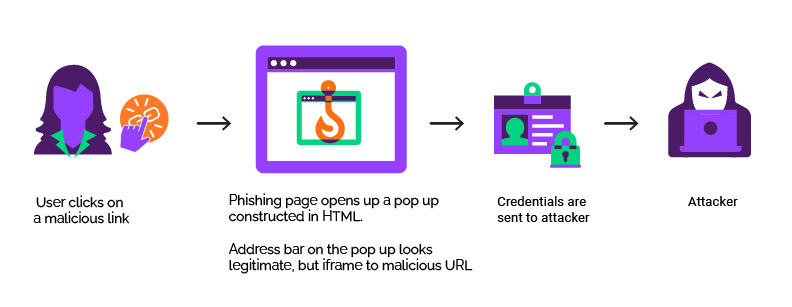
The Menlo Labs research team recently analyzed a malicious domain that is known for using Browser in the Browser (BitB) attacks. A BitB attack starts when a user goes to a site and is asked to sign in via a third party (such as Google or Facebook). When the user clicks the link, another popup that is completely constructed using HTML and CSS appears. While the URL displayed in the popup looks like a legitimate site, the underlying iframe points to a phishing site. These attacks leverage Highly Evasive Adaptive Threat (HEAT) techniques to evade detection.
When we analyzed the domain gateway[.]pinata[.]cloud, we noticed that it was associated with multiple phishing sites. Not only were the sites different, but the referring links were, too. From a generic email login page to a fake CDC landing page, this domain hosted a treasure trove of phishing sites. We would now like to share some of them with you.
The first URL path we will look at is: gateway.pinata[.]cloud/ipfs/QmUaW8pYp41riYfRCiYLWGi1omwKV5erkYLzE469jZdk7b.
According to VirusTotal (VT), it is related to malware, and that malware was labeled as being related to APT10. If you go to the site via that URL path, you will get a generic mail login page.
[Analyst comment: While VT has this specific URI connected to APT10 malware, we were unable to confirm this association at the time of analysis.]

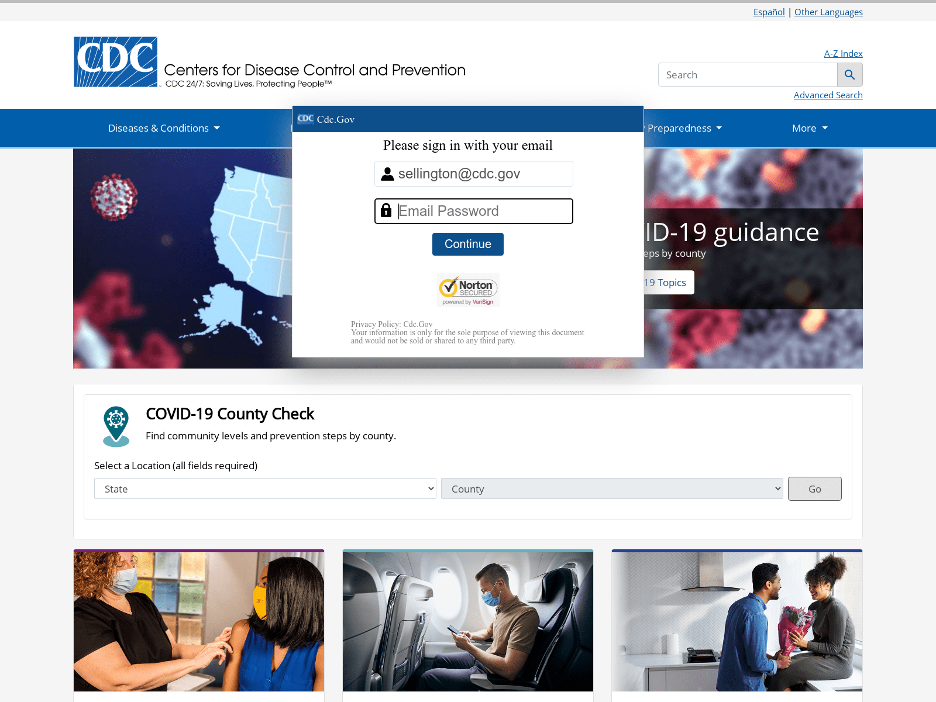
If you go to the same URL path but happen to add #sellington@cdc.gov to the end, you will get a CDC login page.
We also noticed that some of the referring URL paths had emails in them as well. For example, https[://]thulth[.]com/public/css///#[victimname]@henkel.com, which ended on https[://]gateway.pinata[.]cloud/ipfs/Qmdxg94XWxwtZEF7RM712RZL7wW4efBEYNHNMujNiFRyHg/. This was a Microsoft target page.
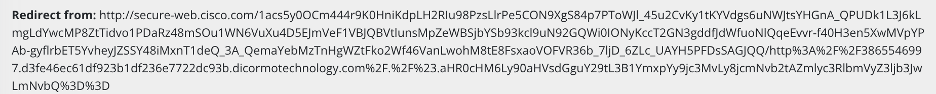
Some other interesting referring URLs linked to sites like Cisco. This open redirect from the Cisco Webex website was mentioned in a blog by Binary Defense. According to the blog, “An open redirect is a technique used to disguise the real destination of a link, abusing a situation in which a website will take any URL as one of the parameters it accepts and forwards the browser to that specified URL.” We can see that happening in this case, with the redirect being another Microsoft target page.
We also saw repeat referring URLs from https[://]thulth[.]com and http[://]go.eu.sparkpostmail1[.]com. Both had Microsoft targets.

If the victim enters their credentials, it will make a post via JavaScript to https[://]ortadogulular[.]com/support/shieldshots.php. This type of activity is considered a Highly Evasive Adaptive Threat (HEAT), a class of cyberthreat that leverages web browsers as the attack vector and employs various techniques, such as this one, to evade multiple layers of detection in security stacks.

We found that most sites on this domain followed that scheme. This BitB attack utilizes Java to post the victim’s credentials. From the analysis of this code, we were able to identify more domains that hosted sites using this technique.
A domain that we found (554325.selcdn[.]ru) from the code analysis is linked to a phishing email with a subject line that says it is a shared folder for the victim’s name. The body of the message directs the victim to click a link for the internal access folder. The link then takes the victim to a BitB phishing site that uses the same JavaScript code to exfiltrate the credentials.
Our original domain gateway.pinata[.]cloud also had some phishing campaigns that asked the victim to log in to view a shared document, much like this phishing site that appears to ask the victim to log in to view an Excel document.

During our analysis period, we also came across a BitB site that appears to still be under construction: https[://]ramiche639.github[.]io/TESTGG will take you to a blank landing page and redirect you to https[://]imaginaryonesmint[.]xyz. This page will load with a BitB window that appears to be a Google login page. However, it was not working properly at the time of analysis and didn’t completely load the phishing page.

BitB attacks will likely continue to increase as threat actors try new ways to trick victims into giving up their credentials. Using multifactor authentication may help increase security when using SSO.
Hash
29bdd8795f985a36c0206bb5a4566cc67be45d5058e758a8e2551da6d7263cf60845204a6d1c75092278d55c76f08346bf4419d04bcba2eee121eb2710fe24a1
Domains
gateway.pinata[.]cloud
https[://]thulth[.]com
http[://]go.eu.sparkpostmail1[.]com
https[://]554325.selcdn[.]ru
https[://]imaginaryonesmint[.]xyz
https[://]ramiche639.github[.]io/TESTGG
rule ajax_post
{
strings:
$a = "ajax"
$b = "dataType"
$c = "JSON"
$d = "url"
$e = "POST"
$f = "ai: ai"
$g = "pr: pr"
$h = "my_slice"
$i = "http:"
$j = "Verifying"
$k = "window.location.replace"
$l = "mgss"
$m = "show"
condition:
all of them
}